Searching a Software? Be Aware Where You Click, You May Get Malware
It looks like there is a massive ongoing malvertising campaign on Google Ads of search results that targets users looking to download popular software like MSI Afterburner, OBS Studio, Brave Browser, Notepad++, VLC Media Player, Audacity, AnyDesk, and many more. In the past days we have reported fake MSI Afterburner websites and fake OBS Studio websites, but it seems a large number of popular Windows software names is affected.
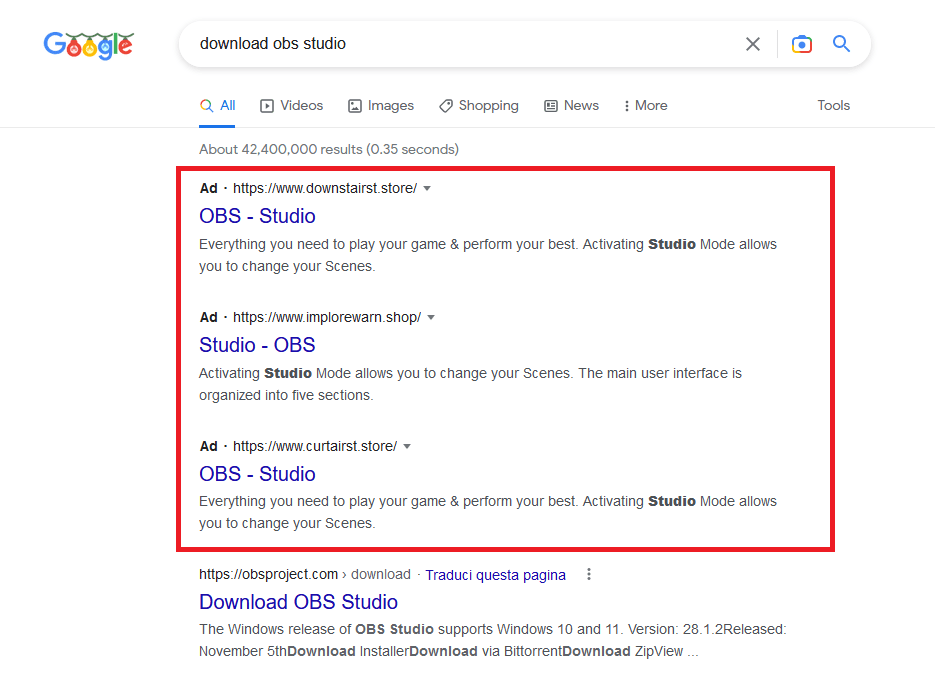
Basically, if you search for a popular software like “brave download” or also just the software name like “msi afterburner” there is a high chance that you will get on first results of Google search some advertised websites (generally with .store or .top TLD) that redirect the user to fake software websites (that look same as the legit one) that deliver malware. Here is an example of a fake VLC Media Player website that deliver a malicious installer:
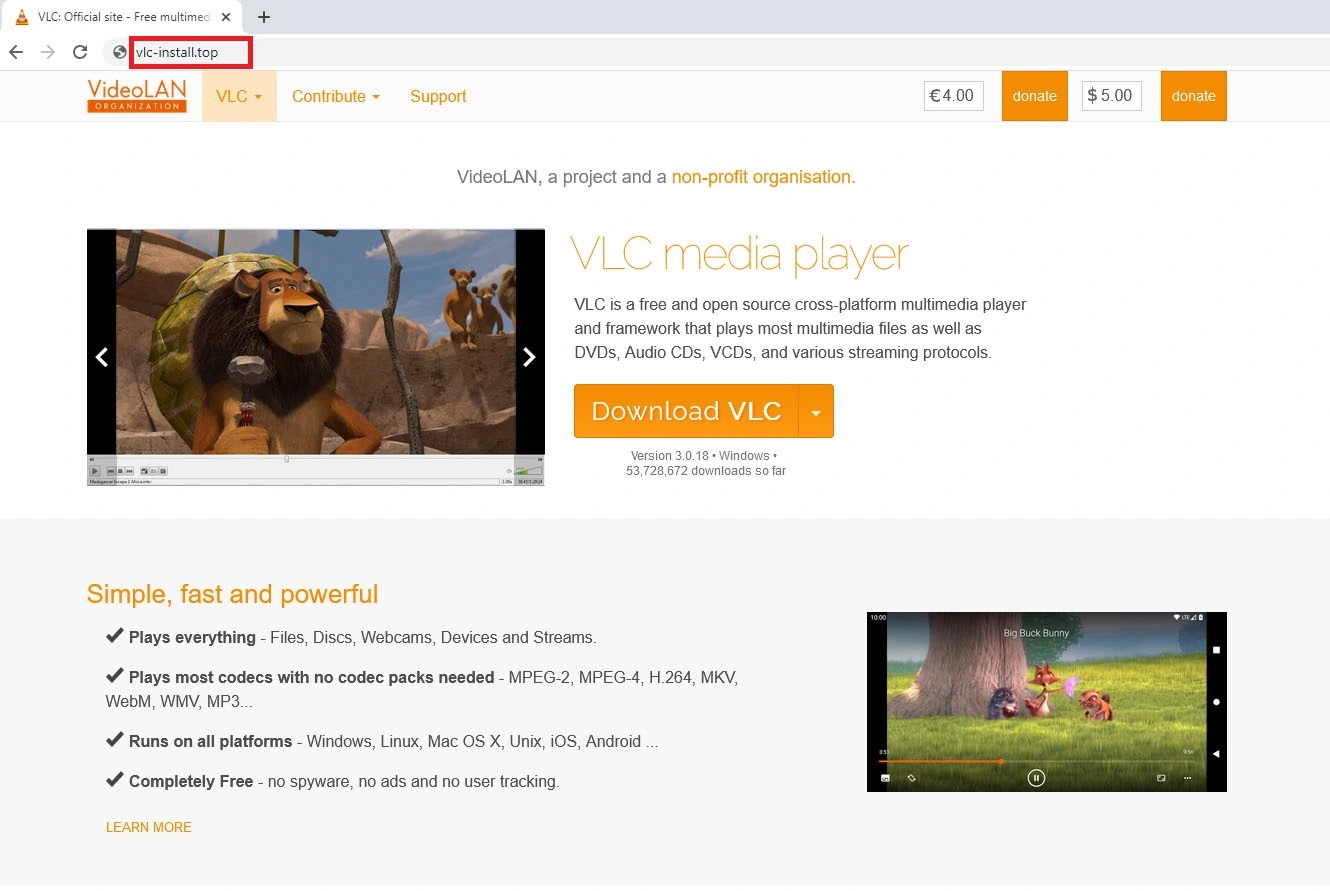
The fake VLC Media Player website has a .TOP extension:
Domain: Vlc-install[.]top
IP Address: 172.67.188.105
IP Country: United States (US)
IP ASN: AS13335 CLOUDFLARENET
Registrar: NameSilo,LLC
Registrar IANA ID: 1479
Creation Date: 2022-12-28T14:12:44Z
Name Server: rosalyn.ns.cloudflare.com
Name Server: bart.ns.cloudflare.comThe “Download VLC” button delivers the fake VLC installer:
hxxps://transfer[.]sh/get/SMMcbF/vlc_install.exeThe fake installer is a .EXE file, unsigned and requires Administrator rights:
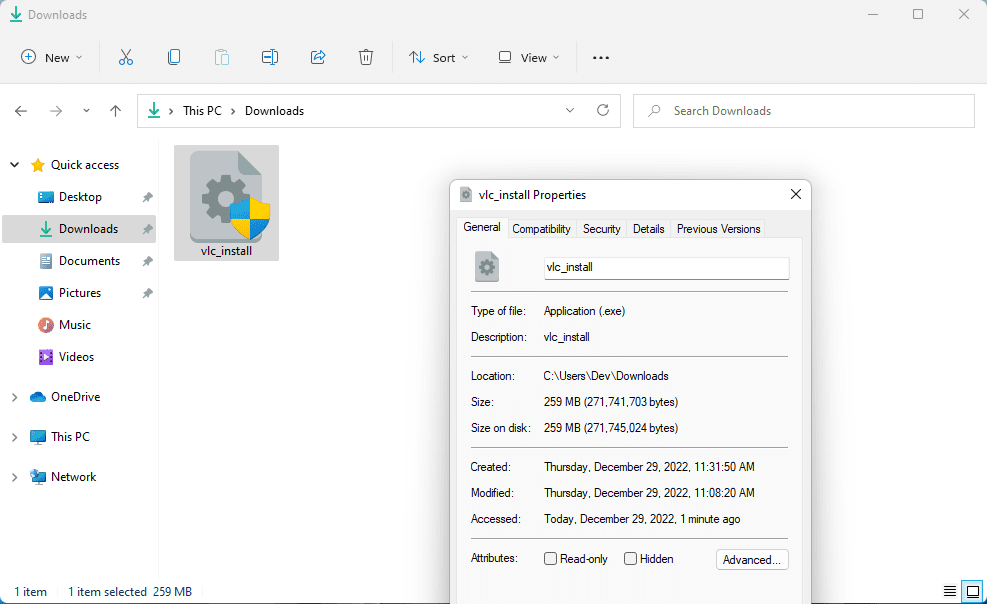
File: vlc_install.exe
File size: 259 MB (271.741.703 bytes)
MD5 checksum: 41CE8C53B4653F464344303393D20C5D
SHA1 checksum: C012039DDB144CEBD4C0C68C84E124C230A000F5
SHA256 checksum: D5B8380662A41FD4409C1F4F5F821C77C7EC225514AEF8AFD5E01FC036FB10DBOne interesting thing we found is that a fake Brave installer is a .ISO file:
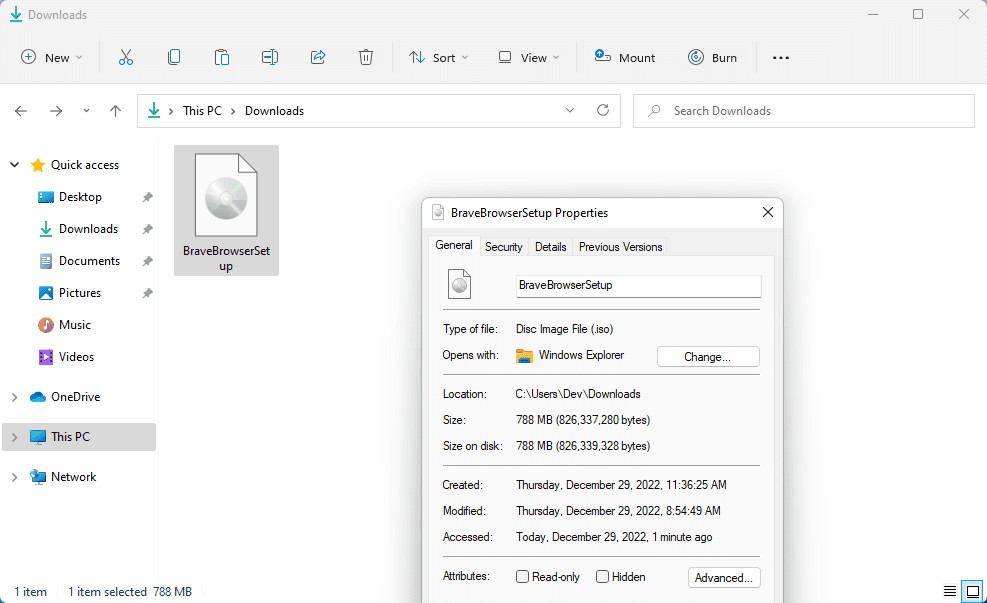
Mostly all fake installers we have found were in .ZIP, .RAR, .EXE or .MSI file extensions.
Once double-clicked, the ISO file is mounted as virtual disk and shows the files contained inside the ISO file, including BraveBrowserSetup.exe that is the fake installer:
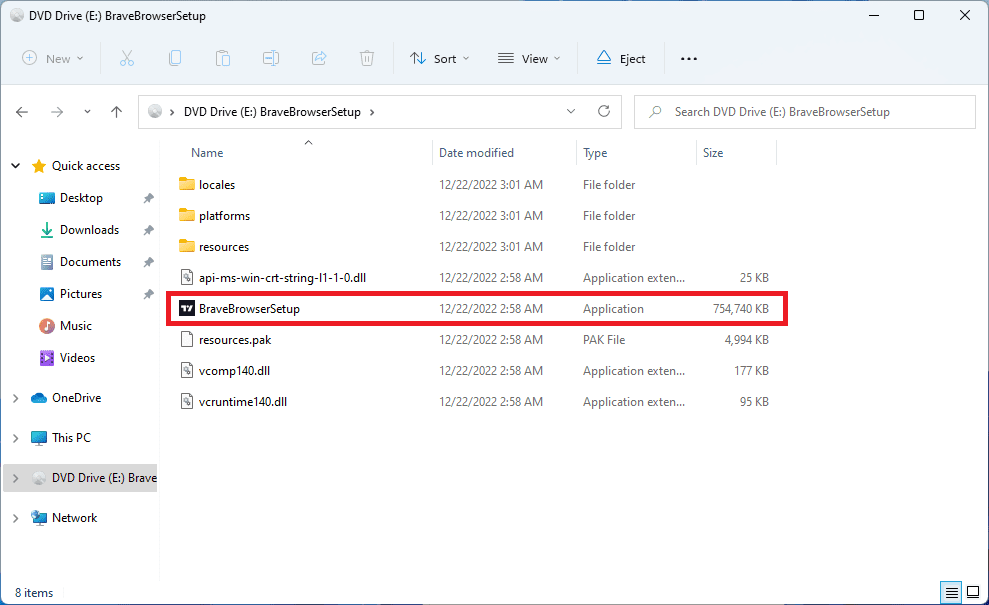
File: BraveBrowserSetup.exe
File size: 737 MB (772.853.552 bytes)
MD5 checksum: FF8867B992BB02459769949537FD9010
SHA1 checksum: 19A5F8F521F2B0DF1D0A4661A67A52A91AE9DE55
SHA256 checksum: DECB30787800155B96778F23FCE23CB037874585BD810F32F6B6DAEA85449496Here is a list of other malicious websites delivering fake installers:
hxxps://www[.]am-pm-contracting[.]com | 45.84.206.2 | LT | AS47583 Hostinger International Limited
hxxps://brave-browser[.]bigkek[.]com | 5.45.67.49 | NL | AS58061 Scalaxy B.V.
hxxps://www[.]aspergerspedia[.]com | 91.217.9.72 | RU | AS44094 Webhost LLC
hxxps://get-brave[.]org | 45.84.206.2 | LT | AS47583 Hostinger International Limited
hxxps://brave-cryptobrowser[.]com | 188.114.97.2 | NL | AS13335 CLOUDFLARENET
hxxps://brave-browser[.]quarrycontrols[.]com | 79.137.192.10 | RU | AS204603 Partner LLC
hxxps://www[.]aiudacityorg[.]com | 191.101.79.138 | US | AS47583 Hostinger International Limited
hxxps://vlc-install[.]top | 104.21.33.5 | - | AS13335 CLOUDFLARENET
hxxps://www[.]turkina[.]store | 104.21.71.206 | - | AS13335 CLOUDFLARENET
hxxps://any-desktop.empresahbjbj[.]com | 31.222.238.43 | NL | AS43624 Pq Hosting S.r.l.
hxxps://www[.]tradisical[.]store | 104.21.37.252 | - | AS13335 CLOUDFLARENETHere is a list of other direct-download URLs of fake installers:
hxxps://bitbucket[.]org/alexjamescoloomb/hop/downloads/Any-Desk.zip
hxxps://www[.]dropbox[.]com/s/cqj117rmivn38ov/braveappsetup-v56.11.2.zip?dl=1
hxxps://transfer[.]sh/get/YYyEzp/BraveBrowserSetup.isoAs you can see, the fake installers are hosted on free file sharing services.
All these fake software installers can be blocked by NoVirusThanks OSArmor with the option “Block unsigned processes on user space” (unchecked by default, you need to manually enable it), the others are blocked with the default protection profile (such as fake installers signed with an invalid or revoked digital signature, or unsigned .MSI installers).
If you don’t pay close attention to where you click when searching for software, it can be easy to run a fake (and malicious) installer without even knowing it. A simple workaround can be to avoid clicking on the first few ad-promoted results when searching for a software name and instead prefer organic results that generally show the official website.
Other Interesting Posts
- Typosquatting and Misspelled Domains Leading to Malicious HTA File
- New DLL Search Order Hijacking via System Processes on WinSxS Folder
- Searching a Tutorial on YouTube? Be Aware Where You Click (Malware Alert)
- QakBot and PikaBot Delivered via Digitally Signed MSI Windows Installers
- Fake "Copyright Infringement" Messages Lead to Facebook 2FA Bypass