Infostealers Distributed Using Cracked Software & Fake Installers
Infostealers are malicious software used to steal important user information such as passwords, credentials, crypto-currency wallets, files, etc. These malicious software are very dangerous and sophisticate and can run totally hidden in the system without letting the user know about their presence. For this reason it is best to prevent their infection than cure, because if it has been successfully installed in the system, most probably it has already stolen and exfiltrated to a remote server the sensitive information.
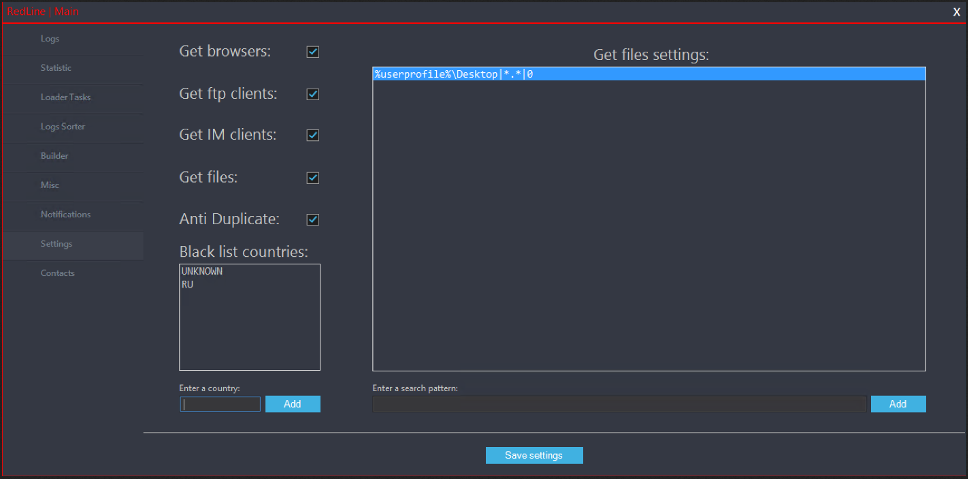
There are many ways that infostealers can infect a system, but generally they are known to spread via cracks or fake software installers of popular Windows software because it is more “easy” to infect the user due to the requested actions by keygens/cracks to, for example, disable the Antivirus software and run the crack with Administrator rights.
How are infostealers commonly installed in the system?
1. Download of Cracks and Pirated Software
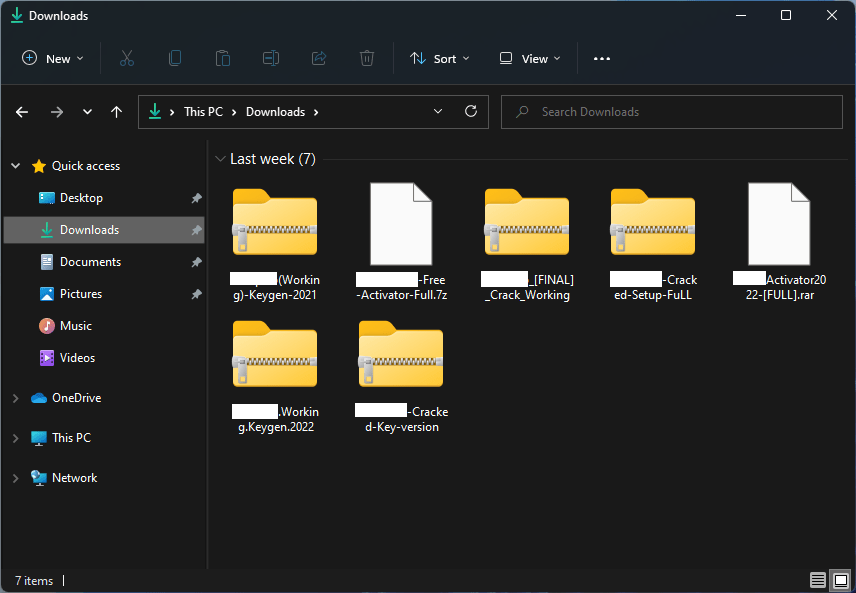
Infostealers (such as RedLine Stealer) are commonly spread via cracks and pirated software, especially because it is known that users are more prone to disable their Antivirus software to run the crack so there is a high chance that the user will get infected. Moreover, many cracks do not immediately run the malicious payload, have been found cracks or keygens that run the payload after a button is clicked, or just before the application is closed.
2. Fake Installers/Setups of Popular Software
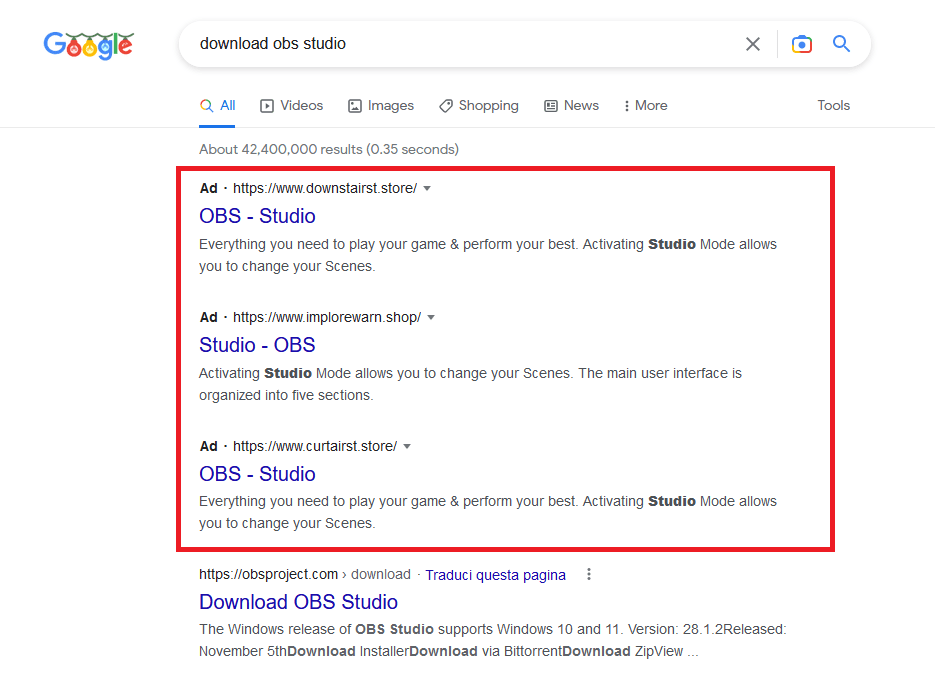
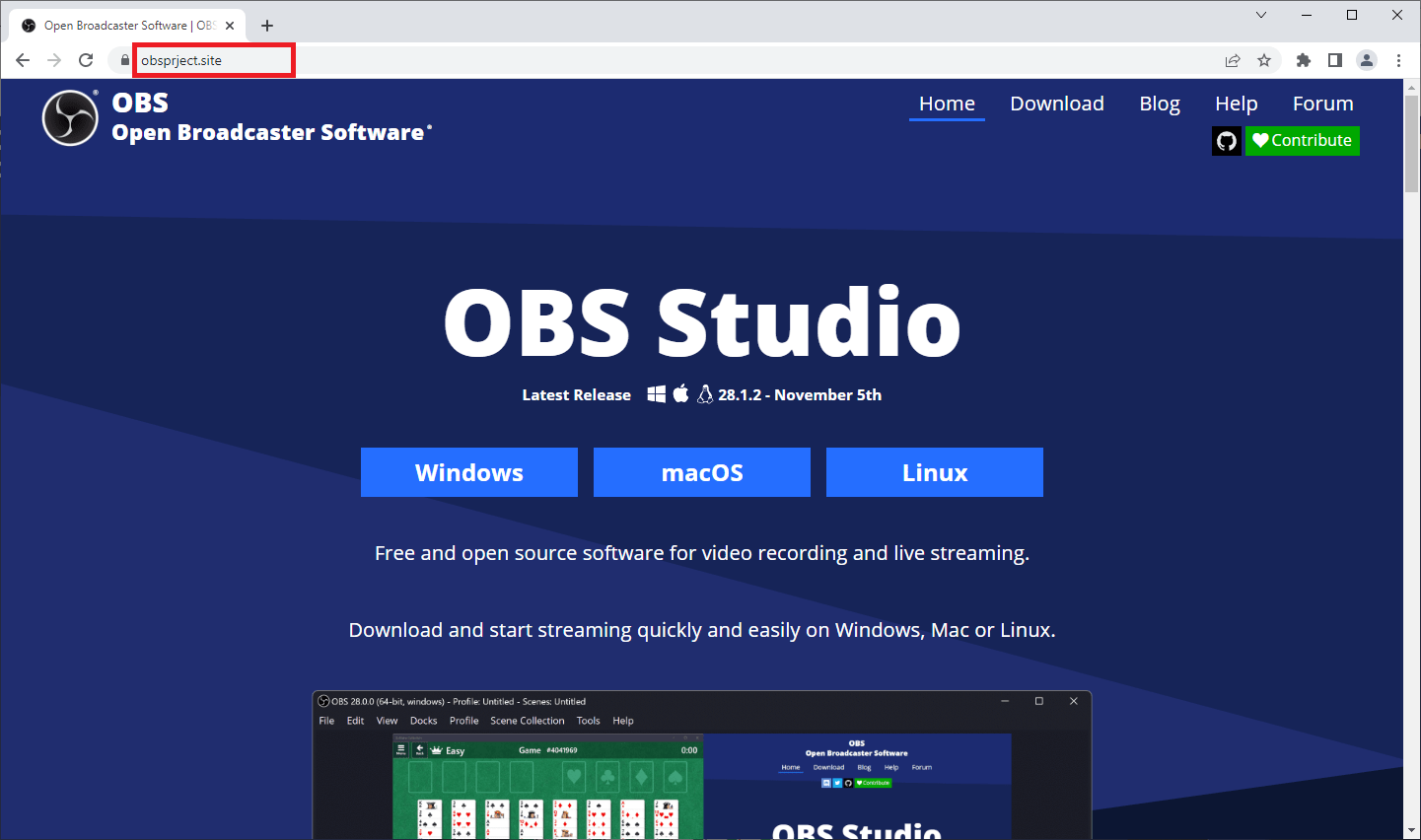
RedLine Stealer is being actively promoted at the moment (November / December 2022) on Google Ads by bidding for keywords related to popular software such as “msi afterburner” or “obs studio”. The fake software websites are found by the user as first entries on the Google search results when searching for the legit software, and once clicked, the user is then redirected to the download of the fake software installer in ZIP or RAR format (that is generally big in file size, like 500+ MB, when extracted).
Fake OBS Studio Websites Advertised on Google Lead to Infostealer
Fake MSI Afterburner Installers Lead to Malware Infostealer
3. Software Downloaded from Unofficial Sources
Any software that is downloaded from unofficial websites (except from legit and well trusted software downloads directories like Softpedia or Majorgeeks) may have been altered or somehow “repackaged” with potentially malicious software or scripts and thus increase the risk of getting infected by these information stealers. In the past many popular free and/or open-source software such as VLC, Notepad++, Irfan View, 7-Zip, Libre Office and even Windows Updates have been “rebuilt” to install also malware infostealers.
Malicious Notepad++ installers push StrongPity malware
Fake Windows 11 upgrade installers infect you with RedLine malware
Weaponizing Open Source Software for Targeted Attacks
4. Malicious Links on Youtube Video/Comments
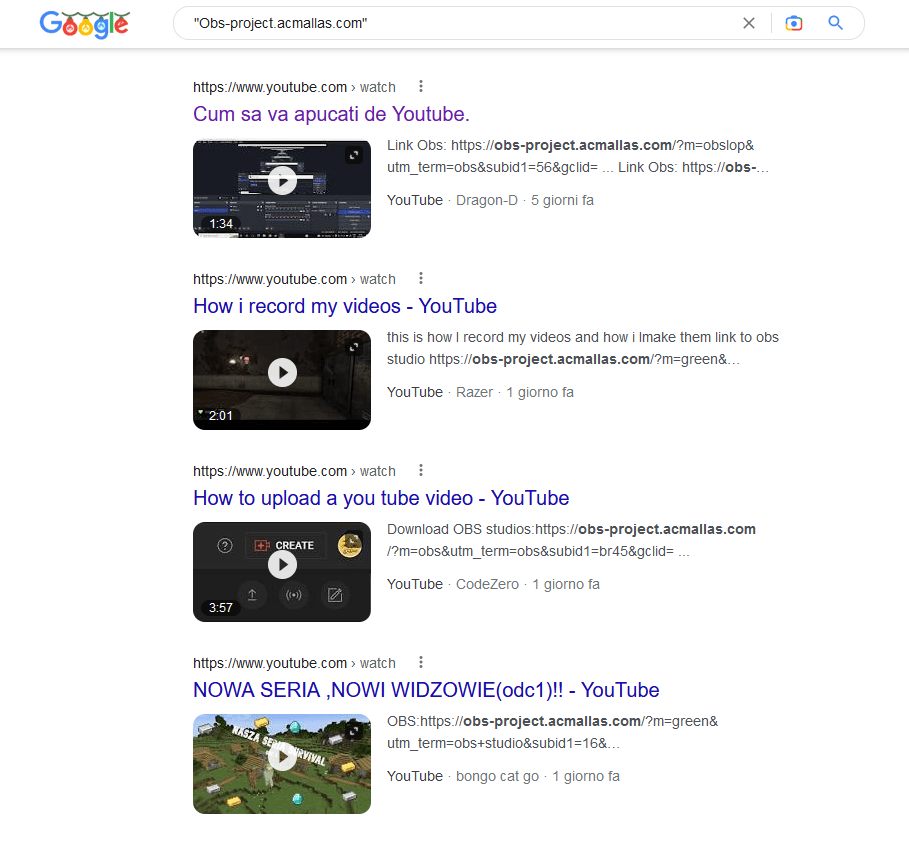
Fake software installers and software cracks are promoted also on comments of YouTube videos and/or on the description of the video. The video is also used to “instruct” the user to disable the Antivirus software before run the fake installer or software crack, and there may also be fake positive comments on the video that thanks the author of the video for providing a “working method” to perform the specified task as per shown in the video, and thus fool the user to download and run the malicious executable file.
5. Download Links Found on Email Messages
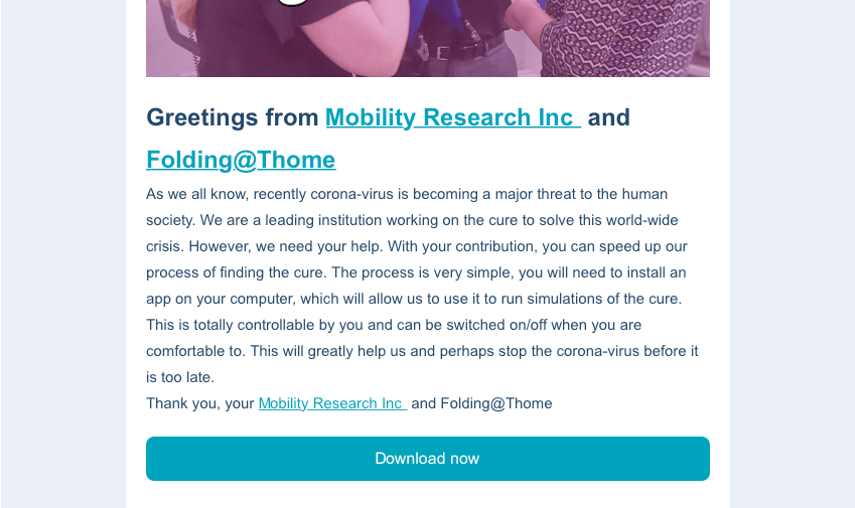
Image taken from: Proofpoint
Have been reported cases, for example during the coronavirus pandemic, that infostealers tried to spread via email messages containing “Download Now” buttons and asking the user to download and install a specific application to get news about the coronavirus. Or another example is when the user is asked on a email message to install the update of a software (that may be effectively installed in the user’s system) to upgrade a specific application.
Redline Stealer Distributed Using Coronavirus-themed Email Campaign
Recommendations to Avoid Infostealer Infections
- Download software from official websites
- Do not use cracks/keygens and cracked software
- When searching for something check always the domain name
- Always check who is the sender of an email message
- Do not click on links found on suspicious or uncommon emails
- Scan the website/link on URLVoid and VirusTotal to check its safety
- Check if the installer is digitally signed with a valid certificate
- If possible try to avoid software that are unsigned
- Upload the installer file on VirusTotal to check detection rate
- Block unknown and unsigned applications on user space
- Use multiple protection layers (very important)
Speaking of additional layers of protection, you can utilize NoVirusThanks OSArmor to easily [1] block unsigned processes on user space and [2] block unknown signers not present in the Trusted Vendors List (these two protection options are unchecked by default, you will need to enable them). This will make sure that when an user runs an unknown or unsigned application, it will be blocked. Same will happen in case the user will run an installer or application signed by an unknown vendor not present in your list of trusted and known vendors (you can fully edit the Trusted Vendors List on OSArmor as per your needs).
But the user can still disable the security software… To prevent an user from disabling the Antivirus or other security software just make sure to use a Standard User Account and to password-protect the power options of all the security software you have installed, so the user will be unable to disable them. These additional protection measures will participate together in preventing an infection by infostealers and other malware.
Other Interesting Posts
- Typosquatting and Misspelled Domains Leading to Malicious HTA File
- New DLL Search Order Hijacking via System Processes on WinSxS Folder
- Searching a Tutorial on YouTube? Be Aware Where You Click (Malware Alert)
- QakBot and PikaBot Delivered via Digitally Signed MSI Windows Installers
- Fake "Copyright Infringement" Messages Lead to Facebook 2FA Bypass