QakBot and PikaBot Delivered via Digitally Signed MSI Windows Installers
Recently have been reported some QakBot and PikaBot variants delivered via Windows Installers (.msi files) digitally signed with valid certificates with the intent to bypass antivirus software and application whitelisting software.
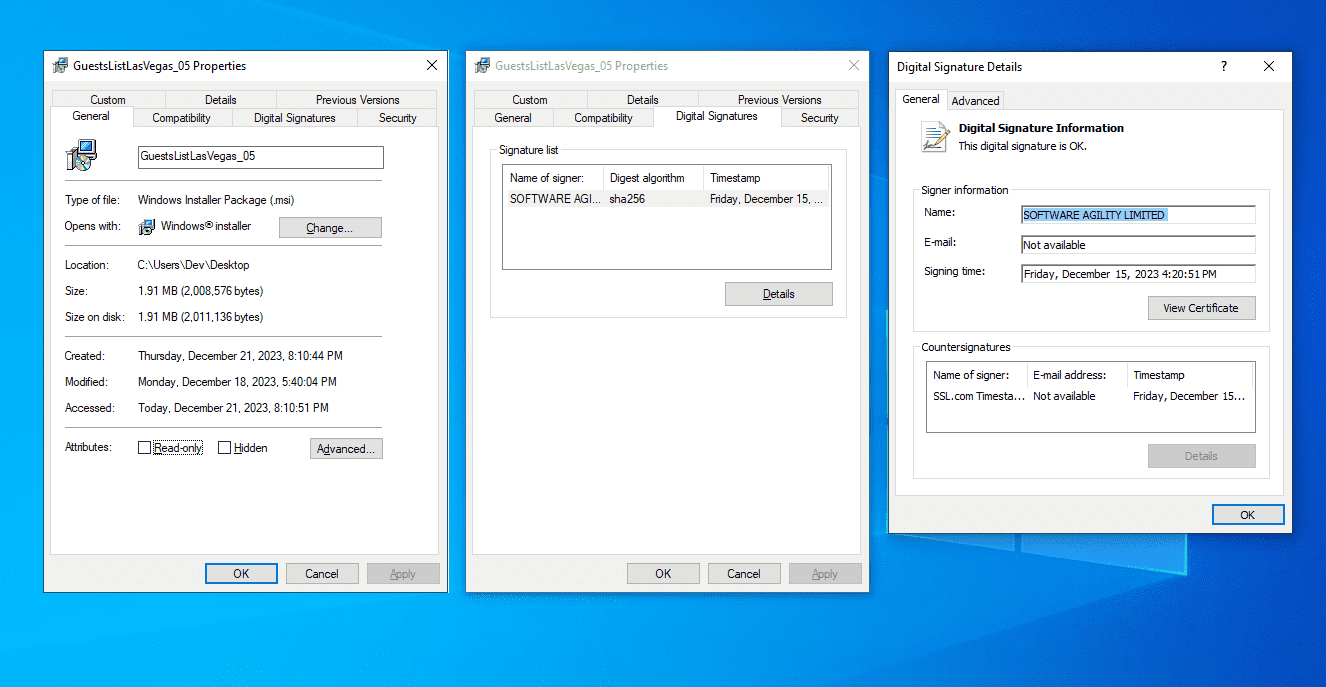
For the case of QakBot, according to Microsoft Threat Intelligence, the first stage of the infection starts with a PDF file delivered via email that contains a link to download the digitally signed Windows Installer file. Once the .msi file is executed, it will drop a malicious DLL file (KROST.dll) on the system and then it will spawn rundll32.exe to load it:
Process: [5820]C:\Windows\SysWOW64\rundll32.exe
Process MD5 Hash: 889B99C52A60DD49227C5E485A016679
Command Line: "C:\Windows\System32\rundll32.exe" C:\Users\user\AppData\Roaming\KROST.dll,hvsi
Parent: [4876]C:\Windows\Installer\MSIB12C.tmp
Parent MD5 Hash: B41E1B0AE2EC215C568C395B0DBB738ARegarding PikaBot, it is promoted via malvertising on Google Ads targeting legit software: if you search for a popular software such as “OBS” or “AnyDesk” you will get on the first search results a (malicious) ad that redirects to a phishing website with the same look as the official website of the searched software. The software downloaded from the malicious website is the fake version of the legit software in Windows Installer (.msi) format. It is becoming common for these malicious .msi files to be signed with a valid digital certificate.
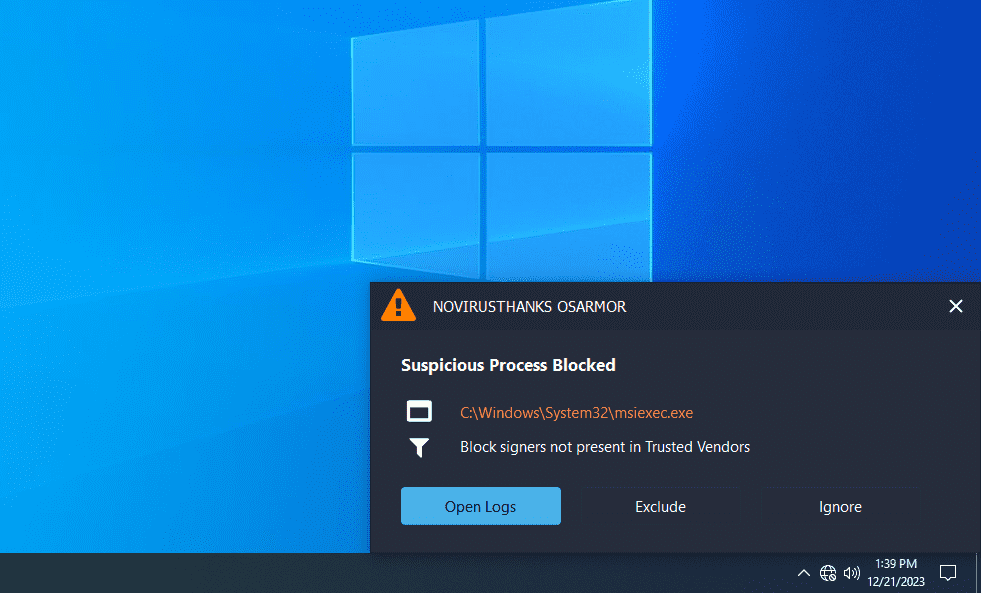
A good way of blocking these kind of threats is to enable in OSArmor the option” Block signers not present in Trusted Vendors” so that if a vendor (company name that digitally signed the executable) is not present in OSArmor’s Trusted Vendors List it will be blocked. Additionally, for extra safety and if you are an advanced user, you can reset the list of trusted vendors to only the ones present in your PC or that you use.
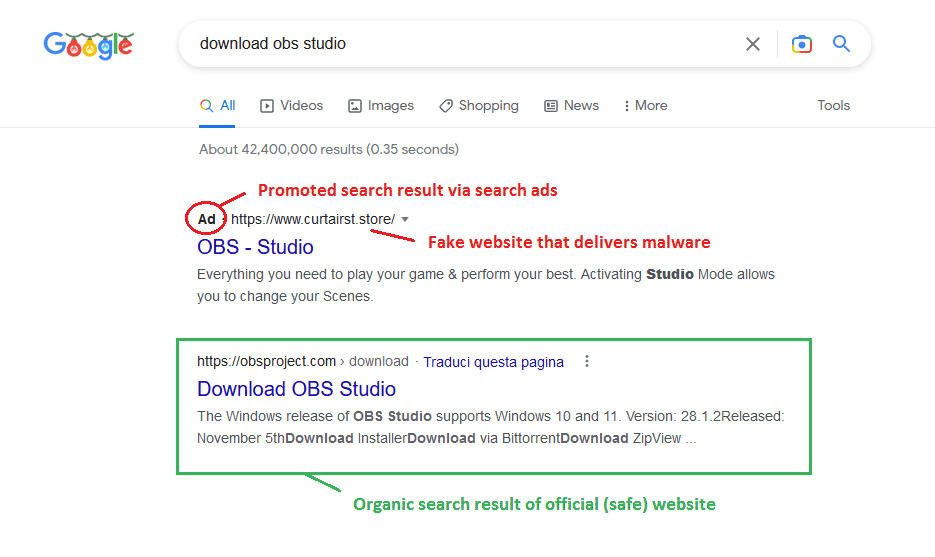
Another good prevention method is to not click on the first Google search results that have the tag “Ad” (which means promoted search result via ads) and instead look for the first organic search result, that generally is the official website of the searched software name:
Here are some indicators of compromise:
GuestsListLasVegas_05.msi
82B8BD90E500FB0BF878D6F430C5ABEC
93A98B919AEC23411AE62DBA8D0D22F939DA45DEC19DB2B4E7293124D8F1507F
B41E1B0AE2EC215C568C395B0DBB738A
A97E782C5612C1A9C8A56C56A943F6190FA7A73C346566860B519EF02EFD0DCA
SOFTWARE AGILITY LIMITED
C:\Users\user\AppData\Roaming\KROST.dll
0A29918110937641BBE4A2D5EE5E4272
780BE7A70CE3567EF268F6C768FC5A3D2510310C603BF481EBFFD65E4FE95FF3Other Interesting Posts
- Typosquatting and Misspelled Domains Leading to Malicious HTA File
- New DLL Search Order Hijacking via System Processes on WinSxS Folder
- Searching a Tutorial on YouTube? Be Aware Where You Click (Malware Alert)
- Fake "Copyright Infringement" Messages Lead to Facebook 2FA Bypass
- How to Digitally Sign Installer and Uninstaller with Inno Setup