Fake OBS Studio Websites Advertised on Google Lead to Infostealer
On the past days we identified fake OBS Studio websites advertised on Google Ads, by searching for “obs studio”, that impersonate the OBS Studio website to deliver a fake OBS Studio installer that is in real a malware infostealer (RedLine Stealer).
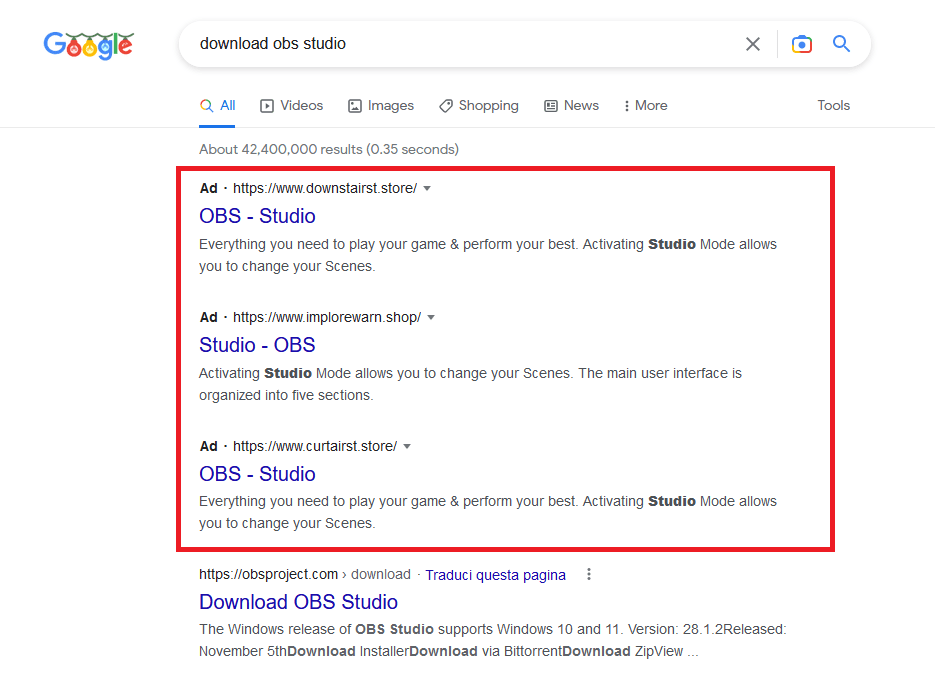
Here is the (one of the many) fake OBS Studio website:
Domain: Obsprject[.]site
IP Address: 45.15.156.176
IP Country: Netherlands (NL)
IP ASN: AS211409 Galaxy LLC
Registrar: PDR Ltd. d/b/a PublicDomainRegistry.com
Registrar IANA ID: 303
Creation Date: 2022-12-23T07:08:34.0Z
Name Server: DNS3.REGWAY.COM
Name Server: DNS2.REGWAY.COM
Name Server: DNS4.REGWAY.COM
Name Server: DNS1.REGWAY.COMThe website looks like exactly as the official OBS Studio website:
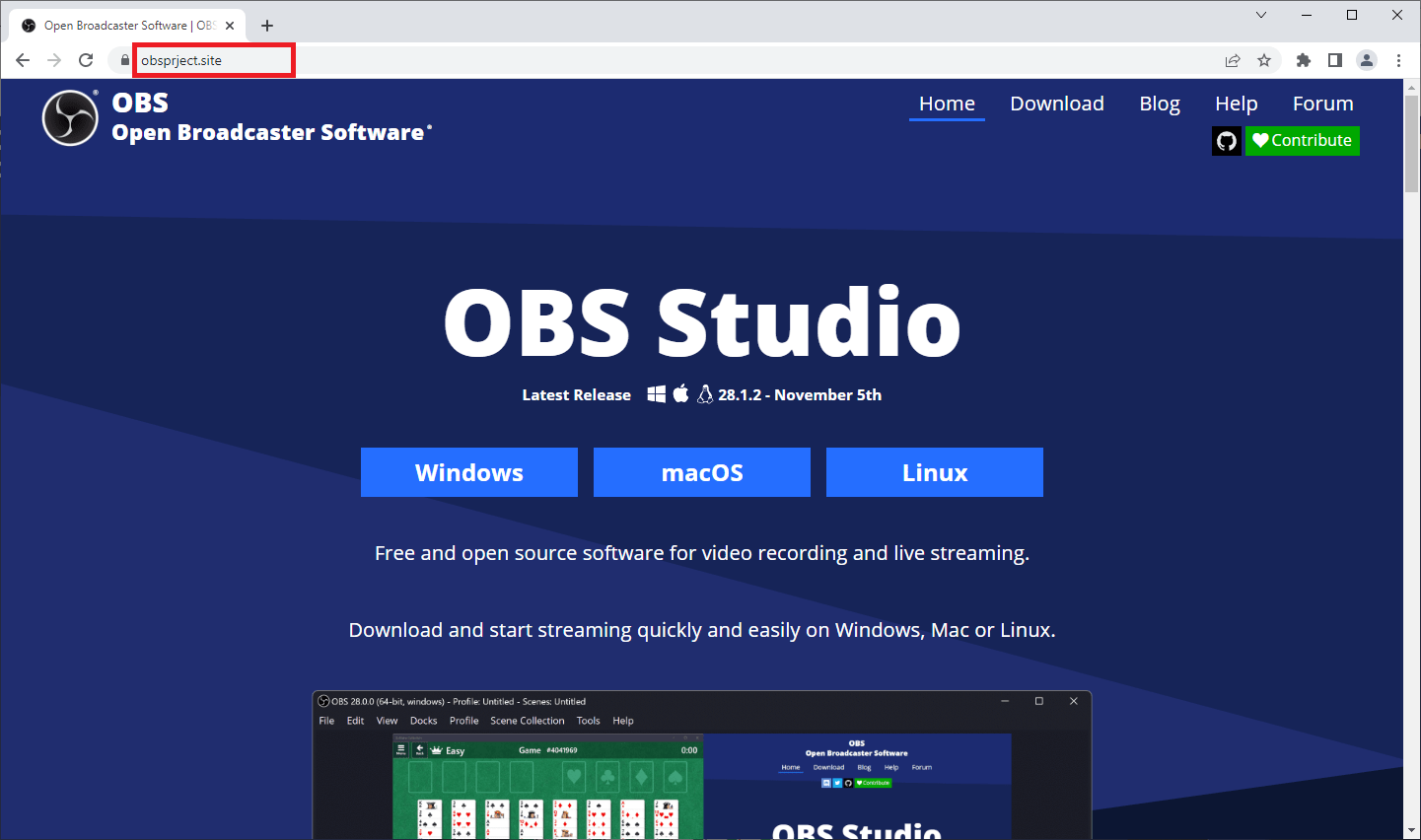
The download button points to this URL (that is used as a redirect):
hxxps://iplogger[.]com/2b7Yq6And it redirects the user to the fake OBS Studio software:
HTTP/2 302
server: nginx
date: Sat, 24 Dec 2022 11:38:58 GMT
content-type: text/html; charset=UTF-8
location: hxxps://cdn[.]discordapp[.]com/attachments/1055574420854423663/1055608941222051860/OBS-Studio-28.1.2-Full-Installer-x64.zip
set-cookie: clhf03028ja=51.15.234.36; expires=Sun, 24-Dec-2023 11:38:58 GMT; Max-Age=31536000; path=/; secure; HttpOnly; SameSite=Strict
set-cookie: 42396099856680996=1; expires=Sun, 24-Dec-2023 11:38:58 GMT; Max-Age=31536000; path=/; secure; HttpOnly; SameSite=Strict
expires: Sat, 24 Dec 2022 11:38:58 +0000
cache-control: no-store, no-cache, must-revalidate
strict-transport-security: max-age=604800
content-security-policy: img-src https: data:; upgrade-insecure-requests
strict-transport-security: max-age=31536000
x-frame-options: SAMEORIGINThe URL of the fake OBS Studio installer is hosted on Discord:
hxxps://cdn[.]discordapp[.]com/attachments/1055574420854423663/1055608941222051860/OBS-Studio-28.1.2-Full-Installer-x64.zipHere are file details of the downloaded ZIP file:
File: OBS-Studio-28.1.2-Full-Installer-x64.zip
File size: 128 MB (134.053.544 bytes)
MD5 checksum: 5693838009BEC79BA8359B23AFAE8A93
SHA1 checksum: A6008C10CDAB4BECA0A8EB9995820813F82BCD83
SHA256 checksum: 794F4EDD6E15EBCA222BCE54C0F1C3E418A1BDD83A329FF0F3DFF1B48983B907It contains a EXE file named OBS-Studio-28.1.2-Full-Installer-x64:
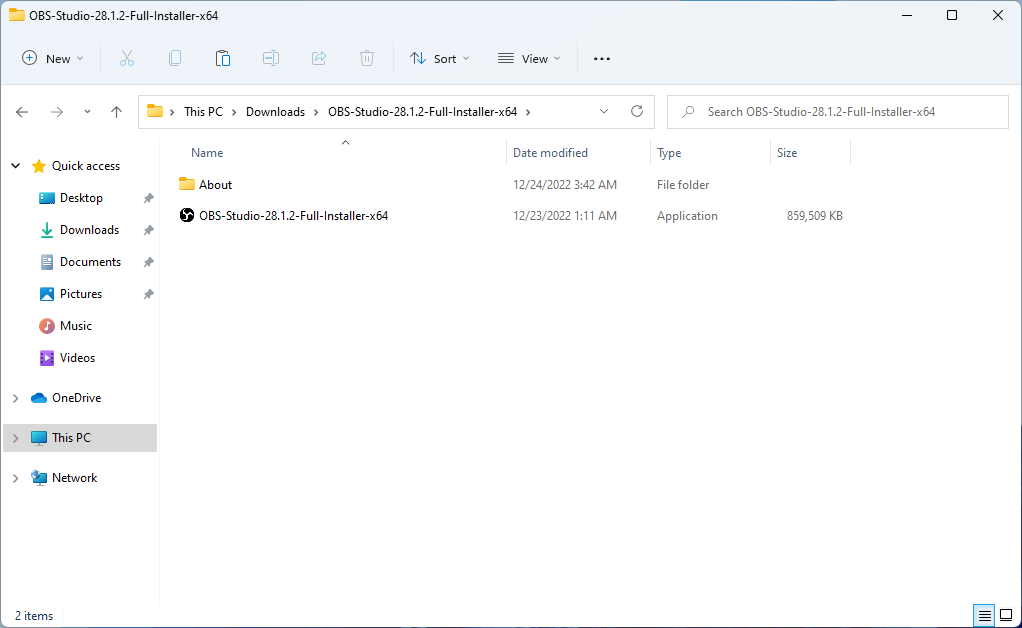
File: OBS-Studio-28.1.2-Full-Installer-x64.exe
File size: 839 MB (880,136,314 bytes)
MD5 checksum: 63912FBCF0867242B73AC3165801F73F
SHA1 checksum: CBBAF35E8DCE467B4CACD8CA2917DAF95179E3F6The fake installer is digitally signed by “Discord Inc.” and is obviously invalid:
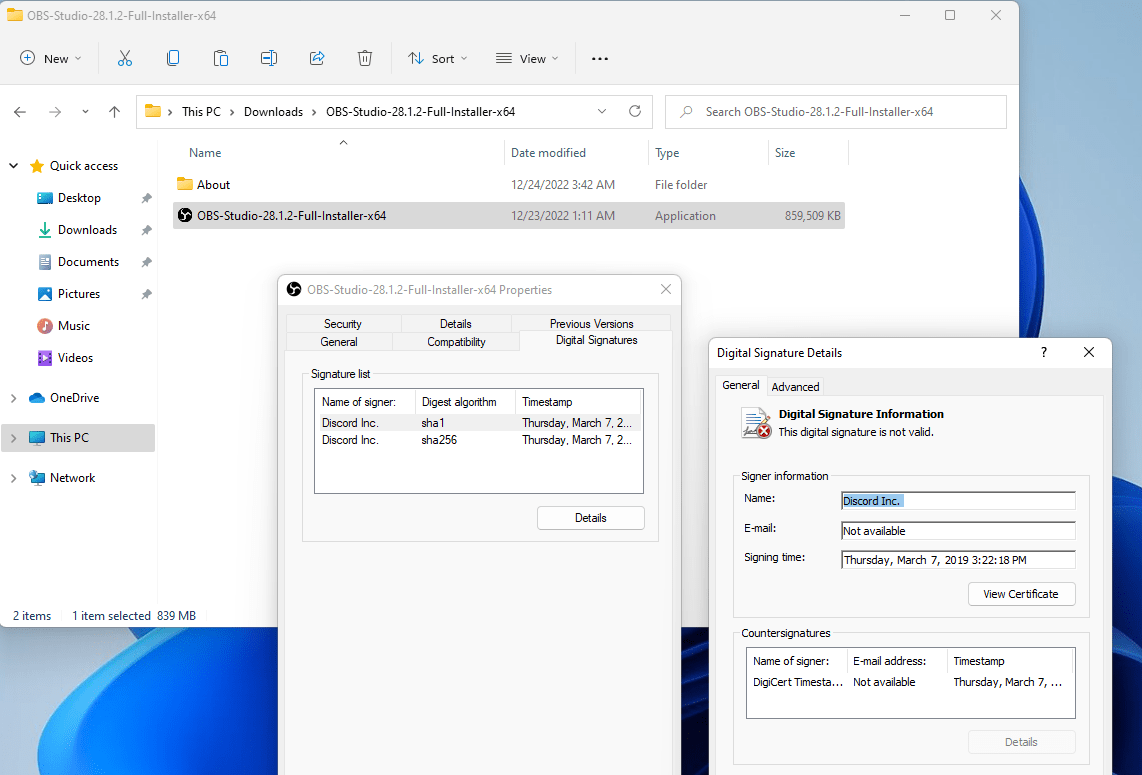
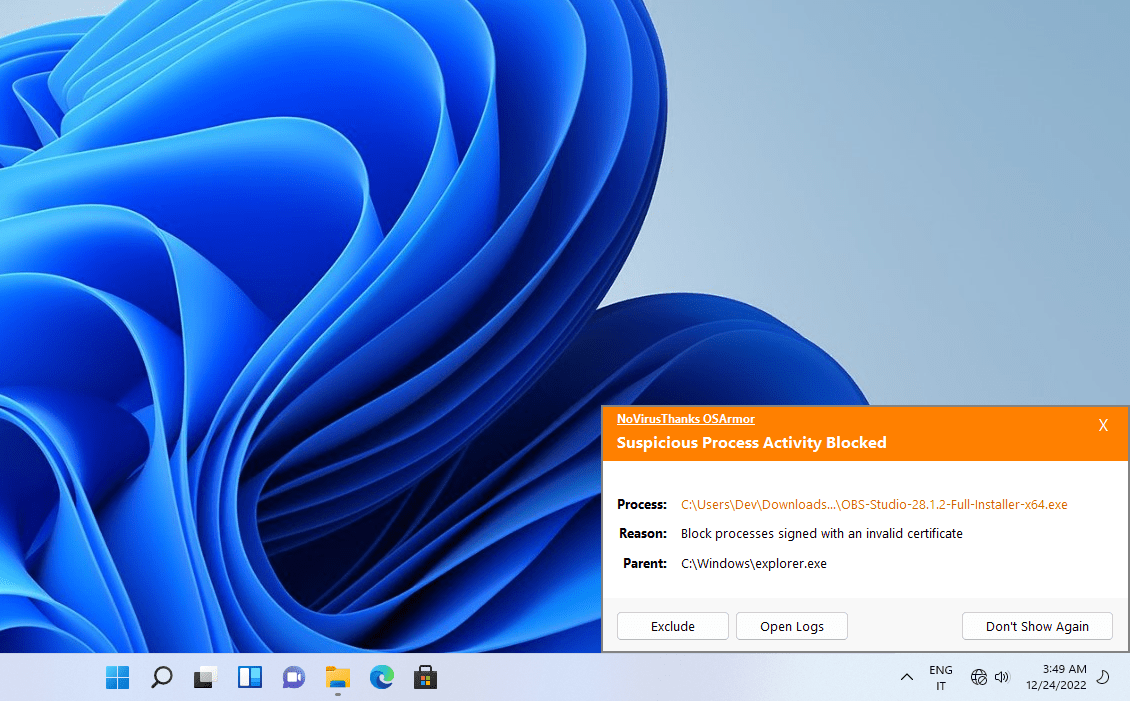
The malware sample is 840 MB probably to prevent it from being scanned by some Antivirus software that limit the size of files to scan, or to prevent it from being uploaded on VirusTotal and other online malware analysis services (some may limit the upload file size). The malware is signed with an invalid certificate and it is blocked by NoVirusThanks OSArmor with default protection options (we highly recommend to enable the option “Block unsigned processes on user space” to block any unsigned process), here is a screenshot:
Other malicious websites found on Google Ads of search results:
hxxps://www[.]curtairst[.]store | 188.114.97.2 | NL | AS13335 CLOUDFLARENET
hxxps://www[.]downstairst[.]store | 172.67.184.100 | US | AS13335 CLOUDFLARENET
hxxps://www[.]implorewarn[.]shop | - | - | -
hxxps://www[.]obslivestudio[.]live | 188.114.97.2 | NL | AS13335 CLOUDFLARENET
hxxps://www[.]electionship[.]store | 104.21.49.137 | - | AS13335 CLOUDFLARENET
hxxps://www[.]phonetv[.]shop | 172.67.181.7 | US | AS13335 CLOUDFLARENET
hxxps://www[.]prupleish[.]store | 188.114.97.2 | US | AS13335 CLOUDFLARENET
hxxps://www[.]roverlexuslife[.]shop | 188.114.96.2 | NL | AS13335 CLOUDFLARENET
hxxps://www[.]ywampescara[.]com | - | - | -
hxxps://www[.]imforming[.]shop | 188.114.97.2 | NL | AS13335 CLOUDFLARENET
hxxps://www[.]buzkashirtswear[.]shop | 104.21.73.74 | - | AS13335 CLOUDFLARENET
hxxps://www[.]obssreviwz[.]sbs | 45.15.156.176 | NL | AS211409 Galaxy LLC
hxxps://www[.]guiyanmar[.]store | 188.114.96.2 | NL | AS13335 CLOUDFLARENET
hxxps://www[.]notpwju[.]xyz | 104.21.93.36 | - | AS13335 CLOUDFLARENET
hxxps://www[.]obsprojectssc[.]store | 45.93.201.95 | RU | AS49943 IT Resheniya LLC
hxxps://www[.]obcproject[.]fun | 45.93.201.95 | RU | AS49943 IT Resheniya LLC
hxxps://www[.]obcproject[.]space | 45.93.201.95 | RU | AS49943 IT Resheniya LLC
hxxps://www[.]obsproo[.]store | 45.93.201.95 | RU | AS49943 IT Resheniya LLC
hxxps://www[.]revolutionmarsbuild[.]com | 45.15.156.176 | NL | AS211409 Galaxy LLC
hxxps://www[.]thismightendbadly[.]com | 45.15.156.176 | NL | AS211409 Galaxy LLC
hxxps://www[.]obsprr[.]store | 45.93.201.95 | RU | AS49943 IT Resheniya LLC
hxxps://www[.]obstreamview[.]site | 45.15.156.176 | NL | AS211409 Galaxy LLC
hxxps://www[.]blogdom[.]site | 188.114.96.2 | NL | AS13335 CLOUDFLARENET
hxxps://www[.]commosty[.]store | 188.114.96.2 | NL | AS13335 CLOUDFLARENETAs you can see it seems there is an ongoing malicious campaign that is bidding the “obs studio” keyword on Google Adwords targeting users that search for OBS Studio software. The websites promoted via the ads have the same UI as the official OBS Studio website and are used to infect users with infostealer or other malware.
Official OBS Studio website:
https://obsproject.comIt is very important to always check the domain name that matches the official company website before download something and always download software from the official websites. As an additional protection I would also recommend to block the execution of unsigned processes on user space (in the example above I used OSArmor) so processes that are not digitally signed and located in user space are blocked by default.
Other malicious domains impersonating OBS Studio website:
hxxps://obs-project[.]acmallas[.]com | 194.4.49.130 | FR | AS44477 Stark Industries Solutions Ltd
hxxps://obs-project[.]ossincorp[.]com | 194.4.49.212 | FR | AS44477 Stark Industries Solutions Ltd
hxxps://obs-project[.]crown-phone[.]com | 31.222.238.43 | NL | AS43624 Pq Hosting S.r.l.
hxxps://obstudio[.]us | - | - | -
hxxps://obsprject[.]site | 45.15.156.176 | NL | AS211409 Galaxy LLC
hxxps://notpwju[.]xyz | 104.21.93.36 | - | AS13335 CLOUDFLARENETDirect download links of fake OBS Studio software:
hxxps://github[.]com/Roberhdjsjshhs/aternos/releases/download/OBS/SetupMain.zip
hxxps://bitbucket[.]org/diannogornodonova28/studio/downloads/OBS_projects.zip
hxxps://cdn[.]discordapp[.]com/attachments/1055574420854423663/1055608941222051860/OBS-Studio-28.1.2-Full-Installer-x64.zip
hxxps://wsakefy[.]shop/dl-obs.phpMore fake OBS Studio file hashes detected recently (December 23):
File: OBS_projects.zip
File size: 11,1 MB (11.630.763 bytes)
MD5 checksum: F04281DDE3A9EA2B64F3B4663C8D73AD
SHA1 checksum: A512161050C6349DA41F27FD6A28049EF8DD16DC
SHA256 checksum: 474745317F7C34B7303F2F3582558B8B0332E8DC0E2B567129C58413858091E6
File: OBS-Studio-28.1.2-Full-Installer-x64.zip
File size: 128 MB (134.053.544 bytes)
MD5 checksum: 5693838009BEC79BA8359B23AFAE8A93
SHA1 checksum: A6008C10CDAB4BECA0A8EB9995820813F82BCD83
SHA256 checksum: 794F4EDD6E15EBCA222BCE54C0F1C3E418A1BDD83A329FF0F3DFF1B48983B907
File: SetupMain.zip
File size: 1,89 MB (1.985.921 bytes)
MD5 checksum: 0479B0C8756ABB5C38D806800FAD0D53
SHA1 checksum: D085FA2F942AF29CABD81F5A7E453882B7F3B7AA
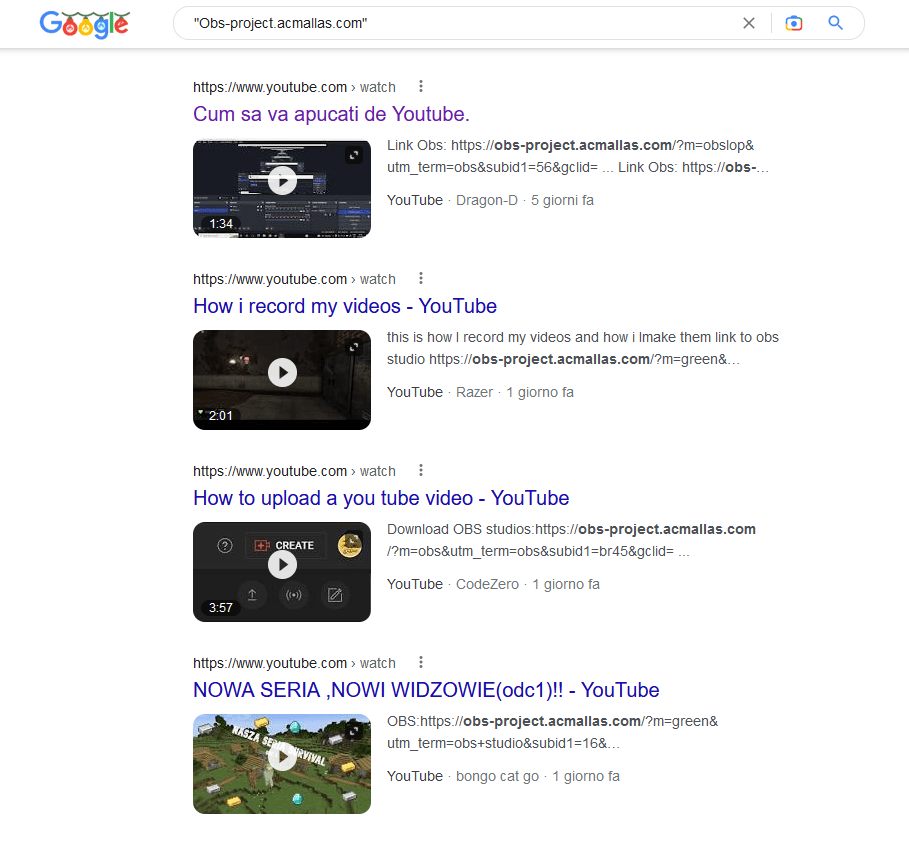
SHA256 checksum: 45C850596A928B7D31871F137BAB1052C44D2B3E8D26B3F2F059A510A60EF0EEBy searching for one of the fake OBS Studio websites on YouTube, we have noticed many videos are promoting these malicious websites on the description and encourage users to download and install these fake OBS Studio installers, some also recommend to the users to disable their Antivirus software and Microsoft Defender before run them:
Other Interesting Posts
- Typosquatting and Misspelled Domains Leading to Malicious HTA File
- New DLL Search Order Hijacking via System Processes on WinSxS Folder
- Searching a Tutorial on YouTube? Be Aware Where You Click (Malware Alert)
- QakBot and PikaBot Delivered via Digitally Signed MSI Windows Installers
- Fake "Copyright Infringement" Messages Lead to Facebook 2FA Bypass