Fake MSI Afterburner Installers Lead to Malware Infostealer
On November 20 2022 we identified a fake MSI Afterburner website promoted via Google Ads, by searching for “msi afterburner”, that impersonated the MSI website to infect users with a fake MSI Afterburner software that is in real a malware infostealer.
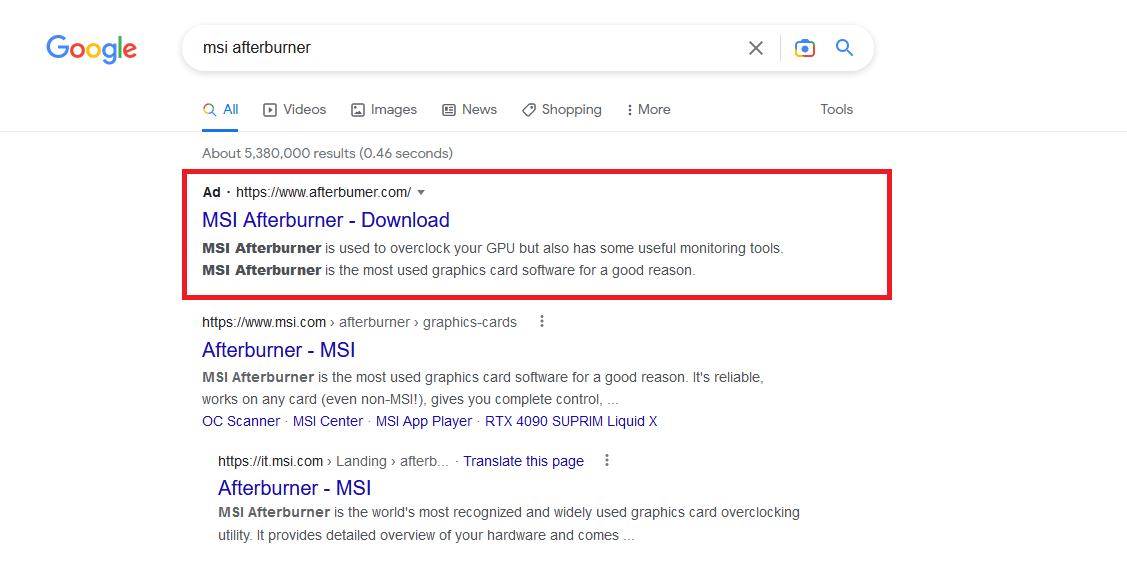
The fake MSI Afterburner website is:
Domain: Afterbumer[.]com
IP Address: 31.31.198.188
IP Country: Russia (RU)
IP ASN: AS197695 Domain names registrar REG.RU, Ltd
Registrar: REGISTRAR OF DOMAIN NAMES REG.RU LLC
Registrar IANA ID: 1606
Creation Date: 2022-11-08T15:41:34Z
Name Server: NS1.HOSTING.REG.RU
Name Server: NS2.HOSTING.REG.RUThe website looks like exactly as the official MSI website:
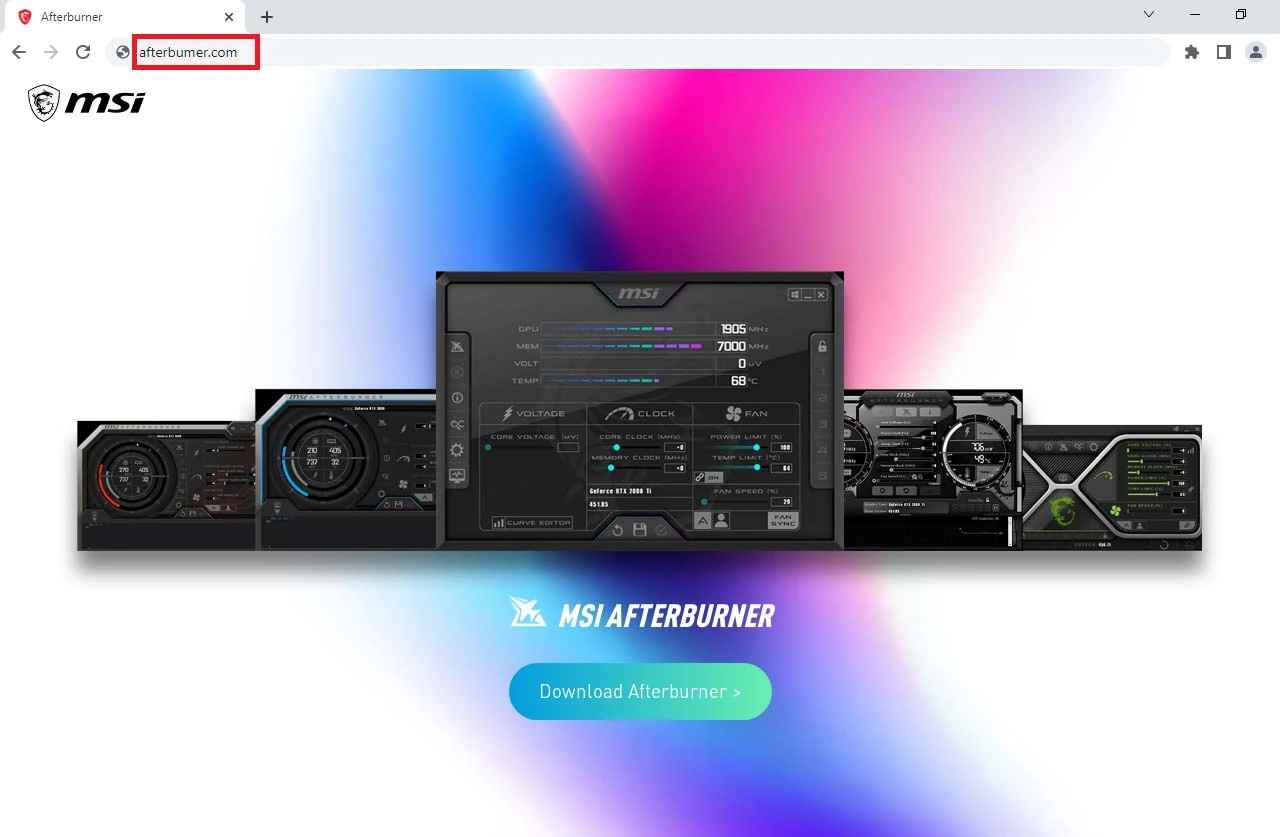
The “Download Afterburner” button points to a Google Drive URL:
hxxps://drive[.]google[.]com/uc?export=download&confirm=no_antivirus&id=1fLKrs68J8kjgTJquX_uRhWLiXvToUB7ROnce clicked, it directly downloads a .ZIP file named:
File Name: MSI Afterburner.zip
File MD5 Hash: 0359A276D0154DF3BEFCD4BECA339B62
File SHA1 Hash: 4321606C16A6E27668F2A91287DECC62721551E3
File Size: 1,30 MBIt contains a .EXE file (of 242 MB) that is the malware infostealer:
File Name: MSI Afterburner.exe
File MD5 Hash: B13C5805BE878D0E7D0F2F3F1A49275C
File SHA1 Hash: 57ACF059AB85576DB5CAF3E4CD00BC297CDC98C5
File Size: 242 MB
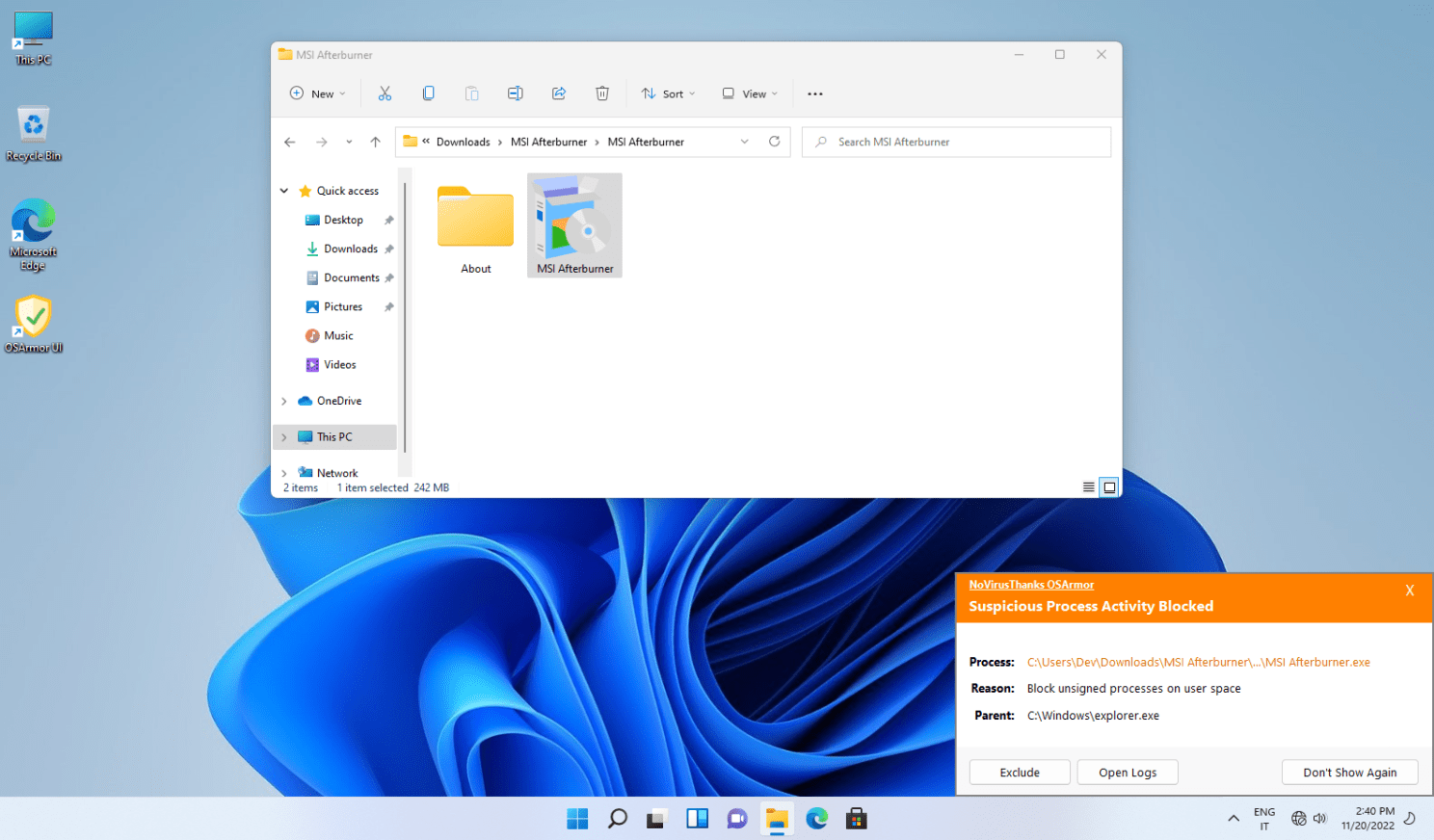
The malware sample is 242 MB probably to prevent it from being scanned by some Antivirus software that limit the size of files to scan, or to prevent it from being uploaded on VirusTotal and other online malware analysis services (some may limit the upload file size). The malware is unsigned and it can be blocked by NoVirusThanks OSArmor with the option “Block unsigned processes on user space” (unchecked by default), here is a screenshot:
Other similar suspicious domains impersonating MSI Afterburner:
hxxps://www[.]afterbumer[.]com | 31.31.198.188 | RU | AS197695 Domain names registrar REG.RU, Ltd
hxxps://app[.]msl-auterburner[.]online | 198.54.116.2 | US | AS22612 NAMECHEAP-NET
hxxp://www[.]msiafterbunet[.]space | 94.103.87.60 | RU | AS48282 Hosting technology LTD
hxxp://msl-auterburner[.]online | 198.54.116.2 | US | AS22612 NAMECHEAP-NET
hxxp://msi-afterburner[.]natriumacetat[.]com | 176.113.115.60 | RU | AS57678 Red Bytes LLC
hxxp://msl-aftenburner[.]hotelnovena[.]com | - | - | -
hxxps://www[.]msl-affteburndr[.]fun | 45.93.201.95 | RU | AS49943 IT Resheniya LLC
hxxps://www[.]msl-affteburndr[.]website | 45.93.201.95 | RU | AS49943 IT Resheniya LLC
hxxps://www[.]msl-affteburndr[.]site | 45.93.201.95 | RU | AS49943 IT Resheniya LLC
hxxps://www[.]msi-astrononubner[.]site | 5.23.50.26 | RU | AS9123 TimeWeb Ltd.
hxxps://misafterpurnier[.]space | 31.31.196.4 | RU | AS197695 Domain names registrar REG.RU, Ltd
hxxps://www[.]msiburneraftir[.]space | 37.140.192.35 | RU | AS197695 Domain names registrar REG.RU, Ltd
hxxps://www[.]msl-affteburndr[.]online | 45.93.201.95 | RU | AS49943 IT Resheniya LLC
hxxps://www[.]msl-affteburndr[.]space | 45.93.201.95 | RU | AS49943 IT Resheniya LLC
hxxps://www[.]aftlerburner[.]com | 45.93.201.95 | RU | AS49943 IT Resheniya LLC
hxxps://www[.]mslafteburners[.]online | 193.106.191.11 | RU | AS59940 Kanzas LLC
hxxps://www[.]msiburneraftir[.]site | 37.140.192.35 | RU | AS197695 Domain names registrar REG.RU, Ltd
hxxps://msi-afterburner[.]bridgewim[.]com | 176.113.115.60 | RU | AS57678 Red Bytes LLC
hxxps://msi-afterburn[.]fast-tracklogistic[.]com | 193.56.146.132 | RU | AS49912 Janeiro LLC
https://www[.]msi-afterburnerer[.]site | 172.67.194.41 | US | AS13335 CLOUDFLARENET
hxxps://www[.]afterburner-msi[.]pw | 172.67.146.144 | US | AS13335 CLOUDFLARENET
hxxps://www[.]afterburner-oc[.]com | 172.96.138.211 | US | AS395092 SHOCK-1As you can see it seems there is an ongoing malicious campaign that is bidding the “msi afterburner” keyword on Google Adwords targeting users that search for MSI Afterburner software. The websites promoted via the ads on search results have the same UI as the official MSI website and are used to infect users with infostealers or other malware.
Official MSI Afterburner website:
https://www.msi.com/Landing/afterburner/graphics-cardsIt is very important to always check the domain name that matches the official company website before download something and always download software from the official websites. As an additional protection I would also recommend to block the execution of unsigned processes on user space (in the example above I used OSArmor) so processes that are not digitally signed and located in user space are blocked by default.
More fake MSI Afterburner file hashes detected recently (December 04):
File Name: MSIAfterburner.msi
File MD5 Hash: A6E7E59E619C9EC80F21BB25F5E4BE46
File SHA1 Hash: B3450EF4BAF2806151545B611A1A1F3A1D8664C6
File Size: 57,0 MB
File Name: install-win64-11.5.8_en-US.msi
File MD5 Hash: BC826C0D654CD255E534AFAA0B8823BB
File SHA1 Hash: B709386A86BC20B73B298CB23BB985D7D84D5401
File Size: 7,92 MBMore malicious payloads URLs detected recently (December 04):
hxxps://adawayapkdownload[.]com/download/6eGnrOCahfYjxiX/22o1uAa84Bl
HTTP/2 200
date: Sun, 04 Dec 2022 12:38:04 GMT
content-type: application/octet-stream
content-length: 8302592
hxxps://www[.]rnmp[.]com[.]br/MSIAfterburner.msi
HTTP/2 200
date: Sun, 04 Dec 2022 12:41:14 GMT
content-type: application/x-msdownload
content-length: 597411840Other Interesting Posts
- New DLL Search Order Hijacking via System Processes on WinSxS Folder
- Searching a Tutorial on YouTube? Be Aware Where You Click (Malware Alert)
- QakBot and PikaBot Delivered via Digitally Signed MSI Windows Installers
- Fake "Copyright Infringement" Messages Lead to Facebook 2FA Bypass
- How to Digitally Sign Installer and Uninstaller with Inno Setup