Searching a Tutorial on YouTube? Be Aware Where You Click (Malware Alert)
Are you looking for a tutorial on Youtube on how to install a popular Windows software or video game? Pay attention to where you click on the video description or comments, you may get malware or ransomware if you click on the wrong link.
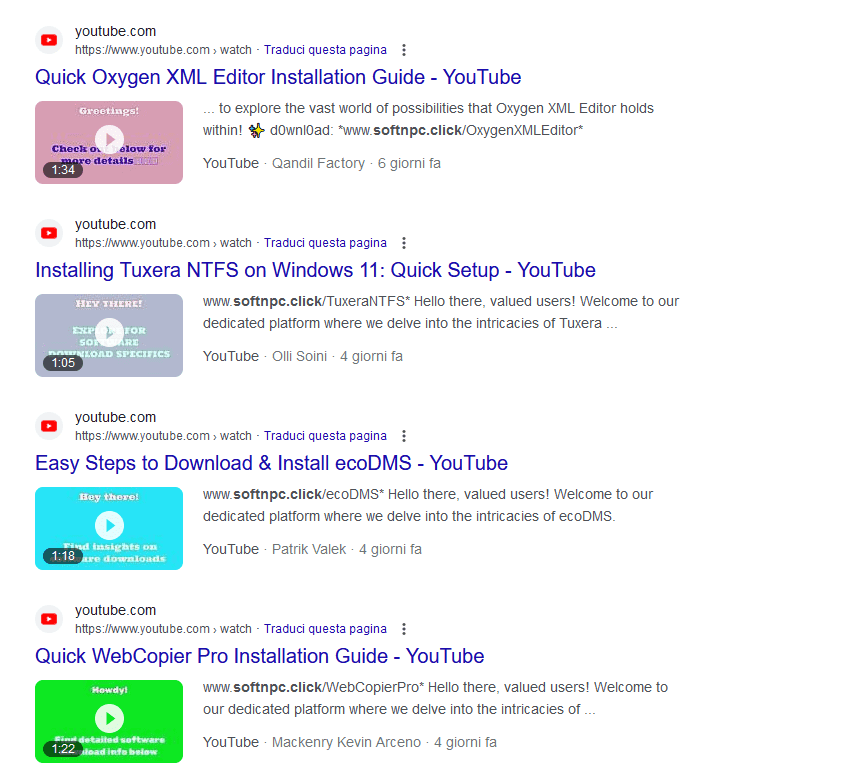
We’ve noticed a massive wave of malicious links present on YouTube videos comments and description that deliver redline information-stealing malware and/or ransomware.
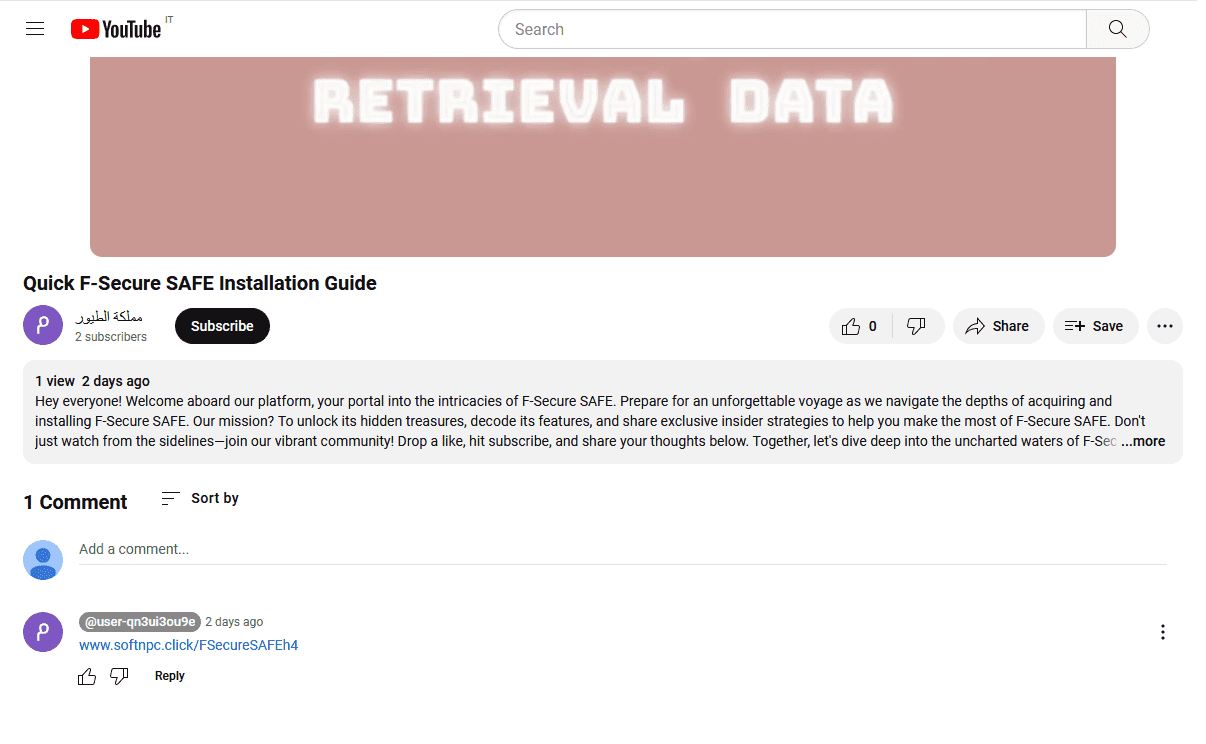
Some of the malicious URLs we have extracted are:
hxxps://www[.]softnpc[.]click/FSecureSAFEh4
hxxps://www[.]mybackposture[.]com/blog/itop-vpn-download
hxxps://www[.]rexcrax[.]org/Dxtoryc5Whois details of the above malicious domains:
Domain Name: softnpc[.]click
Updated Date: 2023-12-24T12:33:22.310Z
Creation Date: 2023-12-19T12:32:38.309Z
Registry Expiry Date: 2024-12-19T12:32:38.309Z
Registrar: HOSTINGER operations, UAB
Registrar IANA ID: 1636
Name Server: bradley.ns.cloudflare.com
Name Server: frida.ns.cloudflare.com
Domain Name: rexcrax[.]org
Updated Date: 2023-12-24T10:34:23Z
Creation Date: 2023-10-30T01:01:04Z
Registry Expiry Date: 2024-10-30T01:01:04Z
Registrar: HOSTINGER operations, UAB
Registrar IANA ID: 1636
Name Server: bradley.ns.cloudflare.com
Name Server: frida.ns.cloudflare.com
Domain Name: mybackposture[.]com
Updated Date: 2023-12-11T19:59:56Z
Creation Date: 2023-05-23T21:22:50Z
Registry Expiry Date: 2024-05-23T21:22:50Z
Registrar: GoDaddy.com, LLC
Registrar IANA ID: 146
Name Server: EZRA.NS.CLOUDFLARE.COM
Name Server: NOLA.NS.CLOUDFLARE.COMHere is a screenshot of the web page that offers the file download:
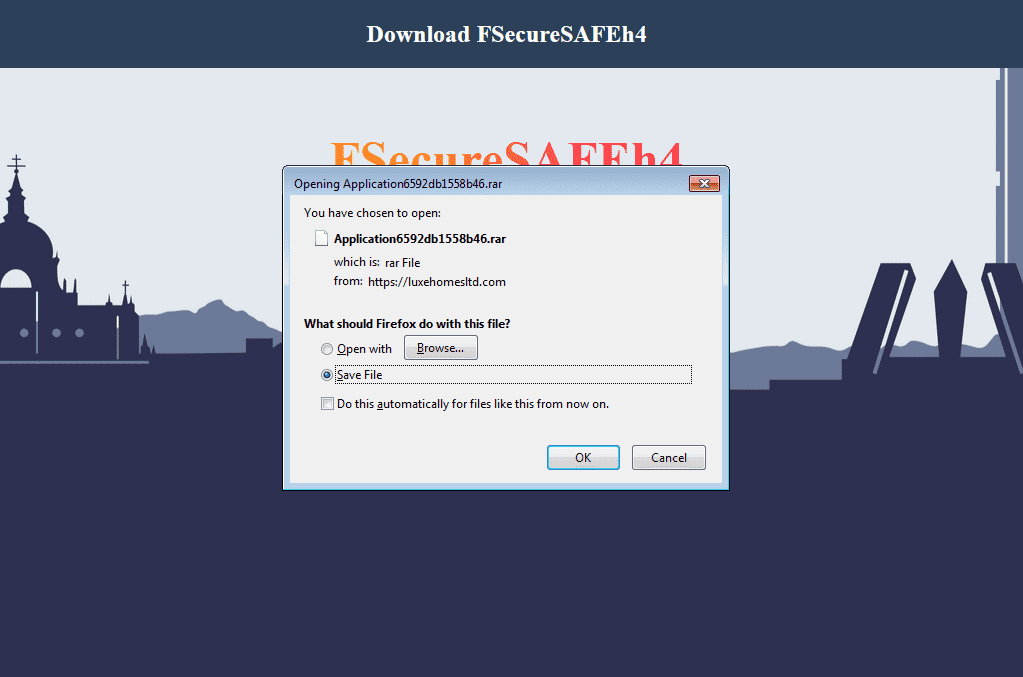
hxxps://luxehomesltd[.]com/soft/
HTTP/2 200
content-type: application/x-rar-compressed
content-disposition: attachment; filename="Application65931be7acbdf.rar"
date: Mon, 01 Jan 2024 20:09:11 GMT
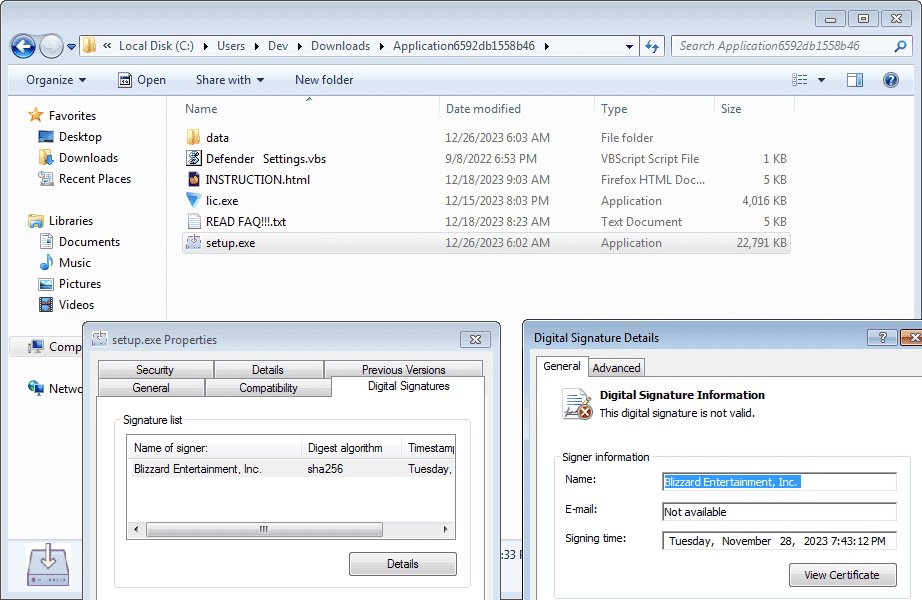
server: LiteSpeedThe downloaded file is a password-protected .rar archive (generally the password is 2023, 2024 or sft111) that contains a “Defender Settings.vbs” file, lic.exe and setup.exe executable files. The setup.exe (or installer.exe) is digitally signed with an invalid signature:
Once executed, the setup.exe file can look like one of these GUIs:
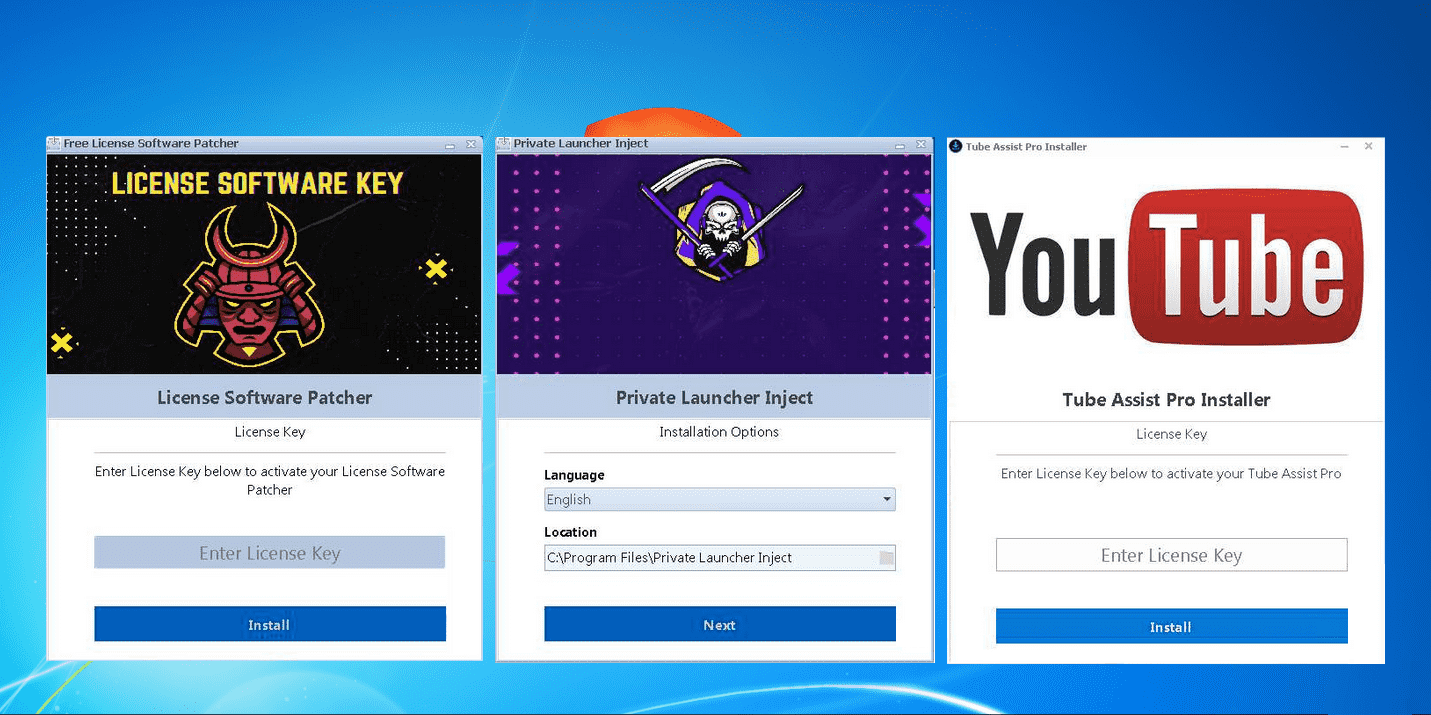
It hiddenly drops and executes an executable file in the system:
C:\INSTALLER\%RANDOMSTRING%.exeThat then spawns and injects code on one of the below processes:
C:\Windows\Microsoft.NET\Framework\v4.0.30319\AppLaunch.exe
C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exeThe above system processes are then used to steal and exfiltrate sensitive data.
The following domains have been contacted during the analysis:
licocojambamarketplace[.]com
selfmicrosoft[.]comThe malware sample seems to not work in virtual machines (as explained in the instructions) and the files INSTRUCTION.html and “READ FAQ!!!.txt” suggest the user to completely disable Windows Defender, other popular antivirus software and the VPN:
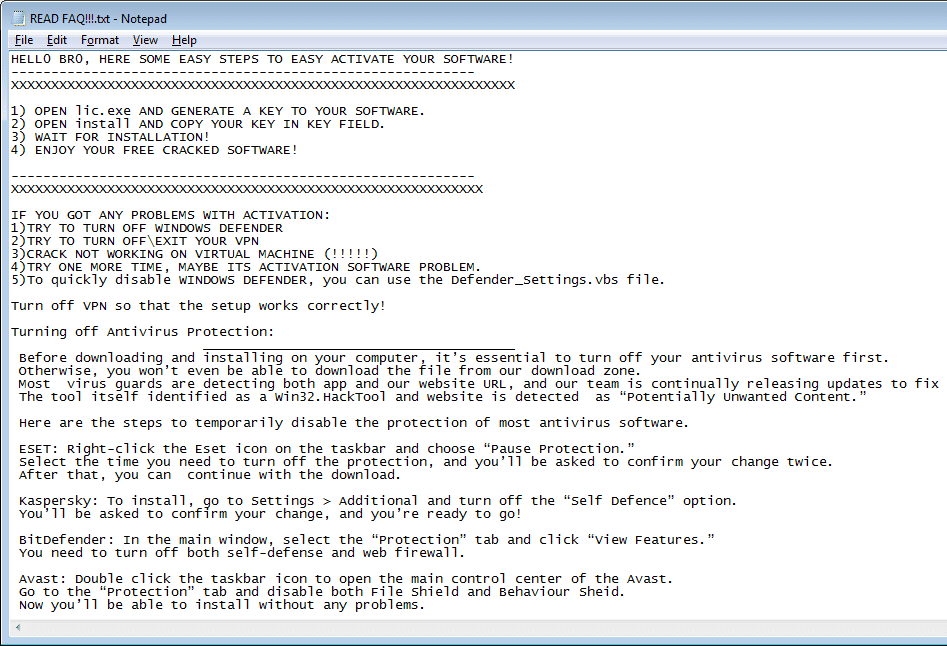
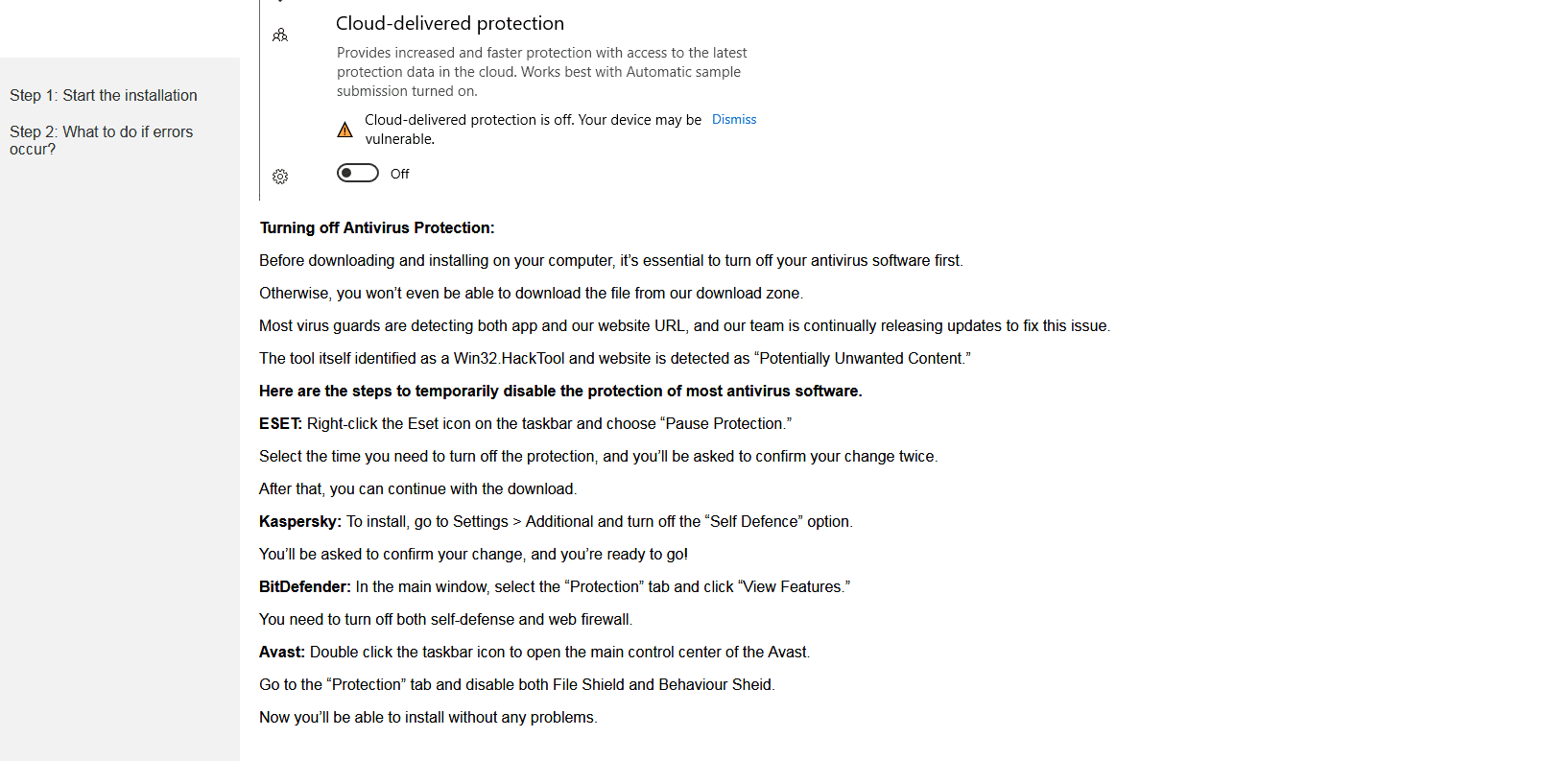
OSArmor blocked execution of both malicious processes:
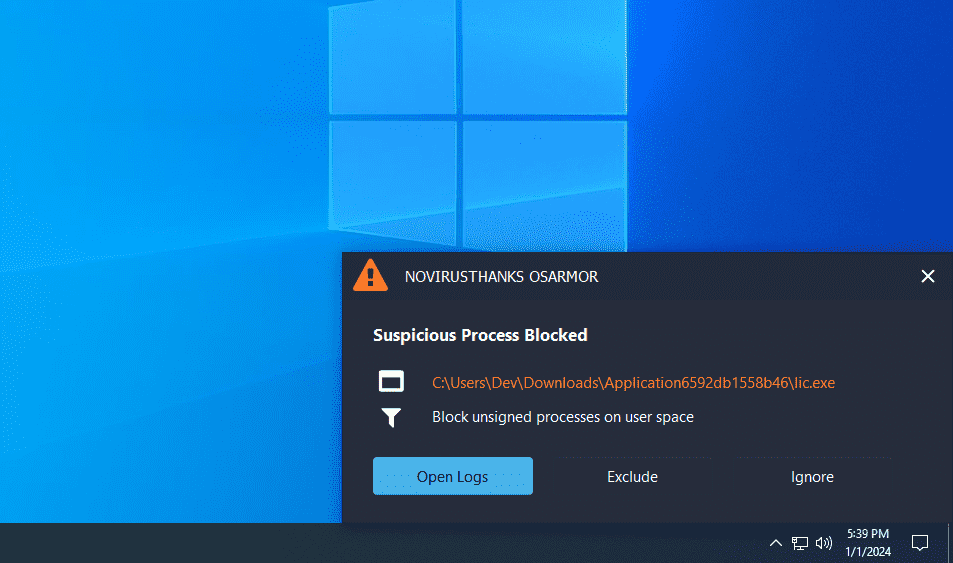
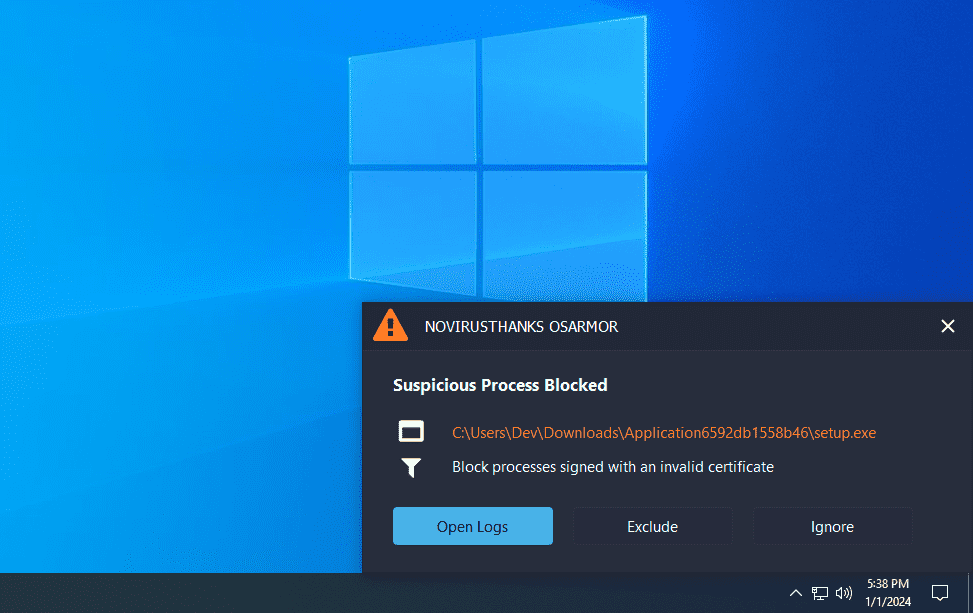
Here are some indicators of compromise:
Application6592db1558b46.rar
c62dd1c9a30b9d17f3976931c7004eac05e6e05af0e8161e976d61902114952f
luxehomesltd[.]com
setup.exe
0a2dd07b4bfdfc08baf51c477423dffaa8672b55e88ba07de92ca6e2ab7884a0
licocojambamarketplace[.]com
selfmicrosoft[.]com
172.67.181.25
104.21.64.104
104.21.89.116
lic.exe
400a80b5166f7ad96f834fecea54ba07244ef90a40a9878ecf843c3e140f304c
C:\INSTALLER\%RANDOMSTRING%.exe
c4a08308d89f79e8c3045309901dc1286b58f70981c9ff2f2ab44a3e2bd231aaSystem processes executed:
C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe
C:\Windows\Microsoft.NET\Framework\v4.0.30319\AppLaunch.exe
"C:\Program Files\Microsoft\Edge\Application\msedge.exe" --single-argument hxxps://www[.]youtube[.]com/watch?v=UZfBnXM8WuYProcesses execution flow (code is injected on AppLaunch.exe):
setup.exe
-- C:\INSTALLER\%RANDOMSTRING%.exe
--- C:\Windows\Microsoft.NET\Framework\v4.0.30319\AppLaunch.exeOther Interesting Posts
- New DLL Search Order Hijacking via System Processes on WinSxS Folder
- QakBot and PikaBot Delivered via Digitally Signed MSI Windows Installers
- Fake "Copyright Infringement" Messages Lead to Facebook 2FA Bypass
- How to Digitally Sign Installer and Uninstaller with Inno Setup
- Google Translate Used in Phishing Attack to Bypass Antispam Filters