LMIGuardianSvc.exe (LogMeIn) Abused to Sideload Malicious DLL
An user sent us an interesting malicious ISO file that contains a LNK shortcut and a “System Volume Information” folder (that is hidden to the user, only the LNK file is visible). The folder has an icon similar to the Windows File History, here is the ISO file content:
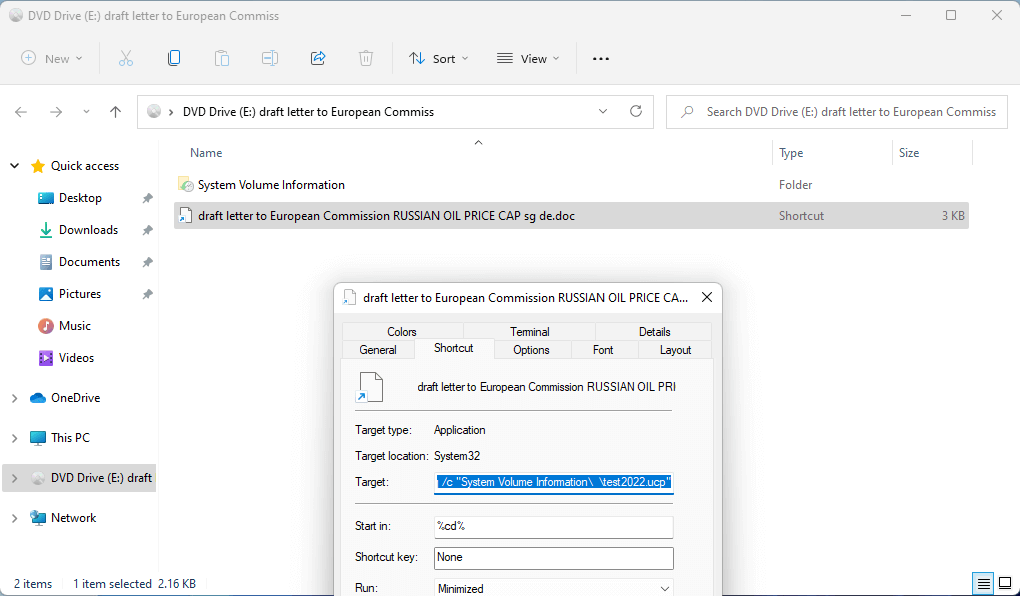
The LNK shortcut file uses cmd.exe to execute the “test2022.ucp” file:
C:\Windows\System32\cmd.exe /q /c "System Volume Information\ \test2022.ucp"“System Volume Information” is a folder but once clicked, it opens File History:
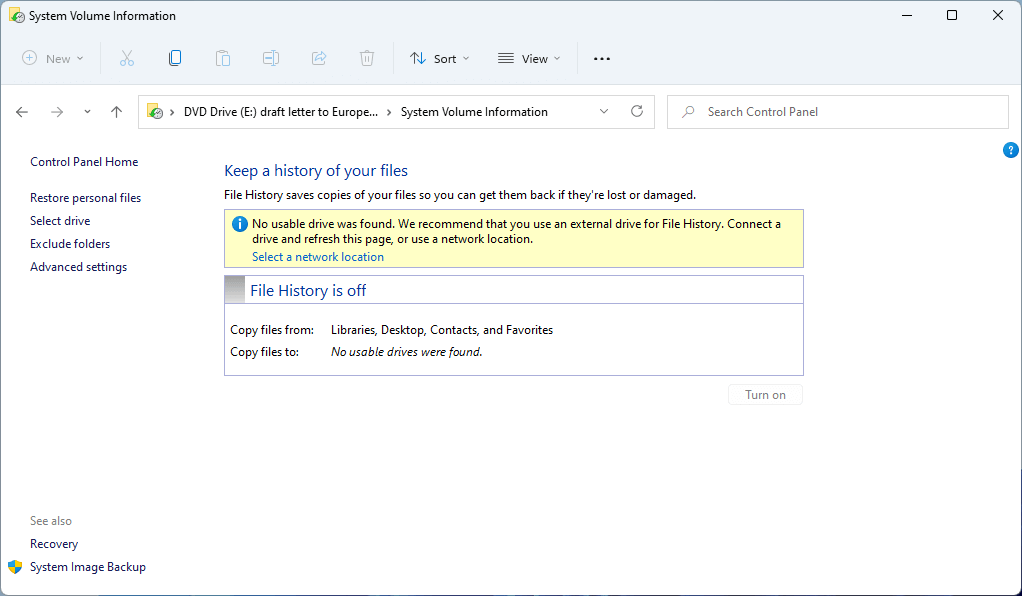
Lets try to open the folder with Windows Command Prompt (cmd.exe):
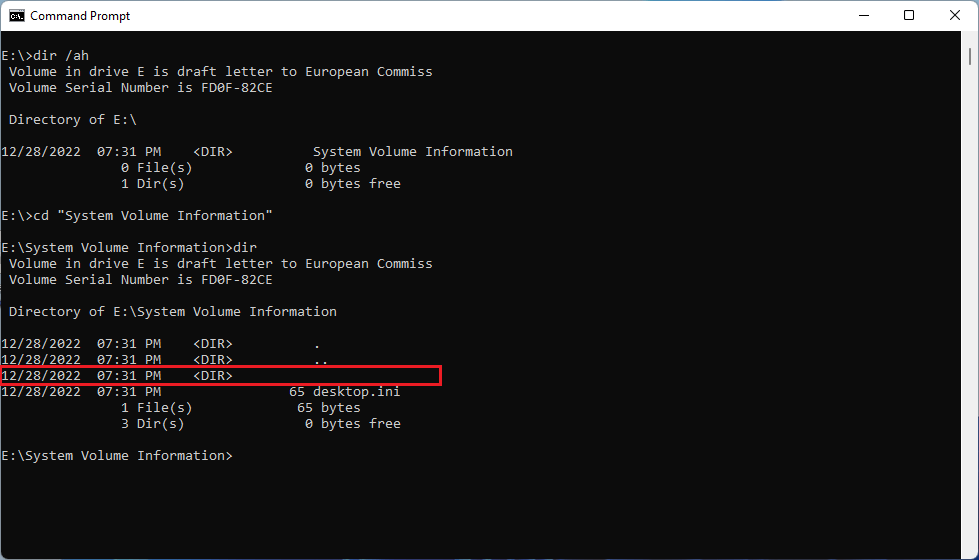
It can be opened and you can see from the above image that there is a folder with a “blank” name, lets try to open the ISO file with 7zip to open the “blank”-named folder:
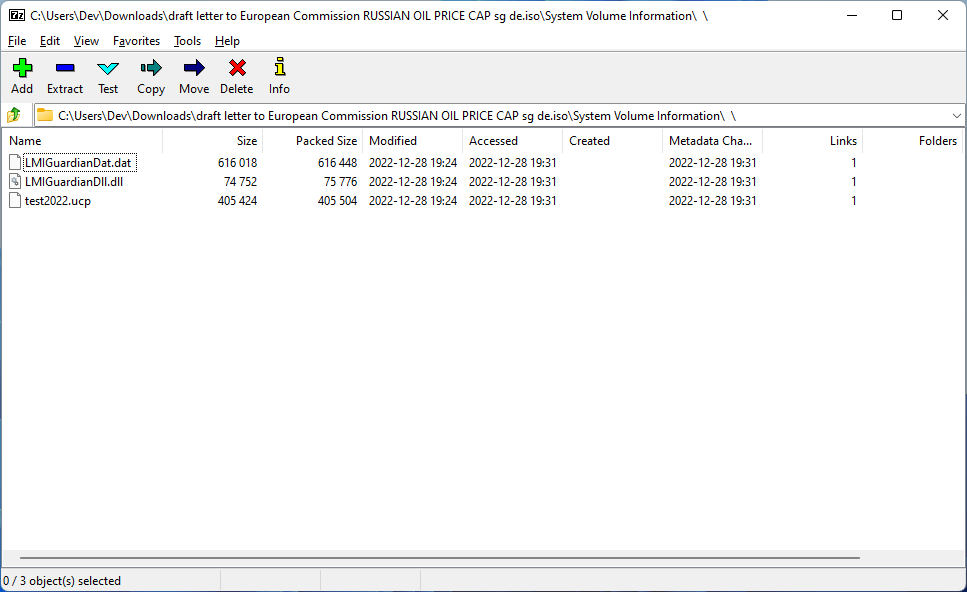
There are 3 files inside the “blank”-named folder:
File: LMIGuardianDat.dat
File size: 602 KB (616.018 bytes)
MD5 checksum: 64796C7C87D04821ADBED23B10DF1561
SHA1 checksum: A6DC882F68068E1A5EB82CB1A721341F835EF93C
SHA256 checksum: 8C4926DD32204B6A666B274A78CCFB16FE84BBD7D6BC218A5310970C4C5D9450
File: LMIGuardianDll.dll
File size: 73,0 KB (74.752 bytes)
MD5 checksum: 1338724BAEC048F600ED982AD811ECF0
SHA1 checksum: 7CBF6CB53214F11904E63BB7493999A3B2E88B62
SHA256 checksum: EE2C8909089F53AAFC421D9853C01856B0A9015EBA12AA0382E98417D28AEF3F
File: test2022.ucp
File size: 396 KB (405.424 bytes)
MD5 checksum: 93A4E2B886E2815B6B732A2380B0F068
SHA1 checksum: 5CBFA13B74917AABBFB4D714C53AFB1AC20B10E6
SHA256 checksum: 26C855264896DB95ED46E502F2D318E5F2AD25B59BDC47BD7FFE92646102AE0DThe file test2022.ucp is the file that is executed from the LNK shortcut:
C:\Windows\System32\cmd.exe /q /c "System Volume Information\ \test2022.ucp"It is a legit executable (original name LMIGuardianSvc.exe) signed by LogMeIn:
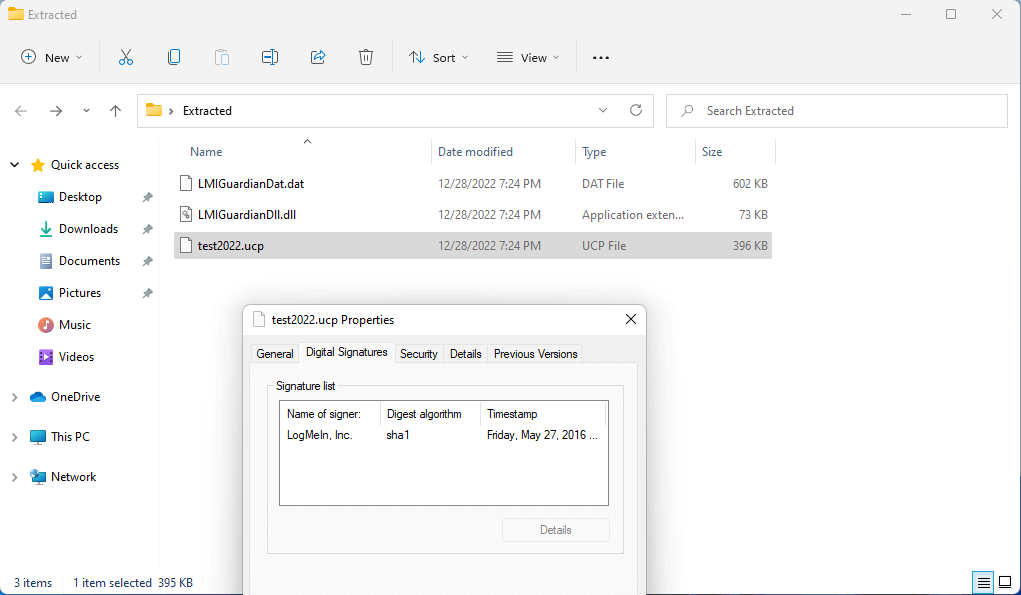
It is clear that LMIGuardianDll.dll is the malicious DLL that will be loaded via DLL sideloading technique by the legit LogMeIn executable LMIGuardianSvc.exe (that has been renamed to test2022.ucp) when it is executed from the LNK shortcut file.
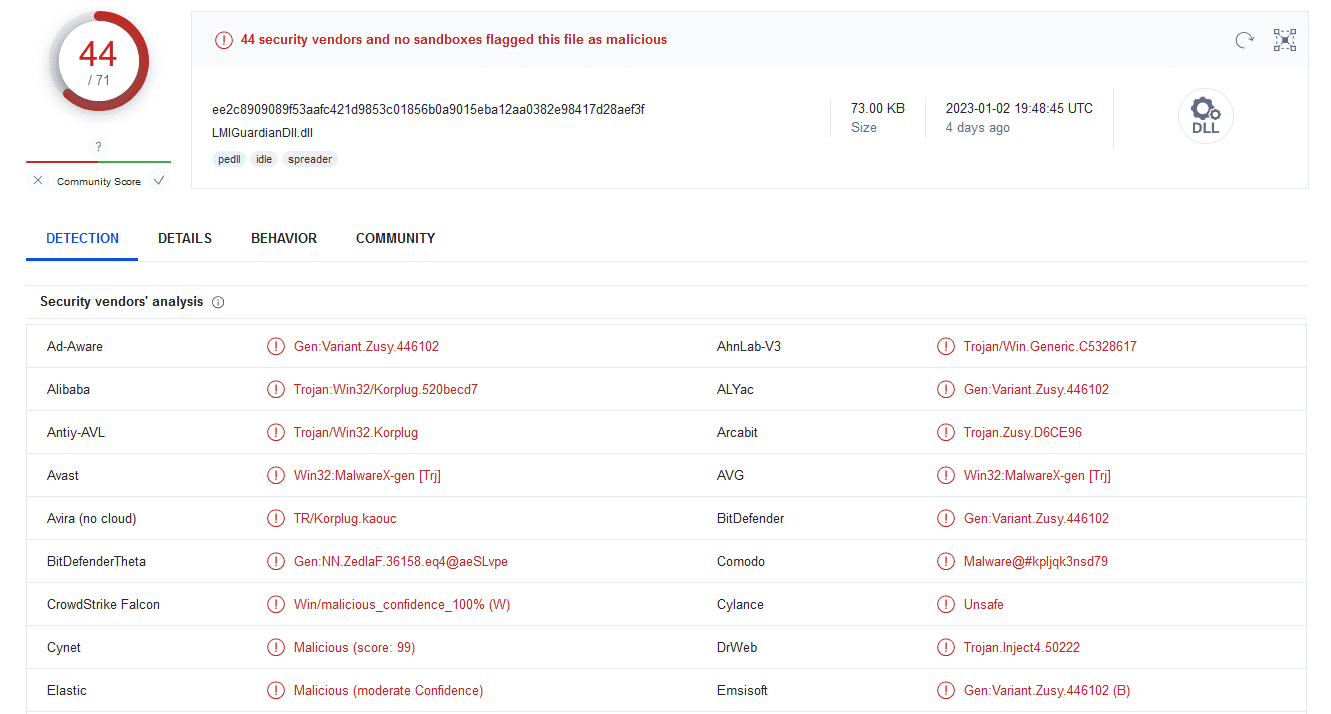
Here is the VirusTotal report of LMIGuardianDll.dll (Korplug RAT aka PlugX):
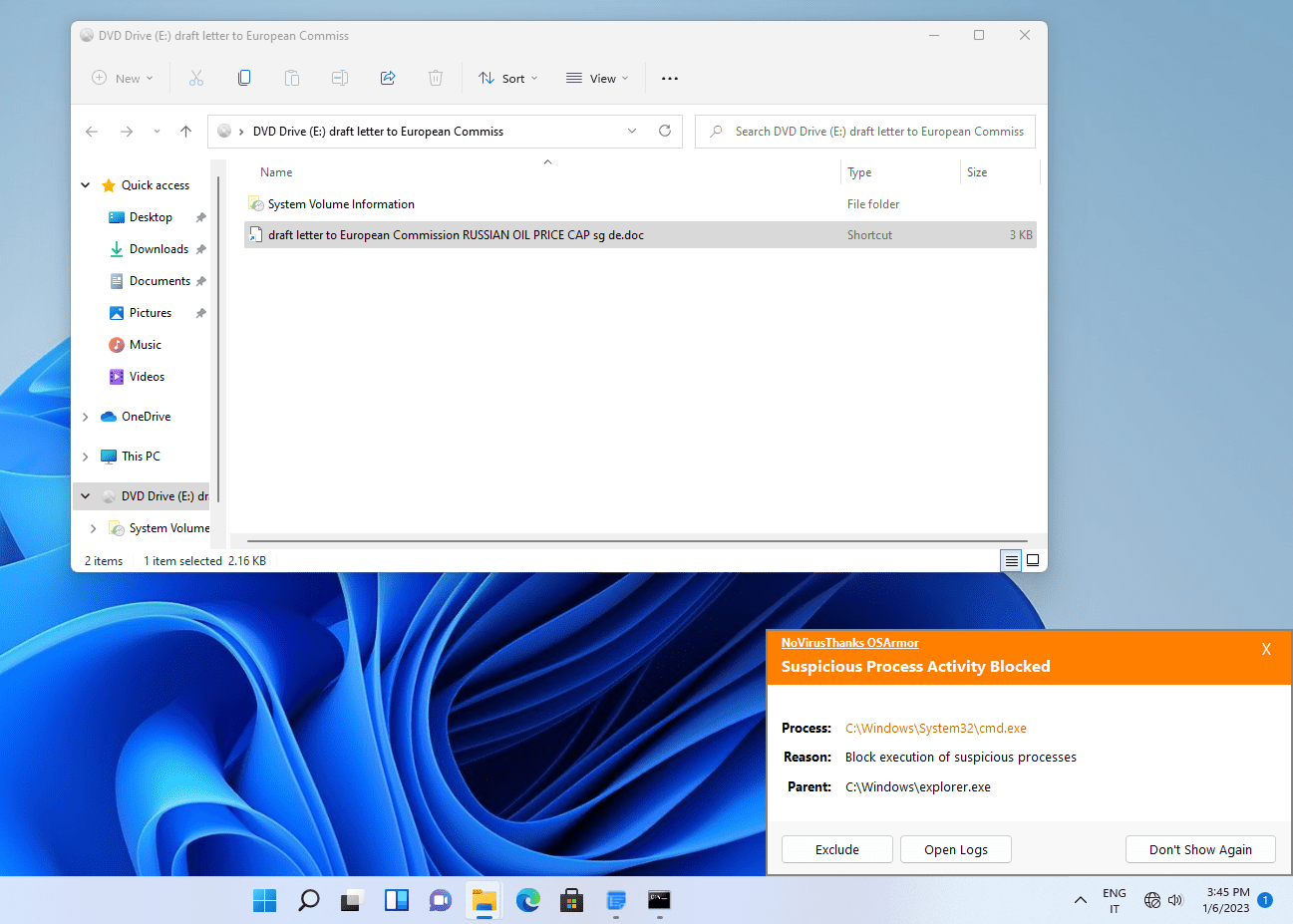
NoVirusThanks OSArmor blocked the infection chain at the begin:
Other Interesting Posts
- Typosquatting and Misspelled Domains Leading to Malicious HTA File
- New DLL Search Order Hijacking via System Processes on WinSxS Folder
- Searching a Tutorial on YouTube? Be Aware Where You Click (Malware Alert)
- QakBot and PikaBot Delivered via Digitally Signed MSI Windows Installers
- Fake "Copyright Infringement" Messages Lead to Facebook 2FA Bypass