Windows Tool WerFault.exe Abused to Sideload Malicious DLL
There is a new ISO file named “recent inventory& our specialties.iso” in-the-wild that is delivered via email as attachment and that uses a DLL sideloading technique to load a malicious DLL file in the user’s system. The Windows system process that is abused to sideload the malicious DLL is WerFault.exe (Windows Problem Reporting), that is a legit Windows system process and is digitally signed by Microsoft Windows.
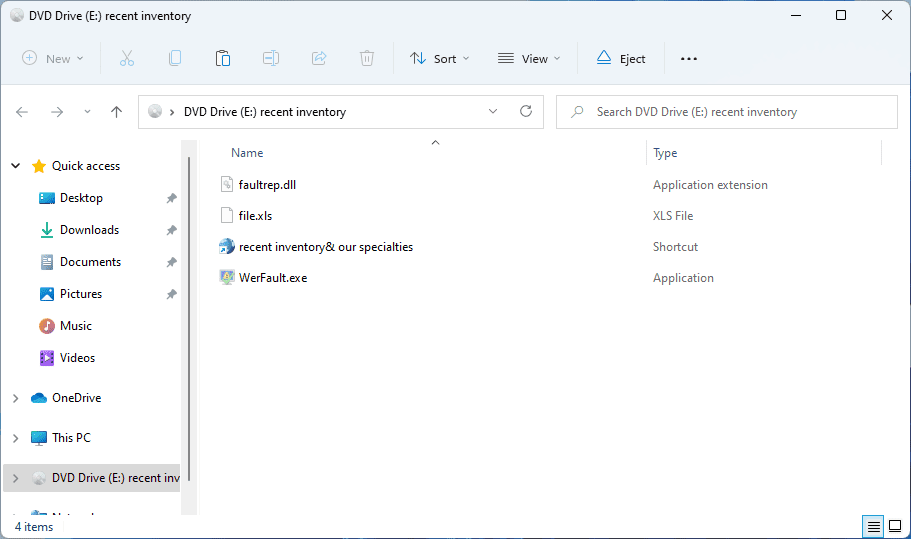
When double-clicked, the ISO file will be automatically mounted as a new drive and it will show to the user its content, all files are hidden to the user except the LNK shortcut file. When the malicious LNK file is double-clicked, it spawns an instance of the system process scriptrunner.exe with a specific parameter that is used to execute WerFault.exe:
C:\Windows\System32\ScriptRunner.exe -appvscript WerFault.exeThen, when WerFault.exe is executed, it will silently load the malicious DLL file faultrep.dll, located in the same folder, and the system will be compromised. The loaded DLL file can then perform any kind of malicious activity, such as download a remote executable and run it, or capture user’s credentials and send them to a remote server, etc. For this reason it is better to prevent that the malicious DLL file (in this case faultrep.dll) is loaded in the system.
NoVirusThanks OSArmor blocks the malicious behavior at the begin:
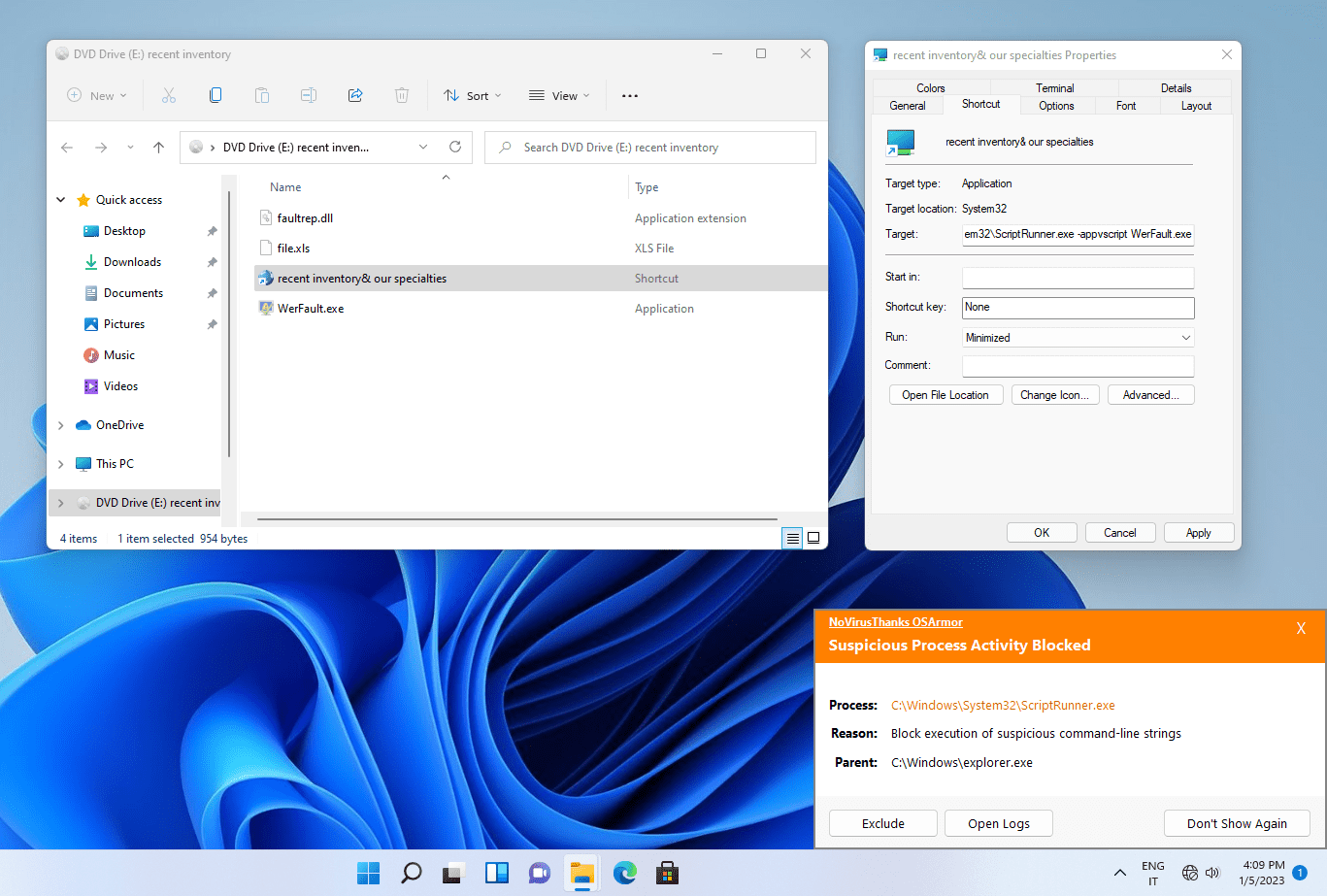
Thus the infection chain has been stopped and the system is safe.
References:
https://twitter.com/SBousseaden/status/1603425101528956935
Hackers abuse Windows error reporting tool to deploy malware
Pupy RAT hiding under WerFault’s cover
Other Interesting Posts
- New DLL Search Order Hijacking via System Processes on WinSxS Folder
- Searching a Tutorial on YouTube? Be Aware Where You Click (Malware Alert)
- QakBot and PikaBot Delivered via Digitally Signed MSI Windows Installers
- Fake "Copyright Infringement" Messages Lead to Facebook 2FA Bypass
- How to Digitally Sign Installer and Uninstaller with Inno Setup