Not Just OneNote, Also Microsoft Publisher Maldocs can Deliver Malware
A few weeks ago we discussed about malicious OneNote documents used to deliver AsyncRAT (that now are being utilized also by Qakbot), but the same can happen with Microsoft Publisher (.pub file extension) malicious documents. To date we have found only a very few Microsoft Publisher maldocs samples, however this doesn’t mean they will not be used soon as an alternative to the common Word, Excel and more recent OneNote maldocs.
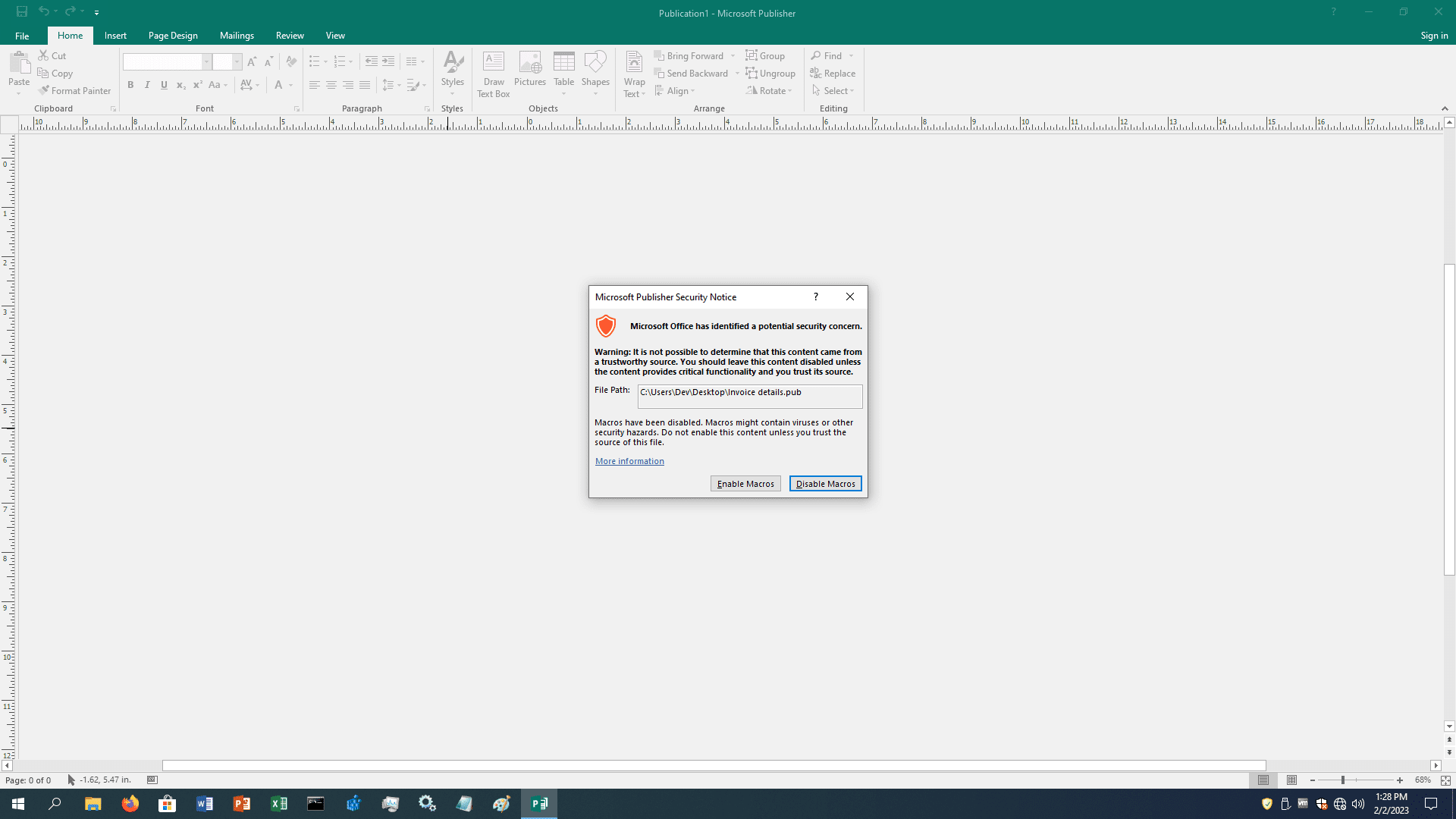
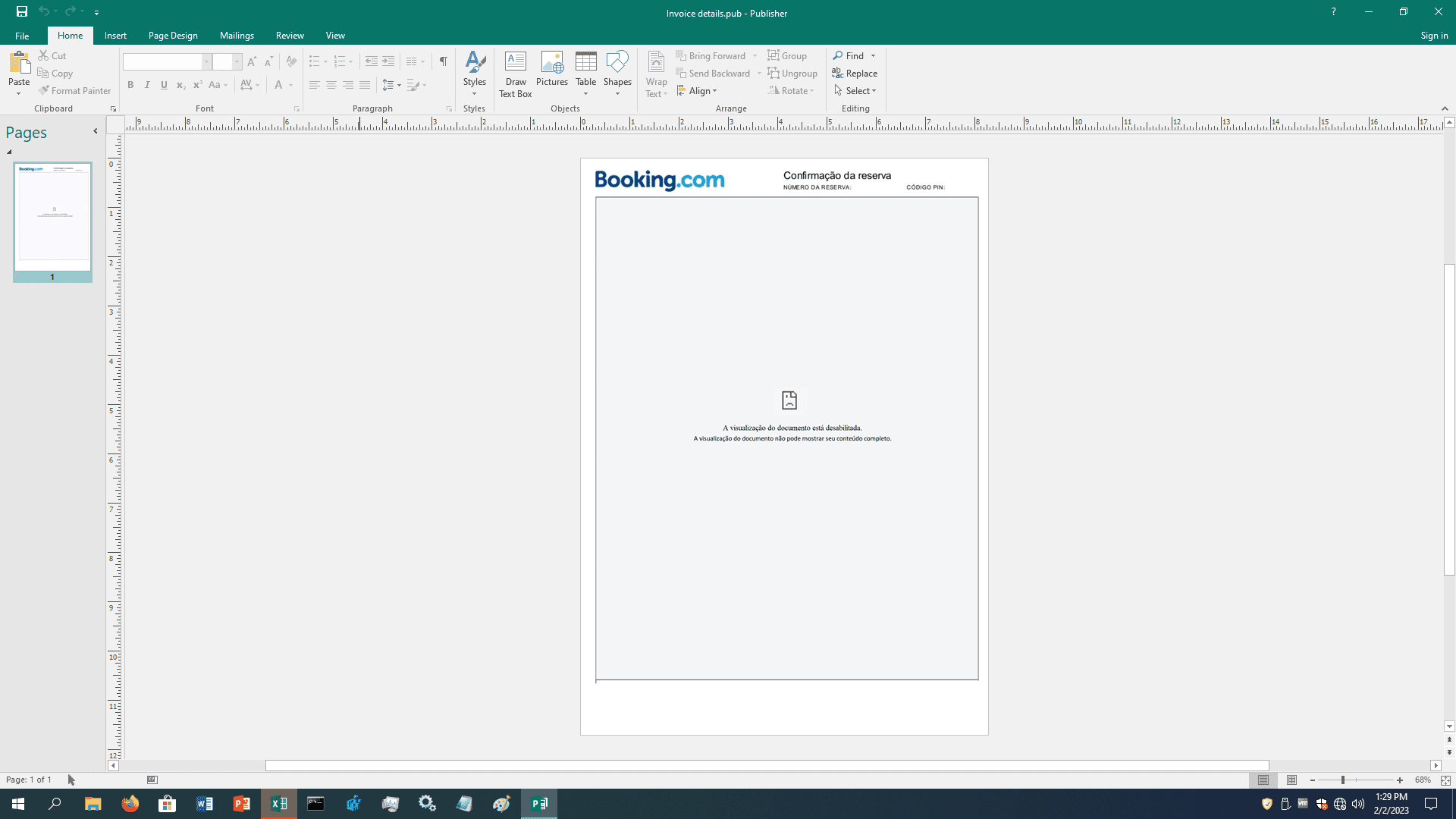
The old .pub sample we’ve tested embedded malicious macros that are detected by Microsoft Office and user is prompted with a warning window, if user clicks the “Enable Macros” then some instances of Microsoft Excel are spawned in the background and at the end the Publisher document, that is a fake invoice, is displayed and the payload is executed:
Here is the process execution flow (Excel was spawned many times):
Process: [8016]C:\Program Files\Microsoft Office\Office16\MSPUB.EXE
Process MD5 Hash: 3C0827DA4353B81E0B9F3D724EC9EDEF
Parent: [3372]C:\Windows\explorer.exe
Command Line: "C:\Program Files\Microsoft Office\Office16\MSPUB.EXE" /ou "" "C:\Users\Dev\Desktop\Invoice details.pub"
Signer: Microsoft Corporation
Parent Signer: Microsoft Windows
System File: False
Parent System File: True
Process: [6412]C:\Program Files\Microsoft Office\Office16\EXCEL.EXE
Process MD5 Hash: EA7FE880FF92EEE3D07648B1206FB552
Parent: [8016]C:\Program Files\Microsoft Office\Office16\MSPUB.EXE
Command Line: Excel
Signer: Microsoft Corporation
Parent Signer: Microsoft Corporation
System File: False
Parent System File: False
Process: [2479]C:\Program Files\Microsoft Office\Office16\EXCEL.EXE
Process MD5 Hash: EA7FE880FF92EEE3D07648B1206FB552
Parent: [8016]C:\Program Files\Microsoft Office\Office16\MSPUB.EXE
Command Line: Excel
Signer: Microsoft Corporation
Parent Signer: Microsoft Corporation
System File: False
Parent System File: False
Process: [4593]C:\Program Files\Microsoft Office\Office16\EXCEL.EXE
Process MD5 Hash: EA7FE880FF92EEE3D07648B1206FB552
Parent: [8016]C:\Program Files\Microsoft Office\Office16\MSPUB.EXE
Command Line: Excel
Signer: Microsoft Corporation
Parent Signer: Microsoft Corporation
System File: False
Parent System File: False
Process: [5860]C:\Windows\System32\cmd.exe
Process MD5 Hash: 8A2122E8162DBEF04694B9C3E0B6CDEE
Parent: [8012]C:\Program Files\Microsoft Office\Office16\MSPUB.EXE
Command Line: C:\Windows\system32\cmd.exe /c C:\Users\Public\NOTEPAD.bat
Signer: <NULL>
Parent Signer: Microsoft Corporation
System File: True
Parent System File: False
Process: [3548]C:\Windows\System32\mshta.exe
Process MD5 Hash: 0B4340ED812DC82CE636C00FA5C9BEF2
Parent: [7200]C:\Windows\System32\cmd.exe
Command Line: mshta "<URL>"
Signer: <NULL>
Parent Signer: <NULL>
System File: True
Parent System File: TrueNoVirusThanks OSArmor blocked the infection chain at the begin:
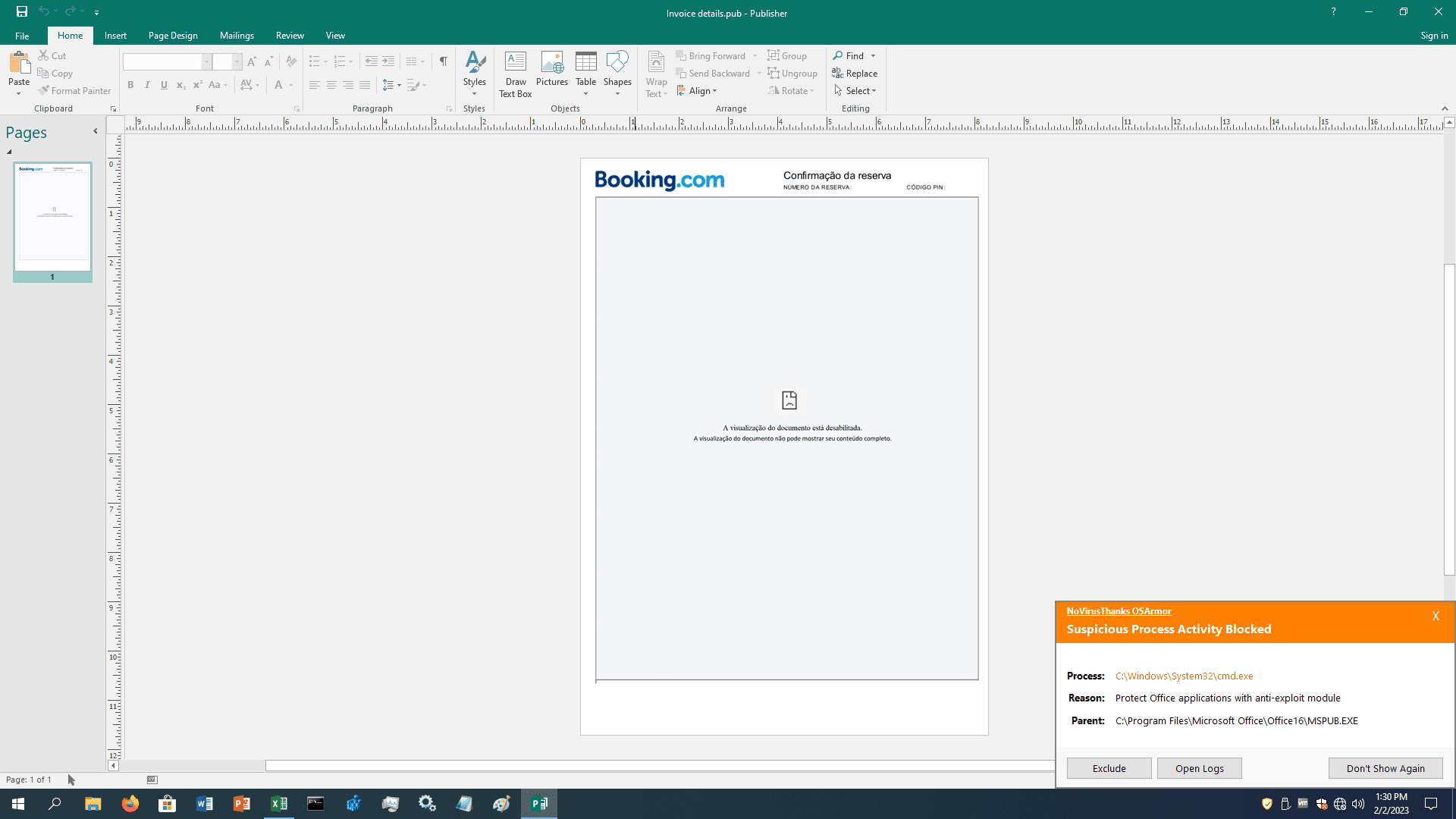
As recommended for OneNote, if you don’t use Microsoft Publisher you should block “.pub” file attachments on your email anti-spam filter, and you may want to completely block the execution of Microsoft Publisher application (MSPUB.EXE) to prevent opening of any Publisher document. Additionally, you may also want to monitor and block child processes of MSPUB.EXE for precaution (OSArmor can do this automatically).
Other Interesting Posts
- Typosquatting and Misspelled Domains Leading to Malicious HTA File
- New DLL Search Order Hijacking via System Processes on WinSxS Folder
- Searching a Tutorial on YouTube? Be Aware Where You Click (Malware Alert)
- QakBot and PikaBot Delivered via Digitally Signed MSI Windows Installers
- Fake "Copyright Infringement" Messages Lead to Facebook 2FA Bypass