Fake “Copyright Infringement” Messages Lead to Facebook 2FA Bypass
A customer contacted us due to some messages received on Facebook Messenger to unlock his Facebook page. The customer is a business owner and runs a Facebook page of his shop. According to the messages received, his page has been locked due to copyright infringement and he has to click on a link received on the messages to unlock the page:
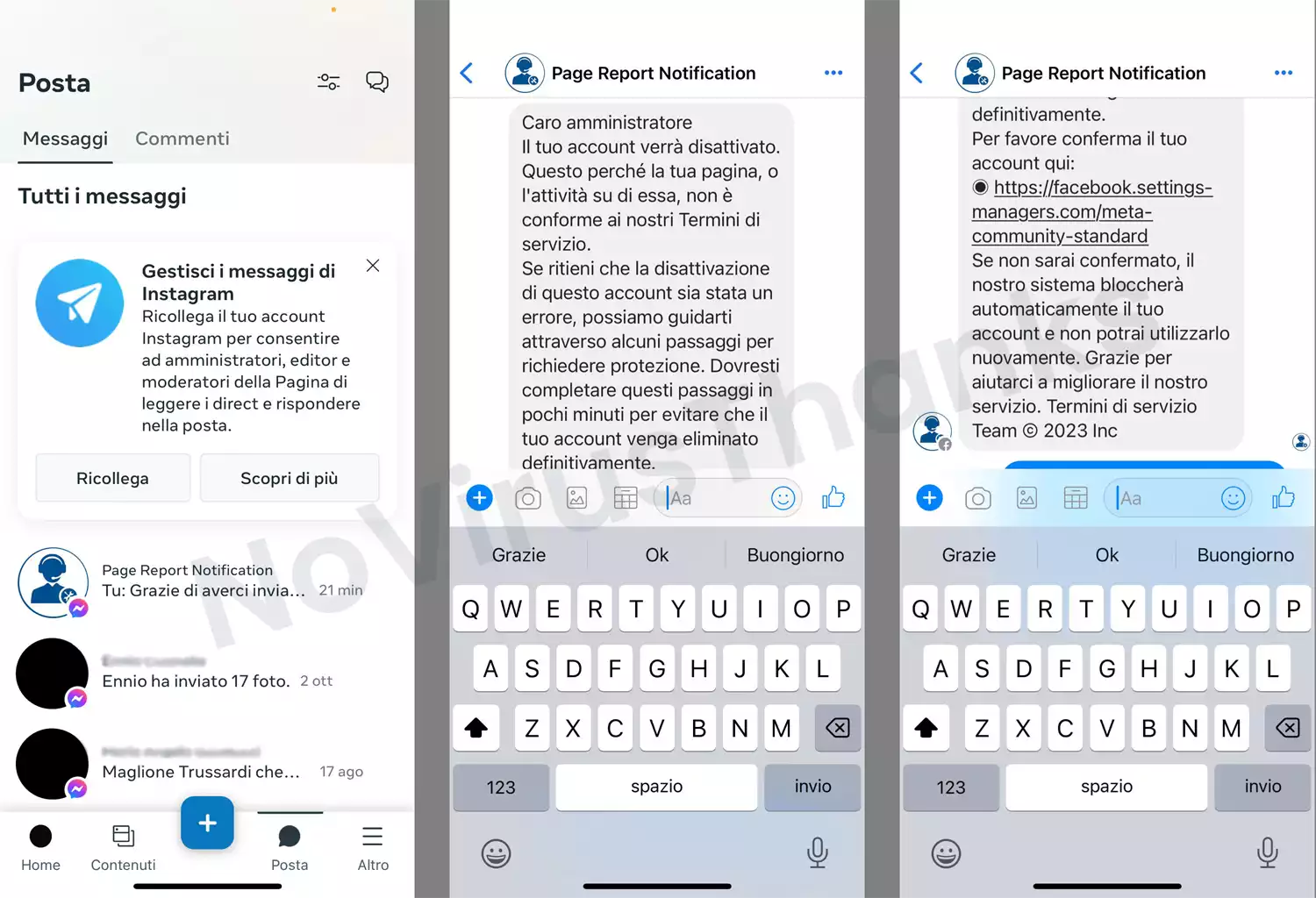
The PMs come from “Page Report Notification” and use a “customer support”-like avatar.
The malicious/phishing URL found on the messages is:
hxxps://facebook[.]settings-managers[.]com/meta-community-standardHere is a screenshot of the web page:
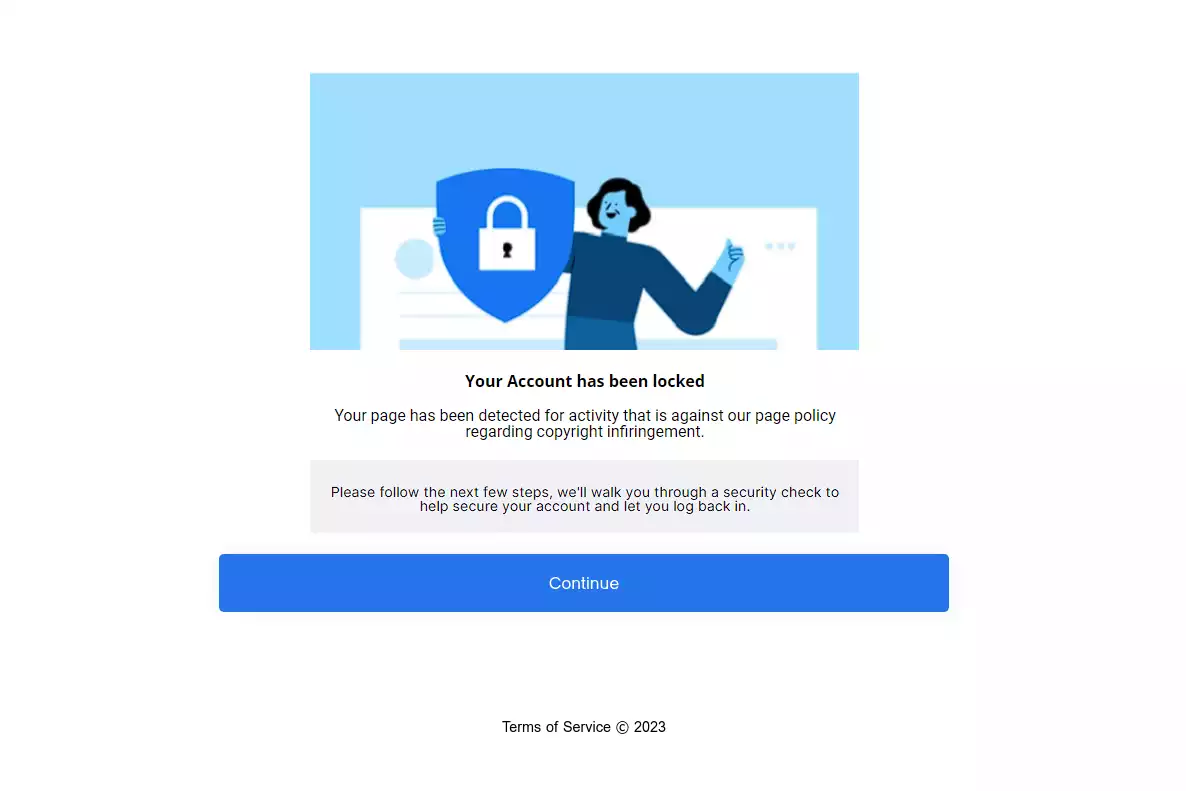
The domain name is hosted on the following IP address:
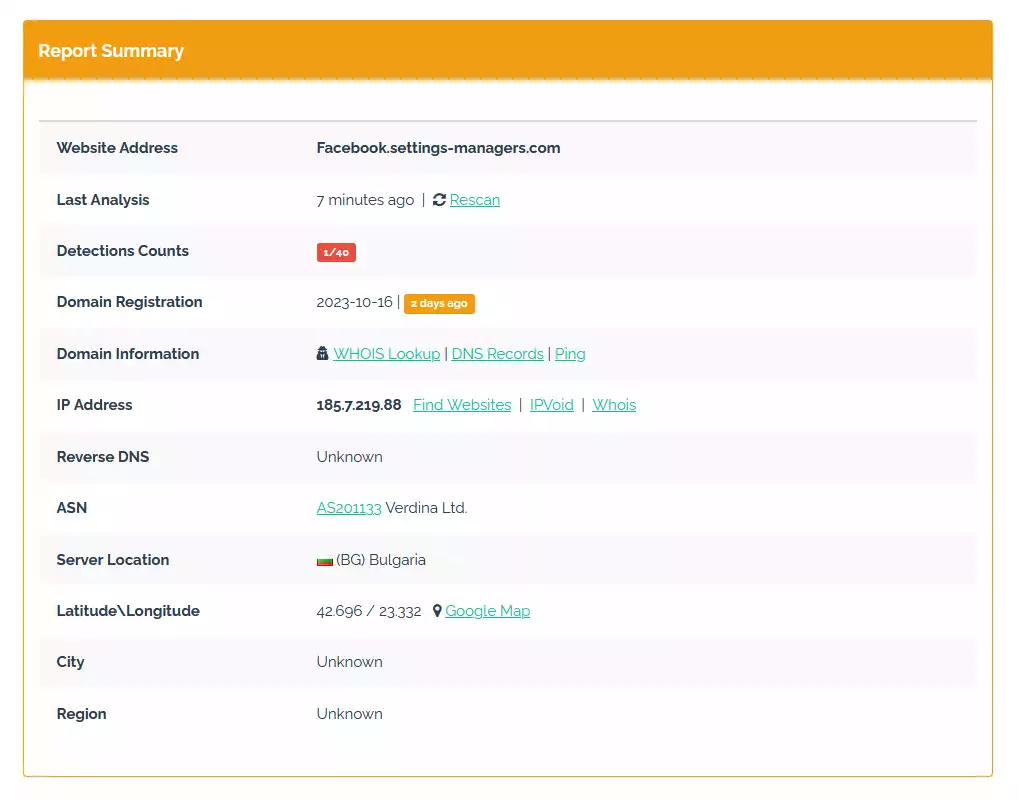
IP Address: 185.7.219.88
Reverse DNS: Unknown
ASN: AS201133 Verdina Ltd.
Company: RackSrvr LTD
Server Location: Bulgaria (BG)
City: Sofia
Timezone: Europe/Sofia
Coordinates: 42.6975,23.3241
The domain name was registered only yesterday (very suspicious):
Domain Name: SETTINGS-MANAGERS[.]COM
Registry Domain ID: 2822360161_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.namecheap.com
Registrar URL: http://www.namecheap.com
Updated Date: 2023-10-16T19:09:36Z
Creation Date: 2023-10-16T19:09:33Z
Registry Expiry Date: 2024-10-16T19:09:33Z
Registrar: NameCheap, Inc.
Registrar IANA ID: 1068
Domain Status: clientTransferProhibited https://icann.org/epp#clientTransferProhibited
Name Server: DNS1.REGISTRAR-SERVERS.COM
Name Server: DNS2.REGISTRAR-SERVERS.COM
DNSSEC: unsigned
After button “Continue” is clicked, we are redirected to this URL:
hxxps://facebook[.]settings-managers[.]com/business-help-centerHere is a screenshot of the web page:
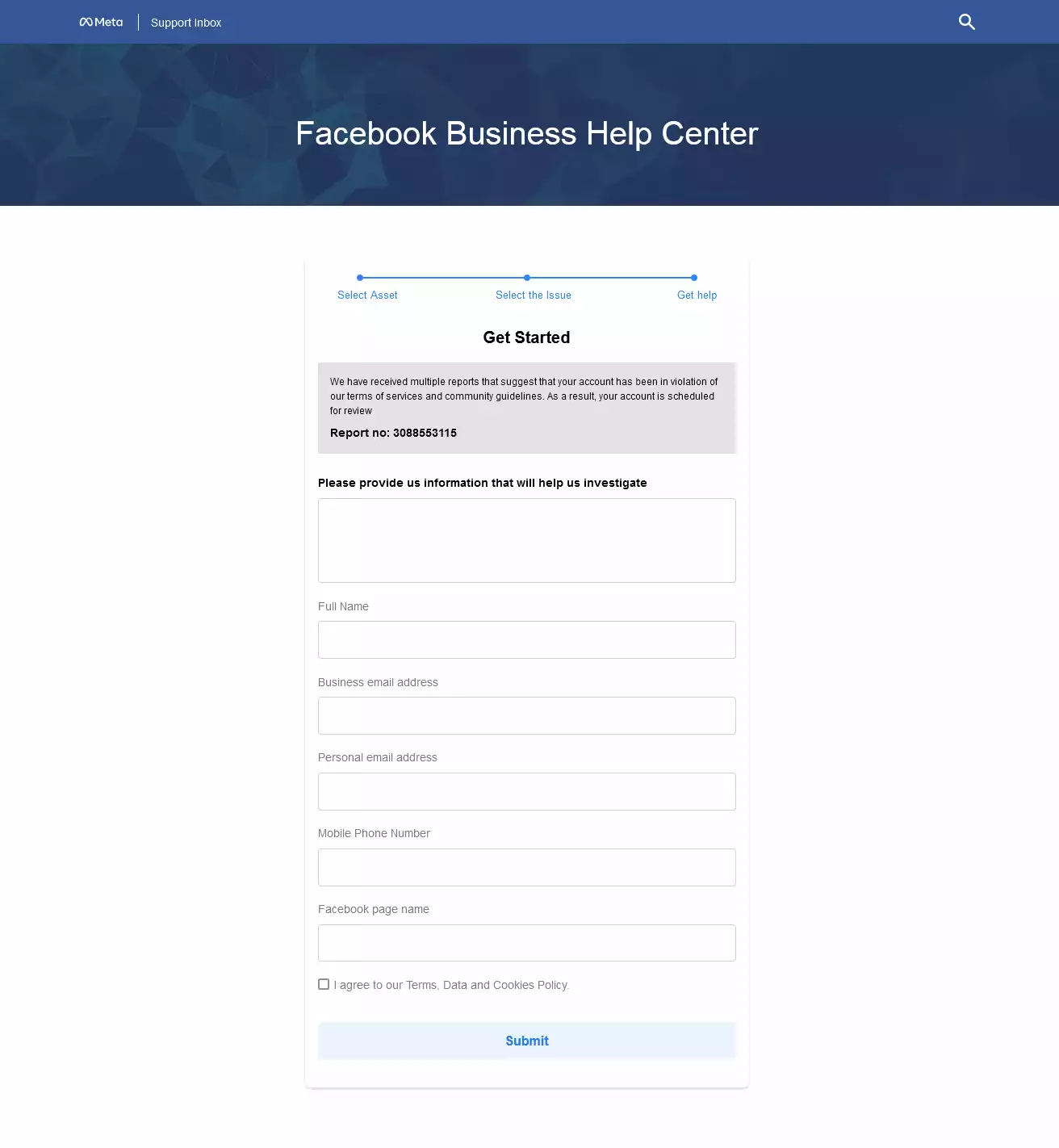
It impersonates Facebook Business Help Center, there is a “Report no” with a random number and we are requested to enter some sensitive information, which include our full name, email address (business and personal), mobile phone number and Facebook page:
After clicking the “Submit” button, a modal window is displayed:
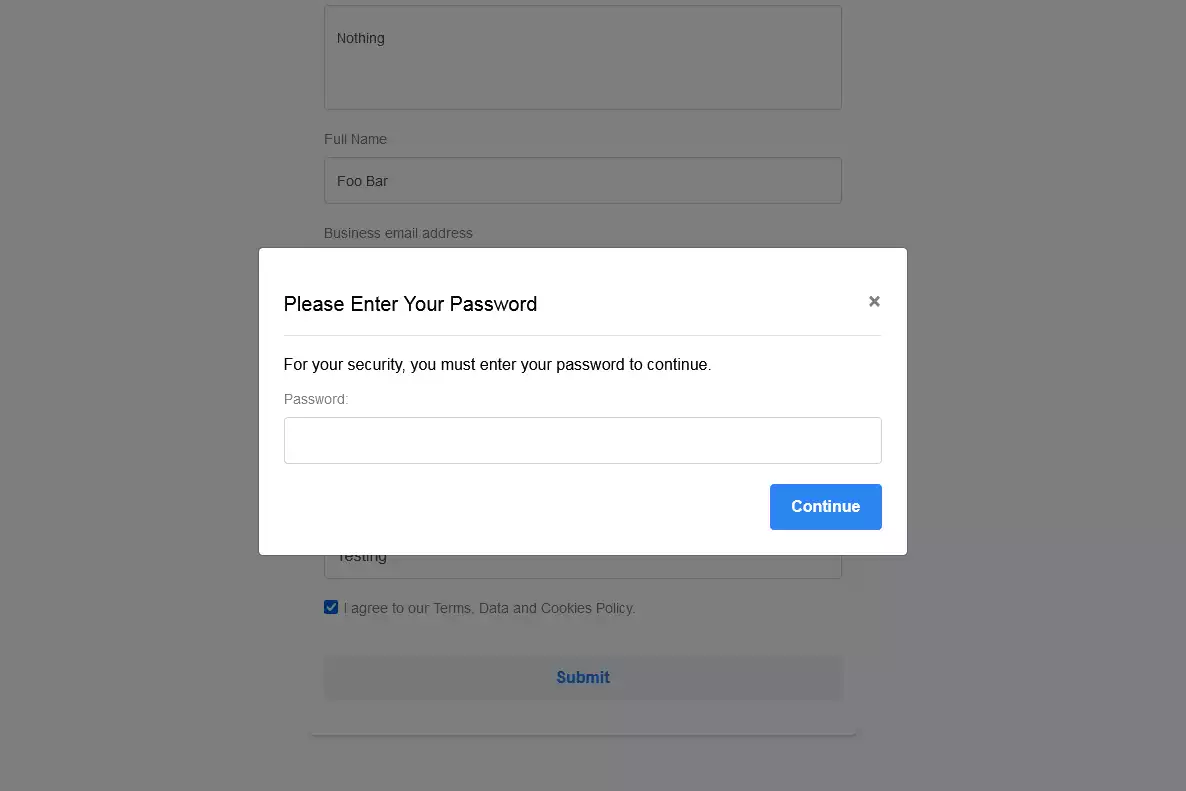
It asks to enter the Facebook account password to continue.
The first time the password is entered, it says “The password is not correct” (this seems to happen always on the first time the button “Continue” is clicked), and the second time we are presented with the new page “Two-factor authentication required”:
hxxps://facebook[.]settings-managers[.]com/confirm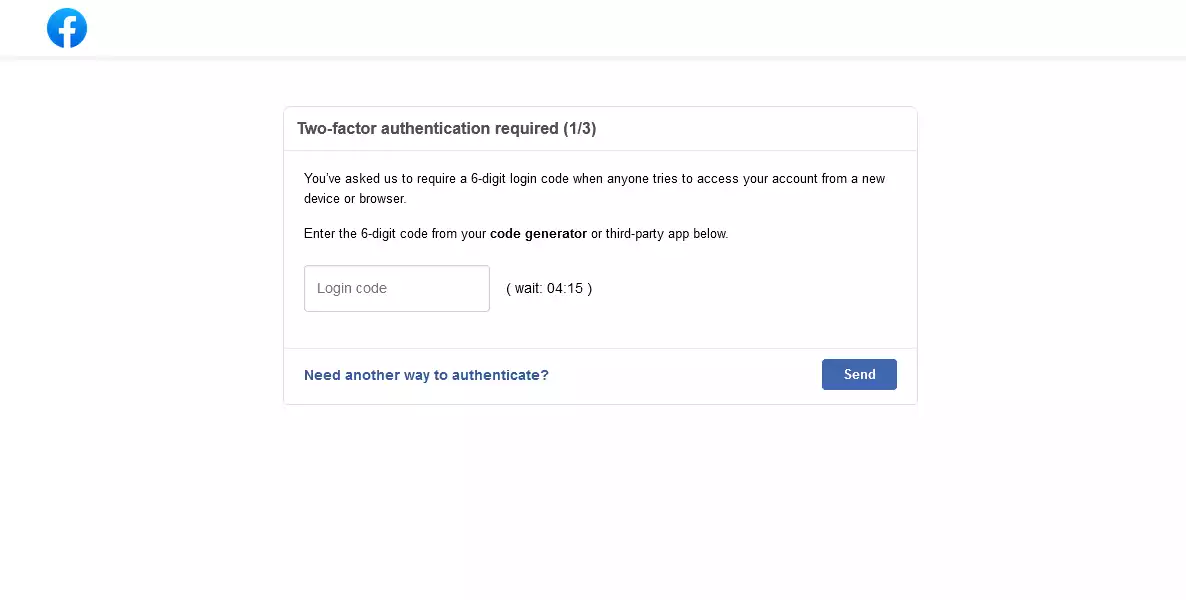
In this case the phishing page attempts to bypass two-factor authentication by asking the user to generate the code using the code generator or third-party app (e.g Google Authenticator). Same as with the previous “Please enter your password” form, the first time the authentication code is entered it shows a “Code is not valid” error message.
The data is sent via a HTTP POST request to this URL:
hxxps://api[.]settings-managers[.]com/api/confirmHere are the HTTP request headers:
POST /api/confirm HTTP/2
Host: api[.]settings-managers[.]com
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:109.0) Gecko/20100101 Firefox/110.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Content-Type: application/json;charset=UTF-8
Access-Control-Allow-Origin: *
Access-Control-Allow-Methods: GET, POST, PATCH, PUT, DELETE, OPTIONS
Access-Control-Allow-Headers: Origin, Content-Type
Content-Length: 180
Origin: hxxps://facebook[.]settings-managers[.]com
Connection: keep-alive
Referer: hxxps://facebook[.]settings-managers[.]com/
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: same-site
And here is the HTTP request payload (body) that has been sent:
{
"reason": "",
"full_name": "",
"business_email": "",
"personal_email": "",
"phone": "",
"facebook_pagename": "",
"check": false,
"first_password": "",
"second_password": "",
"logincode": "123456"
}
It contains all details we entered on the previous web forms.
The HTTP response is this JSON message:
{"success":true}And then we are redirected to the legit Facebook “Policy Center” page:
https://www.facebook.com/policies_center/This Facebook phishing attack is interesting because commonly it used to ask to enter only the email and password, but this time it asked also to enter the two-factor authentication code with an attempt to bypass 2FA authentication protection.
When you receive messages on social networks or on messenger applications make sure to always check the URLs on URLVoid, it can provide you some important information (such as the safety reputation and when domain was registered):
Other malicious domains related to this threat:
hxxp://it[.]vreplycase[.]site
hxxp://vreplycase[.]site
hxxps://babyphatapparel[.]com/help-91571208244949541129
hxxps://s[.]yam[.]com/YuFXI?/meta-notice
hxxps://ln[.]run/0ne9Z
Other Interesting Posts
- Typosquatting and Misspelled Domains Leading to Malicious HTA File
- New DLL Search Order Hijacking via System Processes on WinSxS Folder
- Searching a Tutorial on YouTube? Be Aware Where You Click (Malware Alert)
- QakBot and PikaBot Delivered via Digitally Signed MSI Windows Installers
- How to Digitally Sign Installer and Uninstaller with Inno Setup