New DLL Search Order Hijacking via System Processes on WinSxS Folder
Recently security researchers from Security Joes have reported a new variant of DLL search order hijacking technique that affects system processes located in WinSxS folder.
Here is a screenshot of a sample PoC that uses PowerShell:
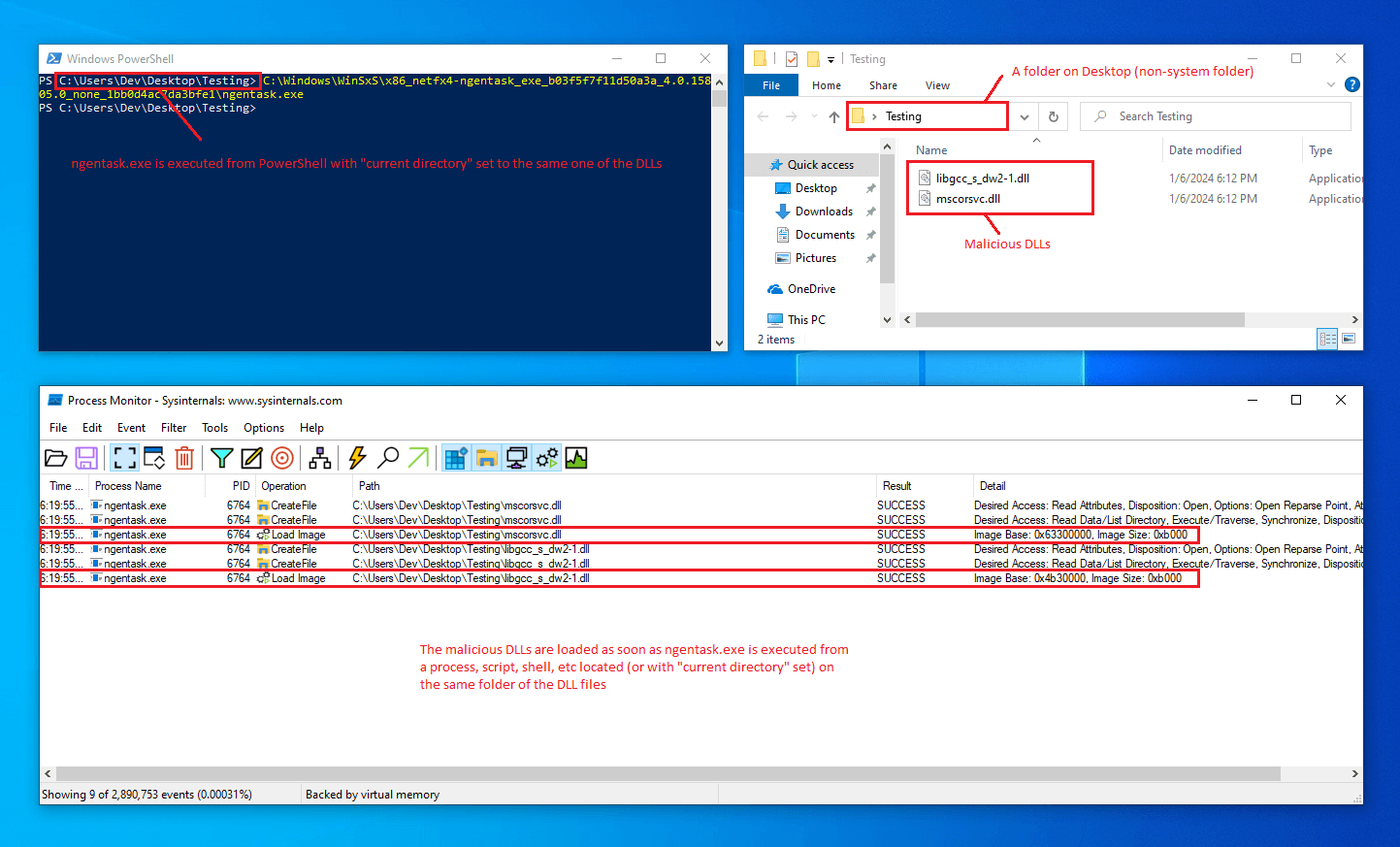
Basically, if a process located in WinSxS folder (such as ngentask.exe) is executed from a process, script, shell, etc located in another folder, such as from C:\Users\Dev\Desktop\Testing\, then ngentask.exe will check for the presence of some DLLs (such as mscorsvc.dll) on the same folder of the caller process and if they are found they are loaded in the system via classic DLL search order hijacking technique.
On Windows 10 21H1 the process ngentask.exe will check for and load also another DLL named libgcc_s_dw2-1.dll, and there may be possibly more on other Windows 10 or 11 versions. Other processes located in the WinSxS folder such as cvtres.exe, csc.exe, ngen.exe may be affected by this behavior, and the interesting point here is also that it is not needed to copy the ngentask.exe on the non-system folder, it just needs to be executed from a process that is already on the actor-controlled folder to load the malicious DLL.
Sample PoC Simulating a Real-World Attack
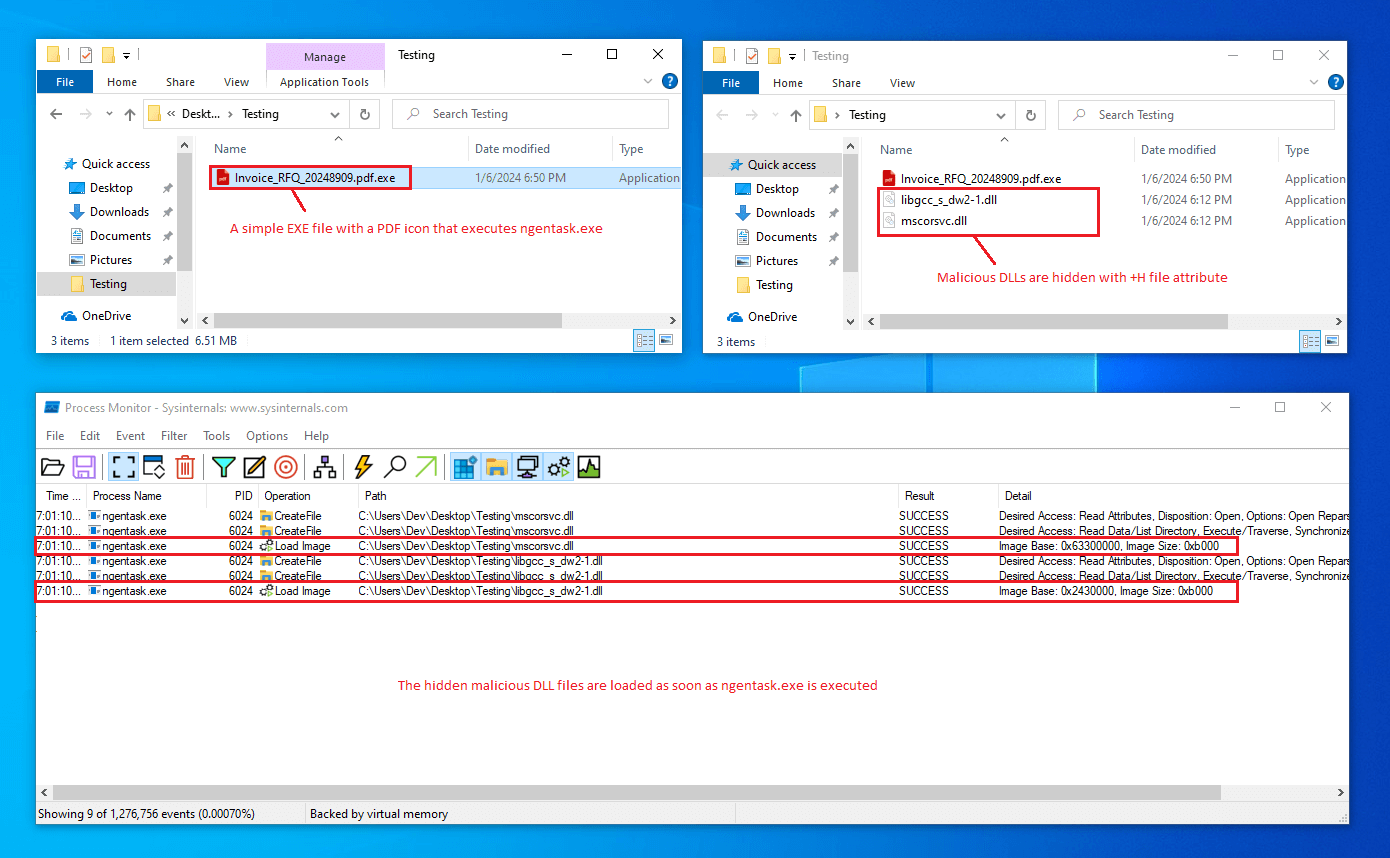
We may see soon some malware variants potentially use this new technique to load a malicious DLL file in the system and bypass security solutions. Lets do a quick real-world attack test with a simple EXE loader masked as a PDF file (icon plus double file extension) and with the two malicious DLLs hidden with the +H file attribute: as soon as the fake PDF file (exe) is executed it starts ngentask.exe and the malicious DLLs are loaded in the system:
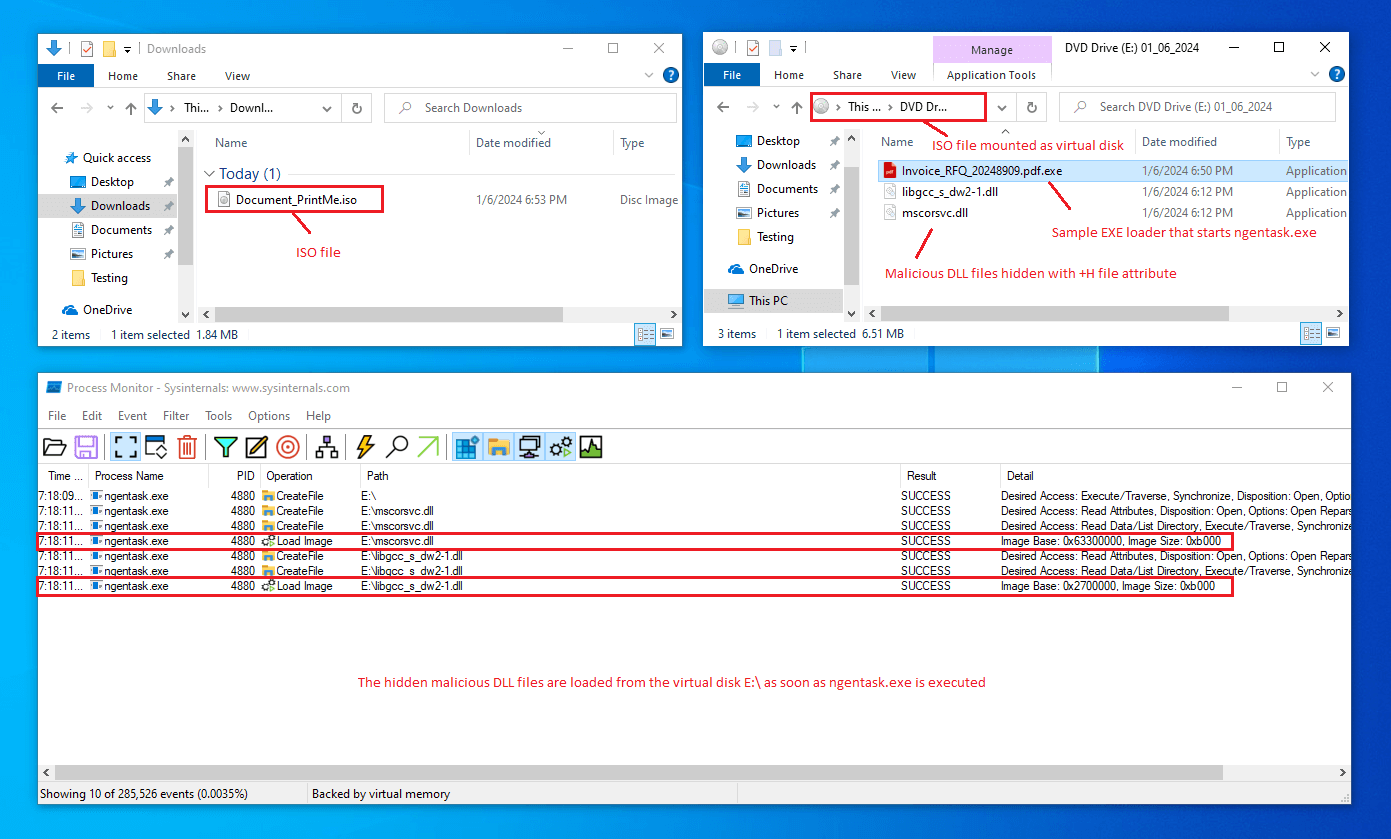
Here is another real-world attack test that uses a ISO file (a common technique used in recent targeted attacks) that contains an EXE loader masked as a PDF document file and the two malicious DLLs hidden with +H file attribute: as soon as the ngentask.exe is executed from the fake PDF file (exe) the malicious DLL files are loaded in the system:
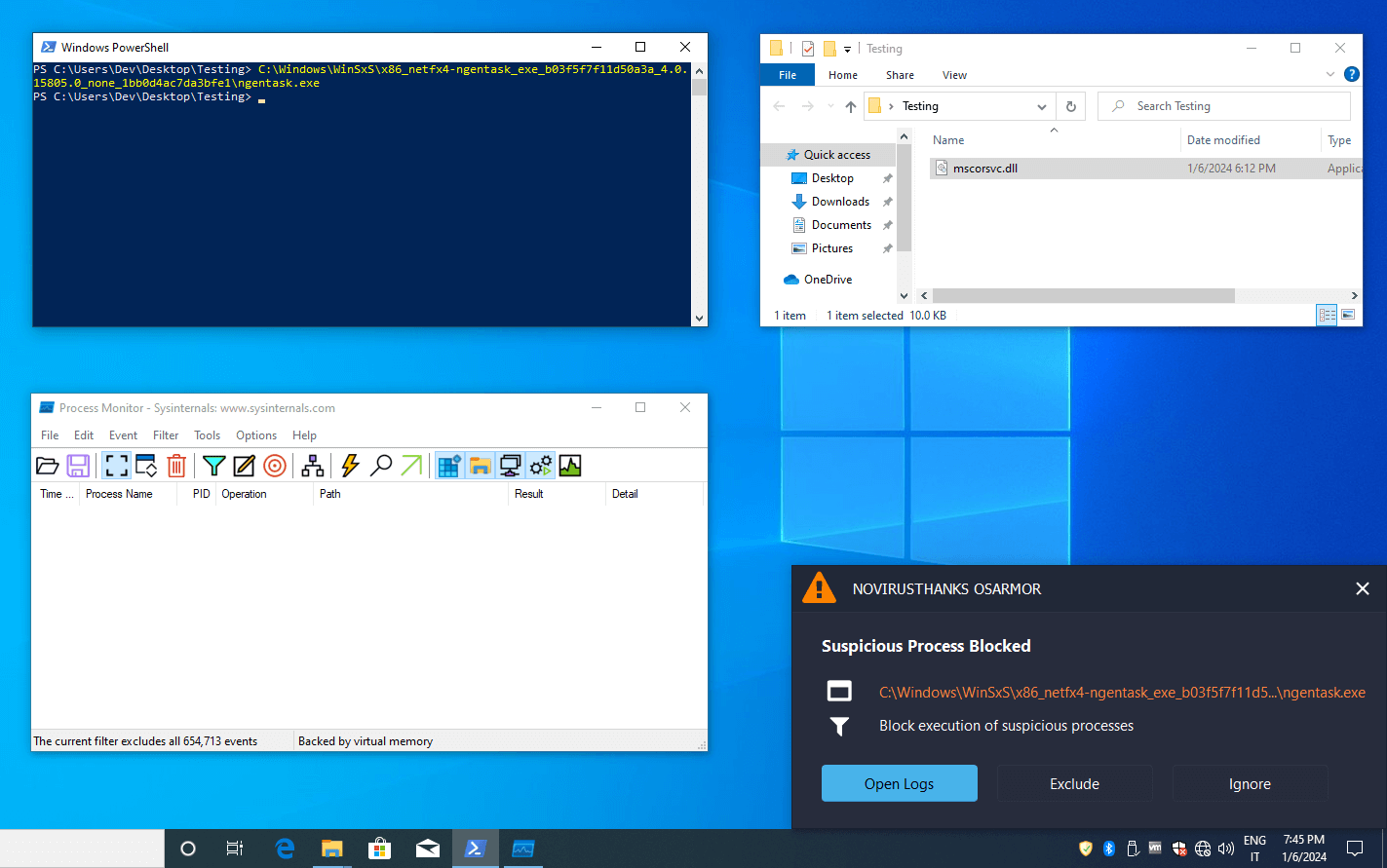
OSArmor with Basic Protection Profile can block this behavior:
A good rule is to monitor for processes executed on WinSxS folder:
C:\WINDOWS\WinSxS\Other Interesting Posts
- Typosquatting and Misspelled Domains Leading to Malicious HTA File
- Searching a Tutorial on YouTube? Be Aware Where You Click (Malware Alert)
- QakBot and PikaBot Delivered via Digitally Signed MSI Windows Installers
- Fake "Copyright Infringement" Messages Lead to Facebook 2FA Bypass
- How to Digitally Sign Installer and Uninstaller with Inno Setup